[InfoSec MASHUP] 43/2024
J&J and Cisco Confirm Breaches; Widespread Exploitation of Fortinet Products; Russia Allegedly Trying to Influence US Elections; New Scoring System for AI Models on HF; Apple Offering up to $1M;
Welcome to the 33 new members from the last 30 days! This newsletter now has 1,582 subscribers.
Partners and Affiliates
🔐 NordVPN Black Friday & Cyber Monday
Campaign duration:
Black Friday: October 16 - December 2
Cyber Monday: December 2 - 10
Special offer: up to 74% off + 3 months extra, starting at $2.99 / 2.99 €
Breaches & Security Incidents
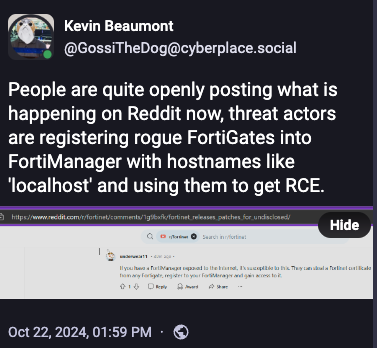
🇺🇸 🔓 Fortinet has not disclosed a critical vulnerability that attackers are actively exploiting to run malicious code on servers used by sensitive organizations. The company has not responded to inquiries or issued a public advisory about the issue. As a result, customers are left seeking information through social media discussions.
UPDATE: Fortinet has revealed a serious vulnerability in FortiManager, tracked as CVE-2024-47575, which has been exploited in attacks to steal sensitive information. The flaw allows attackers to execute commands without authentication, posing risks to managed devices and networks. Customers have expressed frustration over the way the vulnerability was disclosed, as some were not notified before it became public.
↳ Mandiant says new Fortinet flaw has been exploited since June
↳ Burning Zero Days: FortiJump FortiManager vulnerability used by nation state in espionage via MSPs
Cisco Confirms Security Incident After Hacker Offers to Sell Data
🇺🇸 🔓 Johnson & Johnson has reported a data breach affecting the personal information of over 3,200 individuals — The company discovered the breach in mid-August 2024 and is now investigating the incident. Impacted individuals are being offered free credit monitoring, but there is no evidence that their information has been misused.
📚 🔓 The Internet Archive was hacked while trying to restore services after a recent data breach that exposed information of 31 million users. Despite some services being restored, a new security incident involving compromised support tickets has raised more concerns. The Internet Archive is focusing on improving its cyber security to prevent future attacks.
➝ More breaches:
UnitedHealth says data of 100 million stolen in Change Healthcare hack
Penn State Settles for $1.25M Over Failure to Comply With DoD, NASA Cybersecurity Requirements
OnePoint Patient Care Data Breach Impacts Nearly 800,000 People
Insurance admin Landmark says data breach impacts 800,000 people
Henry Schein Revealed a Data Breach Affecting over 160,000 People
Cybercrime, Cyber Espionage, APT’s
🇺🇸 ⚖️ A Buffalo police detective, Terrance Michael Ciszek, has been charged for buying stolen credentials on a dark web marketplace called Genesis Market. He allegedly purchased 194 stolen account credentials and lied to the FBI about his activities. Ciszek faces up to 10 years in prison for possession of unauthorized access devices and making false statements.
🇨🇳 🎰 A sophisticated group of attackers, suspected to be APT41, targeted the gambling industry over nine months, using advanced techniques to steal sensitive information. They adapted their tools based on the security team's responses, employing unique malware and exploiting vulnerabilities to maintain access. Their methods included DLL hijacking and modifying system files to execute malicious code stealthily.
Government, Politics, and Privacy
🇺🇸 🤖 The White House has introduced new rules for US national security agencies to manage the use of artificial intelligence while addressing its risks. These guidelines aim to promote the responsible use of AI, ensuring it supports national security without violating civil rights or enabling misuse. Critics, however, worry that the policy may allow too much self-regulation by these agencies.
🇮🇪 💰 LinkedIn has been fined €310 million (about $356 million) by Ireland's Data Protection Commission for violating privacy laws related to its tracking ads business. The commission found that LinkedIn did not have valid legal justifications for processing user data and failed to inform users properly. LinkedIn must comply with GDPR regulations within three months following this significant penalty.
📱 📍 Babel Street offers a service called Location X that can track the locations of millions of phone users — Although it claims to limit access to government law enforcement, individuals can still obtain trials by claiming future government work. This raises concerns about privacy and the extent of location tracking.
🇺🇸 🔐 A task force of cyber experts has released recommendations for the next U.S. president to improve cybersecurity — Key priorities include resolving conflicting regulations, addressing the cyber workforce shortage, and collaborating with the private sector on critical infrastructure protection. The report emphasizes the need for bipartisan support and suggests strengthening cybersecurity agencies and education programs.
🇺🇸 💰 The SEC has fined four companies—Unisys, Avaya, Check Point, and Mimecast—for misleading statements about the impact of the SolarWinds hack in 2020 — The companies downplayed the breaches despite knowing that significant data was stolen. They will pay fines totalling nearly $7 million without admitting wrongdoing.
🇨🇾 Cyprus successfully stopped a digital attack aimed at its main government online portal — The attack was part of a series targeting state utilities and a Greek energy company, but it only disrupted the portal for a few minutes. No client information was compromised, and authorities are unsure who is behind the attacks.
🇺🇸 🇷🇺 The U.S. State Department is offering a reward of up to $10 million for information about the Russian media outlet Rybar, which is accused of spreading propaganda that could influence the U.S. presidential election. Rybar has over 1.3 million social media followers and promotes pro-Russian sentiments while inciting division within the U.S. The initiative is part of a broader effort to combat foreign interference in American democracy.
Partners and Affiliates
🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
Malware & Threats
🦠 🏦 New variants of the Grandoreiro banking malware are using advanced tactics to evade detection and continue targeting users worldwide. Despite some arrests within the group, the malware has evolved with features like mouse tracking and CAPTCHA barriers to bypass security measures. Grandoreiro can steal credentials from thousands of financial institutions and is primarily distributed through phishing emails.
🦠 🍎 A new macOS malware called NotLockBit can encrypt files and impersonates the LockBit ransomware. It targets both Windows and macOS systems, stealing data and preventing recovery. Security experts warn it is actively being developed and may pose a significant threat in the future.
Ransomware Gangs Use LockBit's Fame to Intimidate Victims in Latest Attacks
🦠 🇷🇺 A new phishing campaign targets Russian-speaking users using the Gophish framework to deliver remote access trojans like DarkCrystal RAT and PowerRAT — The attacks involve malicious documents or HTML links that require victims to enable macros or click links to trigger infections. Once activated, the malware can steal sensitive data and provide remote control of the infected system.
🦠 Two malware families, Bumblebee and Latrodectus, have returned with advanced phishing tactics after being disrupted by a law enforcement operation — These malware are designed to steal personal data and deploy additional malicious software through deceptive emails that appear legitimate. Recent campaigns utilize techniques such as malicious PDF attachments and ZIP files to deliver their payloads stealthily.
🦠 💸 Cybersecurity researchers at Phylum have found malicious npm packages that steal Ethereum private keys and allow remote access to victims' machines. These packages, designed to look like the legitimate ethers package, require developers to use them in their code for the attack to work. The authors of these malicious packages quickly removed them after their discovery.
AI, Crypto, Tech & Tools
🍎 💰 Apple is offering up to $1 million to security researchers who find vulnerabilities in its new Private Cloud Compute service — The company rewards researchers for reporting issues that could allow malicious access to user data. This initiative is part of Apple's ongoing bug bounty program to enhance security and protect customer privacy.
🐧 🇷🇺 A recent change in the Linux kernel removed several entries with Russian names or email addresses due to compliance with sanctions against Russia — This decision, made by maintainer Greg Kroah-Hartman, sparked debate among developers about its implications. To be added back, individuals must provide proof that they are not connected to sanctioned entities.
🤖 🎯 Endor Labs has introduced a new scoring system to assess the security of open source AI models from Hugging Face, similar to how they evaluate open source software. This system helps identify potential risks, including malicious code and vulnerabilities inherited from base models. While it doesn't solve compliance issues with AI regulations, it provides a trustworthy starting point for developers to gauge the safety of AI models.
🤖 ✍🏻 Google has introduced SynthID, a technology that adds invisible watermarks to AI-generated content to help identify its authenticity. This system works with text, images, audio, and video, and the watermarks remain detectable even after modifications. SynthID is currently in beta and aims to prevent the misuse of AI-generated content, such as deepfakes and misinformation.
🛠️ 🦠 Avast has released a free tool to help victims recover files encrypted by the Mallox ransomware, which has been active since 2021. The decryptor works for files encrypted in 2023 or early 2024 and targets specific file extensions. However, it cannot decrypt files affected by later versions of Mallox after a cryptographic flaw was fixed in March 2024.
🤖 Researchers have developed a technique called "Deceptive Delight" that can trick large language models into generating harmful content by mixing unsafe instructions with benign ones in conversations. This method has a success rate of about 64.6% and highlights the models' weaknesses in processing context. To combat this risk, experts recommend using strong content filtering and improving the models' resilience against such attacks.
Deceptive Delight: Jailbreak LLMs Through Camouflage and Distraction
Vulnerabilities, Research, and Threat Intelligence
Atlassian Patches Vulnerabilities in Bitbucket, Confluence, Jira
Cisco Patches Vulnerability Exploited in Large-Scale Brute-Force Campaign
Nvidia Patches High-Severity Flaws in Windows, Linux Graphics Drivers
VMware Releases vCenter Server Update to Fix Critical RCE Vulnerability
White Hat Hackers Earn $500,000 on First Day of Pwn2Own Ireland 2024
⚠️ CISA has warned that a recently patched vulnerability in Microsoft SharePoint Server, known as CVE-2024-38094, is being actively exploited — This flaw allows authenticated attackers with high-level permissions to run arbitrary code on the server. CISA urges all organizations to quickly apply the necessary security updates to protect against these attacks.
🔓 Google's Threat Analysis Group has warned about a zero-day vulnerability in Samsung's mobile processors that allows attackers to execute arbitrary code on affected Android devices. The flaw, tracked as CVE-2024-44068, has been exploited in the wild and is linked to a use-after-free bug in the m2m scaler driver. Samsung has patched this issue in its October 2024 security updates, but researchers caution that the exploit remains a risk.
🔓 📨 Hackers are exploiting a flaw in Roundcube Webmail to steal email credentials from government organizations in the CIS region — They use emails with hidden malicious content to trick users into giving up their login information. System administrators are urged to update Roundcube to the latest version to protect against this vulnerability.
🔓 ☁️ Several popular end-to-end encrypted cloud storage services, including Sync, pCloud, Icedrive, Seafile, and Tresorit, have serious security vulnerabilities that could expose user data. Researchers found that these flaws allow attackers to manipulate files and access sensitive information, contradicting the platforms' promises of security. While some companies have started addressing these issues, others have not responded or chosen not to fix them.
🪳 💰 Google Cloud has launched a new Vulnerability Reward Program (VRP), offering up to $101,010 for reporting security flaws in over 460 of its products and services. Researchers will work directly with Google Cloud security engineers for quicker bug assessments and improved rewards. To qualify for the highest rewards, participants must provide detailed reports showing the security impact of the vulnerabilities they find.
ICS, OT & IoT
🔓 Germany's CERT@VDE has warned about critical vulnerabilities in industrial routers, including the mbNET.mini, which can be exploited by remote hackers to take control of devices. Vendors have released patches to address these issues, but concerns remain about the overall security of such devices. Experts urge manufacturers to conduct regular security testing to prevent similar risks in the future.