Originally posted on May 22, 2024, but after the recent news that the U.S. will not renew funding for the CVE program, I thought I’d share this one again.
On Wednesday, April 16, funding for MITRE to develop, operate, and modernize the Common Vulnerabilities and Exposures Program and related programs, such as the Common Weakness Enumeration Program, will expire,
After finishing reading Chris Hughes and Nikki Robinson’s excellent book titled “Effective Vulnerability Management: Managing Risk in the Vulnerable Digital Ecosystem”, I thought I’d write a piece on the less(er) known community-developed Common Weakness Enumeration (CWE™) project and why it’s important to all. Let’s go!
Introduction
In today's fast-paced software development environment, ensuring robust security and quality is more critical than ever. One powerful tool that can significantly enhance both is the Common Weakness Enumeration (CWE).
What is CWE?
Let’s look at the definition from the official CWE website:
Common Weakness Enumeration (CWE™) is a community-developed list of common software and hardware weaknesses. A “weakness” is a condition in a software, firmware, hardware, or service component that, under certain circumstances, could contribute to the introduction of vulnerabilities. The CWE List and associated classification taxonomy identify and describe weaknesses in terms of CWEs.
Knowing the weaknesses that result in vulnerabilities means software developers, hardware designers, and security architects can eliminate them before deployment, when it is much easier and cheaper to do so.
CVE (Common Vulnerabilities and Exposures) and CWE (Common Weakness Enumeration) serve different purposes in the realm of cybersecurity. CVE lists specific vulnerabilities, while CWE categorizes types of weaknesses that can lead to vulnerabilities.
By integrating CWE into the Software Development Life Cycle (SDLC), developers can proactively identify and mitigate vulnerabilities, standardize their security practices, improve code quality, achieve compliance, and reduce costs associated with fixing post-deployment issues. This blog post will delve into the top five reasons why every developer should make CWE a cornerstone of their SDLC.
Today we'll cover:
Let’s dive right into it 🤿
1. Improved Security Posture
Incorporating CWE into the SDLC significantly enhances a developer's ability to create secure applications. Here's why:
Identifies and Mitigates Common Vulnerabilities Early
One of the primary benefits of using CWE is its ability to help developers identify and mitigate common vulnerabilities early in the development process. By referencing a comprehensive list of known weaknesses, developers can anticipate and address security issues before they become embedded in the codebase. This proactive approach not only strengthens the application's security but also saves time and resources by reducing the need for (financially) extensive post-deployment fixes.
It also as a fortunate side effect that it spreads security awareness to the developer community early in the cycle without overwhelming teams with “fixes”.
Weakness Weaponization
Many security breaches can be traced back to common vulnerabilities that are well-documented in CWE. Understanding the relationship between these weaknesses and real-world exploitations allows developers to prioritize addressing the most critical issues. By focusing on vulnerabilities that are frequently weaponized by attackers, developers can significantly reduce the risk of successful exploits and subsequent data breaches.
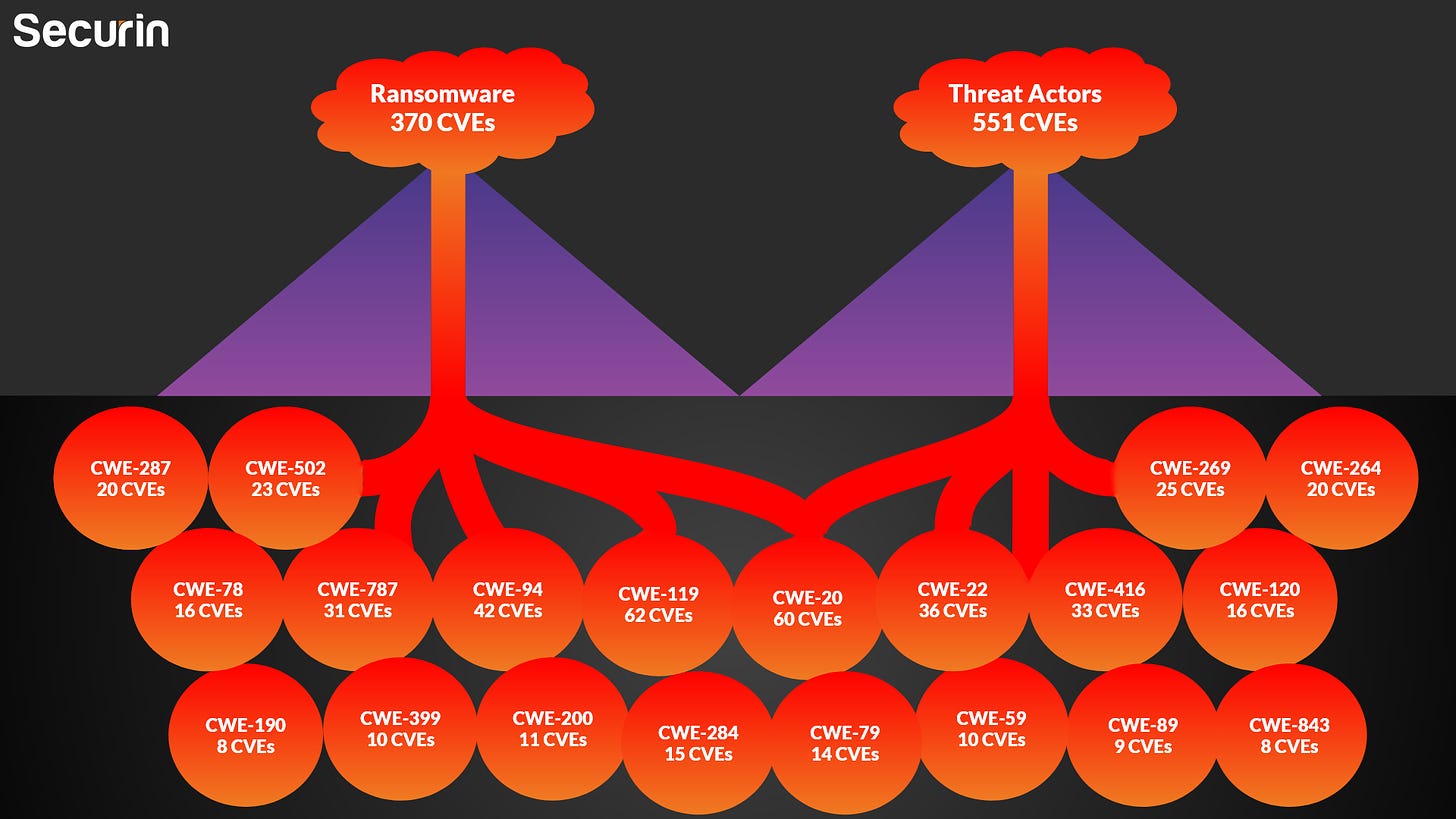
Weaknesses Fuelling Threat Actor and Ransomware Eruptions / securin.io
Context is Everything
The context in which a vulnerability exists is crucial to understanding its potential impact. CWE provides detailed descriptions and examples of how weaknesses can be exploited, giving developers a clearer understanding of the risks involved. This contextual information enables developers to implement more effective mitigation strategies tailored to their specific application environment.
By incorporating CWE into the SDLC, developers can significantly improve their security posture, making their applications more resilient against potential attacks. This proactive approach not only helps in building robust software but also instills a culture of security awareness throughout the development team.
2. Standardization
Incorporating CWE into the SDLC fosters a standardized approach to security, which has significant benefits for development teams.
Provides a Common Language for Discussing Security Issues
CWE offers a universal language for identifying and describing software weaknesses, which improves communication among team members. When developers, security professionals, and stakeholders use the same terminology, it eliminates confusion and ensures that everyone has a clear understanding of the security issues at hand. This common framework facilitates more effective collaboration, enabling teams to work together seamlessly to identify, prioritize, and address vulnerabilities.
By standardizing the way security issues are discussed and documented, CWE helps streamline the development process, making it easier to integrate security into every stage of the SDLC. This shared understanding is crucial for fostering a security-first mindset across the organization, ultimately leading to the development of more secure and reliable software.
The relationship between CWE and the National Vulnerability Database (NVD) is that CWE provides a standardized vocabulary and structure for describing vulnerabilities, which the NVD uses to classify and catalog vulnerabilities in its database. When a vulnerability is added to the NVD, it is typically mapped to one or more CWE entries to provide a standardized description of the weakness. This allows security professionals to search and analyze vulnerabilities in a consistent and structured manner, making it easier to understand and address security risks.
3. Enhanced Code Quality
By incorporating CWE into the SDLC, developers not only produce more secure code but also foster a culture of collaboration, continuous learning, and proactive risk management. This approach leads to enhanced code quality, reduced vulnerabilities, and ultimately, more robust and reliable software products. Here’s why:
Encourages Best Practices in Coding
Adherence to Standards: Integrating CWE into the SDLC encourages developers to adhere to coding standards and best practices, fostering cleaner, more maintainable code.
Code Reviews and Collaboration: Developers are prompted to conduct thorough code reviews, sharing insights and best practices to improve overall code quality and reduce the likelihood of vulnerabilities.
Secure by Design
Shift Left Security: Incorporating CWE promotes a "security-first" mindset, where security considerations are integrated into the design and implementation phases of development.
Proactive Risk Mitigation: Developers proactively identify and address potential vulnerabilities during the development process, reducing the need for reactive security measures post-deployment.
What Developers Shall Do
Training and Education: Developers should undergo training on secure coding practices and familiarize themselves with common vulnerabilities listed in CWE.
Code Analysis Tools: Utilize automated code analysis tools that leverage CWE to identify and remediate vulnerabilities early in the development cycle. Even better these analysis tools could be embedded in the developers IDE.
Collaboration with Security Teams: Foster collaboration between developers and security teams to ensure a shared understanding of security requirements and effective mitigation strategies. Ideally in a DevOps world, these would be part of the same team with security trained developers taking the role of AppSec champions to facilitate this collaboration.
GenAI Assistance for Threat Modeling
Automated Threat Modeling: AI-driven tools, can assist developers in conducting threat modeling exercises based on CWE entries, identifying potential threats and vulnerabilities in software design and architecture. GenAI can provide insights into potential attack vectors and recommend mitigation strategies, empowering developers to proactively address security concerns during the design phase, as highlighted in the below Secure Software Development Life Cycle (SSDLC) diagram:
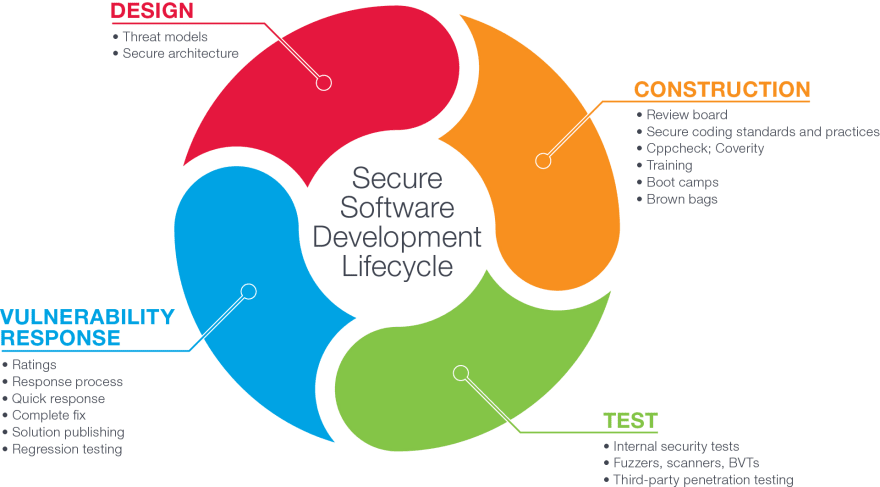
SSDLC process diagram. Source: dev.to
See following example of threat model finding:
Operator is deployed and Pod is running but not being used at present. Refer to Kubernetes Operators: good security practices
Associated CWE
4. Compliance
Incorporating the Common Weakness Enumeration (CWE) into the Secure Development Life Cycle (SDLC) is paramount for organizations striving to ensure compliance with industry standards and regulatory requirements for developing secure software. Here's why:
Alignment with Regulatory Frameworks: Many industry standards and regulatory frameworks, such as PCI DSS, HIPAA, GDPR, and others, mandate the implementation of secure development practices. Incorporating CWE aligns with these requirements by demonstrating a proactive approach to identifying and mitigating software vulnerabilities, which is essential for compliance.
Proactive Vulnerability Management: Integrating CWE into the SDLC enables organizations to proactively address vulnerabilities early in the development process. By identifying and mitigating weaknesses before they manifest into security threats, organizations can significantly reduce the risk of security breaches and data compromises.
Strategic Security Investments: Leveraging CWE in the SDLC signifies a strategic investment in enhancing the security posture of software products. This proactive stance not only strengthens defenses against potential cyber threats but also fosters trust and confidence among customers, partners, and regulatory bodies.
Evidence of Secure Development Practices: Incorporating CWE into the SDLC provides tangible evidence of an organization's commitment to secure development practices. This can be invaluable during compliance audits and regulatory assessments, demonstrating due diligence in mitigating software vulnerabilities and protecting sensitive data.
Integrating the Common Weakness Enumeration (CWE) into the Secure Development Life Cycle (SDLC) not only strengthens software security but also facilitates compliance with industry standards and regulatory requirements. By adopting a proactive approach to vulnerability management and embracing a culture of continuous improvement, organizations can enhance their security posture, mitigate risks, and build trust among stakeholders.
5. Cost Efficiency
Integrating the Common Weakness Enumeration (CWE) into the Secure Development Life Cycle (SDLC) cuts costs by catching vulnerabilities early. Here's how:
Early Detection: CWE helps find and fix vulnerabilities during development, saving costs compared to post-deployment fixes.
Lower Remediation Costs: Fixing issues during development is cheaper than after deployment, which involves extensive rework and testing.
Efficient Resource Allocation: CWE streamlines development by prioritizing vulnerability fixes, optimizing resources.
Preventing Incidents: Catching vulnerabilities early prevents costly security incidents and data breaches.
Optimized Testing: Focused testing based on CWE reduces testing iterations and costly rework.
Faster Deployment: Addressing vulnerabilities early speeds up deployment, reducing time-to-market delays and boosting revenue.
Enhanced Reliability: Delivering more secure products increases customer satisfaction, reducing support costs.
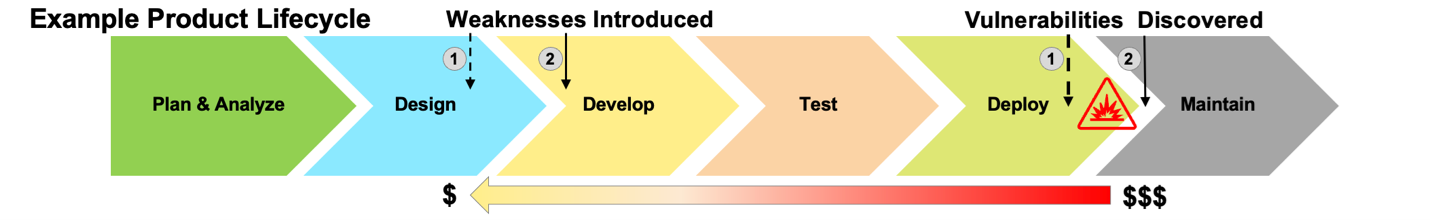
The Systems Sciences Institute at IBM has reported that the cost to fix an error found after product release was four to five times as much as one uncovered during design, and up to 100 times more than one identified in the maintenance phase:
By incorporating CWE into the SDLC, organizations save money by proactively addressing vulnerabilities, fostering a secure and efficient development process.
Conclusion
Incorporating CWE into the SDLC is essential for modern software development. It enhances security by identifying and addressing common vulnerabilities early, standardizes security practices, improves code quality, ensures compliance with industry standards, and reduces costs associated with fixing issues post-deployment. By adopting CWE, developers can create more secure, reliable, and efficient software.
➝ Start integrating CWE into your development process today to build safer and more robust applications. Your future self—and your users—will thank you for it.
Resources
📚 Chris Hughes and Nikki Robinson’s excellent book:Effective Vulnerability Management: Managing Risk in the Vulnerable Digital Ecosystem

💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.