[InfoSec MASHUP] 02/2025
Tenable CEO Amit Yoran Passed Away; Green Bay Packers' Online Store Hacked; White House Cyber Trust Mark Program; Facebook and Instagram Accounts Deletion Surge; New US Cybersecurity Exec. Order;
Welcome to the 23 new members from the last 30 days! This newsletter now has 1,627 subscribers.
Partners and Affiliates
🔐 NordVPN - Save up to 75% + 3 Extra Months!
Breaches & Security Incidents
Washington state sues T-Mobile over 2021 data breach security failures
🇺🇸 🏫 PowerSchool has confirmed a cybersecurity breach that exposed personal information of students and teachers from K-12 schools using its platform. The attacker accessed the system using stolen credentials and exported sensitive data, including names, addresses, and possibly Social Security numbers. PowerSchool is working with cybersecurity experts to investigate the incident and has offered credit monitoring services to affected individuals.
✈️ The International Civil Aviation Organization (ICAO) is investigating a cybersecurity incident involving a potential data breach. A hacker claimed to have stolen 42,000 documents, including personal information of ICAO employees. The organization has not provided further comments on the situation.
🇯🇵 Casio confirmed that hackers stole personal data from nearly 8,500 people during a ransomware attack in October. The breach affected around 6,500 employees and over 1,900 business partners, but no credit card information was compromised. Casio stated they did not negotiate with the hackers and have restored most of their services.
🇺🇸 🏈 The Green Bay Packers' online store was hacked, allowing a third party to steal customers' personal and payment information. After discovering the breach on October 23, 2024, the team disabled payment options and hired cybersecurity experts to investigate. Affected customers are being offered three years of credit monitoring and should watch for any fraudulent activity.
🇨🇳 🇺🇸 Chinese hackers from the group called Salt Typhoon have breached several U.S. telecommunications networks, including Charter and Windstream. They gained access to sensitive information like text messages and phone calls. The U.S. government is taking steps to strengthen telecom security and may ban certain Chinese telecom operations.
🇫🇷 Atos, a French tech company, denied claims from the Space Bears ransomware group that they hacked its database — The company stated that there was no evidence of a breach or ransom demand, and any data mentioned was from an external third party, not managed by Atos. Atos emphasized its strong cybersecurity measures and expert team working to protect its systems.
➝ More breaches:
Medical billing firm Medusind discloses breach affecting 360,000 people
Largest US addiction treatment provider notifies patients of data breach
🔊 Interested in Reaching a Cybersecurity Audience?
Amplify your brand’s presence by sponsoring the InfoSec MASHUP newsletter!
Reach dedicated readers in the cybersecurity field with each issue! Contact us to explore sponsorship opportunities.
Cybercrime, Cyber Espionage, APT’s
⚖️ Microsoft is suing a group of cybercriminals for using stolen credentials to bypass safety measures in its Azure OpenAI services. The criminals allegedly generated harmful content by exploiting the system and selling access to it online. Microsoft has obtained a court order to seize the domain associated with these activities to gather evidence and disrupt their operations.
🇺🇦 🇷🇺 Ukrainian hackers claimed responsibility for a cyberattack on the Russian internet provider Nodex, which caused a total internet outage for its customers. Nodex confirmed that its network was compromised and is currently working to restore its systems. The attack was attributed to the Ukrainian Cyber Alliance, a group that has targeted Russian entities since the invasion of Ukraine in 2022.
Government, Politics, and Privacy
🇺🇸 👨🏻⚖️ The Biden administration plans to release a new cybersecurity executive order to improve federal cyber practices and software procurement. The order aims to enhance security measures, such as requiring encryption for communications and implementing advanced detection tools. It also emphasizes the need for agencies to adopt post-quantum cryptography to protect against future cyber threats.
🇺🇸 👀 A lawyer is seeking to identify the key witness, known as Afgoo, who created the encrypted chat app Anom, which the FBI used to intercept messages from organized criminals. This witness may testify in court, and their identity will be revealed as part of the discovery process. The case, involving numerous criminal syndicates worldwide, is set to go to trial in March.
🇮🇳 The Indian government has proposed new Digital Personal Data Protection (DPDP) Rules to give citizens more control over their personal data. These rules require companies to provide clear information about data processing, allow data erasure, and implement strong cybersecurity measures. Organizations that fail to comply with these regulations could face hefty fines of up to ₹250 crore (about $30 million).
🇪🇺 💰 The EU General Court has fined the European Commission €400 for violating its own data privacy laws — A German citizen's personal data was improperly shared with U.S. companies when he registered for a conference.
🇺🇸 Telegram has shared user data with U.S. law enforcement in response to 900 requests, affecting over 2,200 users. This marks a significant increase from past years, as Telegram updated its policy to include various crimes beyond terrorism. The change comes after pressure from authorities and the arrest of Telegram's founder for alleged cybercrime-related charges.
🇬🇧 The U.K. plans to make creating sexually explicit deepfake content a criminal offense — This move aims to address online abuse, particularly against women, and builds on existing laws that already penalize sharing such content. The new rules will be included in an upcoming Crime and Policing Bill.
🇺🇸 🇨🇳 The U.S. cybersecurity agency CISA stated there is no evidence of a wider hack beyond the Treasury Department after a cyberattack linked to Chinese hackers. The Treasury confirmed the breach, revealing that hackers accessed employee workstations and unclassified documents. CISA is actively monitoring the situation and coordinating with federal authorities for a response.
Partners and Affiliates
🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
Malware & Threats
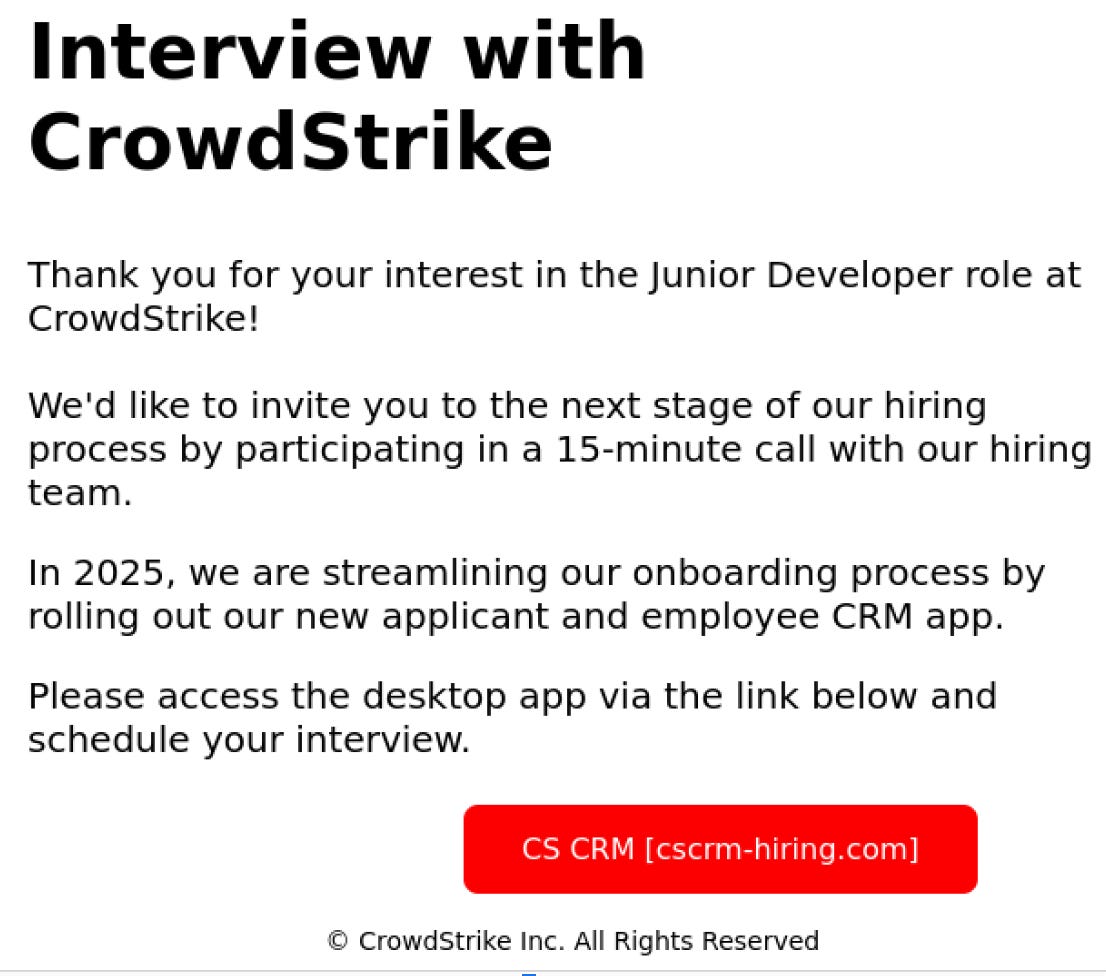
🎣 👨🏻💻 CrowdStrike is warning job seekers about fake job offer emails that contain links to download a cryptocurrency miner. The phishing emails pretend to be from CrowdStrike and direct candidates to a fake website to download an application. Job seekers should verify email addresses and avoid downloading files during the recruitment process.
🦠 🍎 Researchers have discovered a new version of Banshee Stealer, a macOS malware that can bypass antivirus software by using advanced encryption. This malware is spread through phishing sites and fake software downloads, targeting over 100 million macOS users. The updated version has removed restrictions on language settings, allowing it to target a wider range of victims.
🦠 New versions of the Eagerbee malware are targeting government organizations and ISPs in the Middle East, linked to a group called 'CoughingDown.' The malware can collect information, manage files, and enable remote access on infected systems. Experts advise organizations to patch vulnerabilities and monitor for signs of this threat.
🦠 💬 FireScam is a dangerous Android malware that pretends to be a premium version of the Telegram app to steal personal data and control devices. It is distributed through a fake app store site and uses various techniques to avoid detection while monitoring user activities. Once installed, it can access sensitive information, including messages and call logs, and can receive remote commands to maintain control over the infected device.

AI, Crypto, Tech & Tools
🤖 © Mark Zuckerberg reportedly allowed Meta's Llama AI team to use a data set of pirated ebooks for training, leading to a lawsuit claiming copyright infringement. Plaintiffs, including authors Sarah Silverman and Ta-Nehisi Coates, allege that Meta not only used this illegal data but also tried to hide copyright information from it. The case raises serious questions about Meta's practices and its defense of fair use in developing AI models.
⌫ Google searches for deleting Facebook and Instagram accounts surged after Meta announced it will end its fact-checking and content moderation policies. Many users are concerned that this change will lead to increased hate speech and misinformation on the platforms. In response, interest in alternatives like Bluesky and Mastodon has also dramatically increased.
Vulnerabilities, Research, and Threat Intelligence
Android patches several vulnerabilities in first security update of 2025
CISA warns of critical Oracle, Mitel flaws exploited in attacks
Ivanti Connect Secure zero-day exploited by attackers (CVE-2025-0282)
SonicWall urges admins to patch exploitable SSLVPN bug immediately
Facebook awards researcher $100,000 for finding bug that granted internal access
🪳 📱 A Google Project Zero researcher found a serious security flaw in Samsung smartphones that could let attackers execute code without user interaction. This vulnerability affects devices running Android versions 12, 13, and 14 and has been patched by Samsung. The issue arises when audio messages are decoded, allowing specially crafted files to crash the media codec process.
📉 IBM's latest Cloud Threat Landscape Report reveals a 20.4% drop in mentions of Software-as-a-Service (SaaS) platforms on dark web marketplaces. This decline is attributed to improved cybersecurity measures and the takedown of the Raccoon Stealer malware, which previously dominated credential theft. Experts warn organizations to remain vigilant and continue strengthening their security practices despite this positive trend.
🚪 Malicious hackers also struggle with shadow IT, leaving behind old backdoors that can be exploited. Researchers at watchTowr Labs found and hijacked these backdoors, gaining access to thousands of compromised systems. This shows that even attackers can make mistakes in managing their abandoned infrastructure.
🚗 Security researcher Matt Brown found that some Motorola license plate cameras are streaming live video and data to the public internet, exposing sensitive information. He created a tool to track cars in real-time using this unprotected data, raising concerns about privacy risks associated with automated license plate readers (ALPRs). Motorola is working on a firmware update to improve security, but many vulnerabilities remain.
🪳 ☁️ Amazon's AWS Neuron SDK has repeatedly (3x) introduced a security vulnerability that allows for remote code execution due to flawed installation instructions. Despite being notified of the issue multiple times, Amazon has not permanently fixed the problem and continues to expose users to risks. This situation serves as a reminder to always verify the security of code, even from reputable sources.
🪳 🔓 A serious security flaw in the Nuclei vulnerability scanner allows attackers to bypass signature checks and execute malicious code. This vulnerability, tracked as CVE-2024-43405, affects all versions of Nuclei after 3.0.0 and is caused by issues with how newline characters are processed. ProjectDiscovery has released a fix in version 3.3.2 to address this vulnerability.
ICS, OT & IoT
🇺🇸 The U.S. Cyber Trust Mark is a new voluntary program to help consumers assess the cybersecurity of internet-connected devices — Manufacturers can earn this label by meeting specific security standards set by the U.S. National Institute of Standards and Technology. The program will launch in 2025, making it easier for consumers to find secure smart home products.
🪳 🔓 Moxa has reported critical vulnerabilities in their cellular and secure routers that can allow attackers to gain root access or execute unauthorized commands. Two high-severity flaws were identified, with one requiring user authentication and the other being exploitable remotely without authentication. Moxa recommends immediate action, such as applying patches or limiting network exposure, to protect affected devices.