We now have {{active_subscriber_count}} active subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
🇰🇷 South Korean conglomerate Kyowon confirmed a ransomware attack that stole data on January 1. About 9.6 million accounts (5.5 million people) may be affected and roughly 600 of 800 servers were hit. Kyowon is investigating with authorities and working to restore services.
🇧🇪 Belgian hospital AZ Monica shut down all servers after a cyberattack and canceled scheduled procedures. Emergency services and intensive care are largely offline, and seven critical patients were transferred out. Authorities are investigating and the hospital says it is monitoring the situation and will provide updates.
🇺🇸 JPMorgan Chase told Maine authorities that 659 investors were affected by a data breach at law firm Fried Frank. Stolen files included names, contact details, account numbers, SSNs, and passport or ID numbers. Fried Frank says it contained the incident, hired experts, and believes exposed data is unlikely to be misused.
🇪🇸 🪫 Spanish utility Endesa says hackers accessed customer contract data at its Energía XXI unit, including names, contact details, ID numbers, contract and payment info. The company blocked compromised accounts, notified authorities and affected customers, and found no evidence yet of fraudulent use. Threat actors claim to be selling about 20 million stolen records.
🇺🇸 🏝 Hackers stole social security numbers and other data from a University of Hawaii Cancer Center study in August. UH waited months to report the breach, gave few details, and won’t say whether it paid the hackers. The university is notifying participants, offering credit monitoring, and has tightened security.
🔓 The BreachForums hacking site had its user database leaked, exposing about 324,000 accounts. The leak included a passphrase-protected PGP key and a MyBB users table with IPs and registration data. Some records show public IPs that could aid law enforcement and pose OPSEC risks for users.
→ More breaches:
🔗 Partners and Affiliates
With its user-friendly interface, robust security features, and commitment to privacy, NordVPN continues to be a popular choice for individuals seeking online protection and unrestricted internet access.
Special Offer: get up to 73% off with a 2-year plan!
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
❌ Microsoft and international law enforcement seized the infrastructure of RedVDS, a cybercrime marketplace that rented disposable virtual computers to criminals. RedVDS enabled widespread phishing, account takeovers, and at least $40 million in U.S. fraud losses, affecting hundreds of thousands of accounts. The takedown disrupted the service and aims to help identify those behind it.
🇳🇱 ⚖ A Dutch man was sentenced to seven years for hacking port systems in Rotterdam, Barendrecht and Antwerp to help smuggle drugs and for attempted extortion. His appeal failed despite claims that evidence from Sky ECC messages was unlawfully obtained. The court kept most convictions but dropped one drug charge about importing 5,000 kg of cocaine.
🇪🇸 🇪🇺 Europol and Spanish police arrested 34 people linked to the Black Axe criminal group in raids across Spain. The group is accused of cyber-enabled fraud, drug and human trafficking, kidnapping, and other violent crimes that caused over €5.9 million in losses. Authorities also froze bank accounts and seized cash and assets while investigations continue.
🇺🇸 ⚖ A 24-year-old man from Tennessee is expected to plead guilty to hacking the U.S. Supreme Court’s electronic filing system. Prosecutors say he accessed the system without authorization on 25 days between August and October 2023. Details about what was taken or how are not yet public.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests (and don’t forget to star the project); Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇮🇷 🔌 Iran has cut off internet and phone access nationwide for more than a week, leaving about 92 million people offline. The shutdown is one of Iran’s longest and comes amid large anti-government protests and a violent crackdown. Some services and a few Starlink users have limited access, while international tensions and evacuations rise.
🇺🇸 🧑⚖ A federal judge dismissed the Trump administration’s lawsuit trying to force California to hand over unredacted voter data. The court said the request was unprecedented, violated privacy, and fell outside the civil rights laws cited by DOJ. Voting experts and civil rights groups praised the ruling as a win for voter privacy and state election authority.
🇺🇸 🧑⚖ A judge in Austin dismissed a securities class action against CrowdStrike over the July 2024 outage, finding shareholders did not prove intentional fraud. Millions of Windows devices crashed after a bad update, causing major disruptions at airports, banks, media outlets, and hospitals. The dismissal is a win for CrowdStrike, but Delta’s separate $500M lawsuit over the outage and other related claims remain.
🇺🇸 🪖 President Trump's pick for cyber chief told lawmakers he will review whether one leader should run both U.S. Cyber Command and the NSA. He said he will assess the risks and benefits if he is confirmed. He did not commit to keeping the dual-hat arrangement.
🇺🇸 President Trump re-nominated Sean Plankey to lead CISA — Plankey’s earlier nomination stalled in the Senate due to holds by senators over unrelated disputes. The re-nomination signals the administration still wants him for the job.
📆 🇪🇺 The EU is reviewing Google’s $32 billion acquisition of cloud security firm Wiz and must make a preliminary decision by February 10, 2026. Google says Wiz will keep supporting other cloud platforms, but critics worry the deal could harm Wiz’s neutrality and give Google competitive visibility. If the EU needs more study, it may open a longer Phase II probe.
🔗 Partners and Affiliates

🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
🦠 MALWARE & THREATS
🐛 🍪 Researchers found an XSS flaw in the StealC malware control panel that let them view and hijack operator sessions. They used it to gather hardware and location details and recover session cookies, exposing an operator in Ukraine. The disclosure aims to disrupt StealC's malware-as-a-service operations as its use has spiked.
👀 ❌ Researchers found Predator spyware can report why an infection failed using error codes. Error code 304 tells operators the target is running security or analysis tools. Predator also detects tools like netstat and hides crash logs to avoid detection.
🇺🇦 Between October and December 2025, Ukrainian defense officials were targeted with charity-themed messages that delivered the PluggyApe backdoor. CERT-UA links the campaign to the Russian group Laundry Bear (Void Blizzard) and says attackers used fake charity sites, messaging apps, and PIF executables to infect victims. PluggyApe steals system data, keeps persistence via the Windows Registry, and retrieves commands from online sources while attackers increasingly exploit mobile devices and legitimate accounts.
🐧 Security researchers found a new modular Linux malware framework called VoidLink that targets cloud and container environments. It can detect Kubernetes/Docker, gather cloud metadata, load plugins and use rootkits and covert channels to stay hidden. No active infections are confirmed, and analysts say it appears professionally developed, likely for sale or custom use.
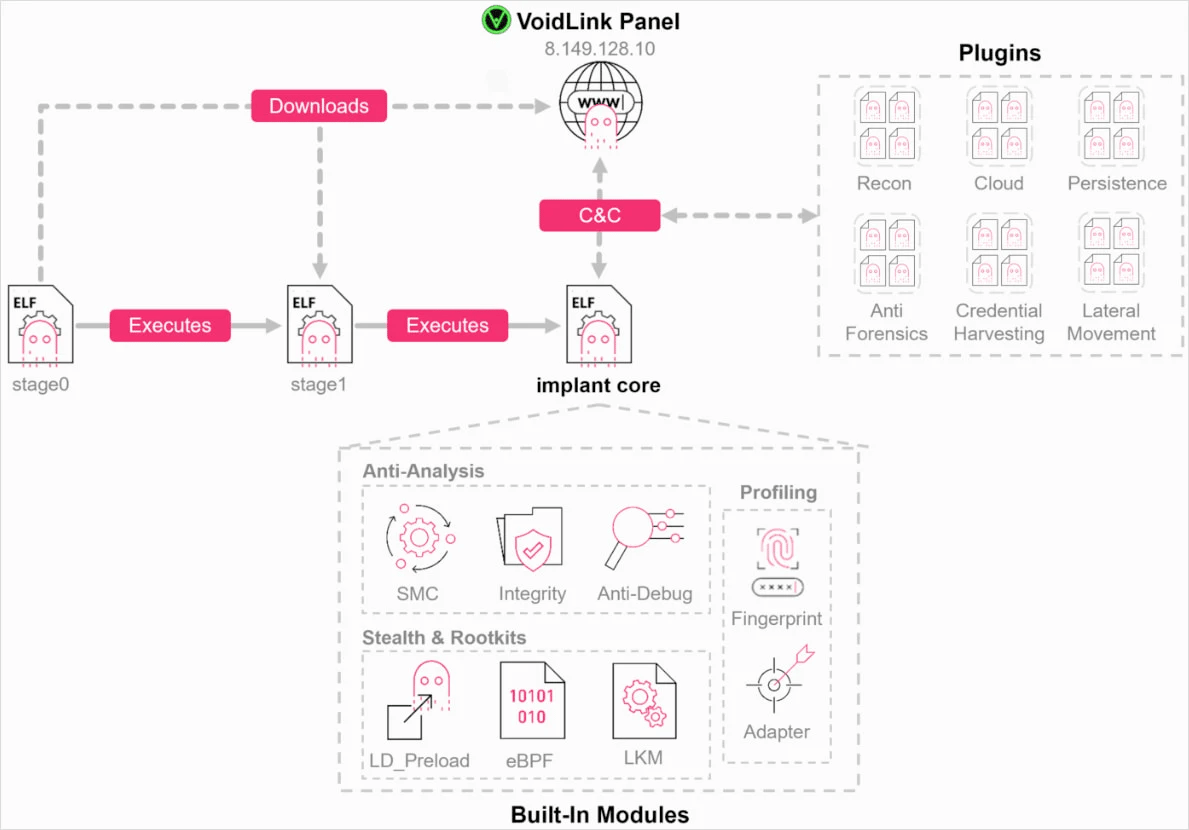
Figure: VoidLink High Level Overview/checkpoint.com
🤖 🧰 AI, CRYPTO, TECH & TOOLS
🆕 Former CISA director Jen Easterly is the new CEO of the RSA Conference — She will lead the conference, innovation programs, education, and membership efforts. Easterly brings deep cybersecurity experience and plans to expand RSAC’s global reach and focus on secure-by-design and AI.
🔓 Researchers found a new "Reprompt" attack that used a single malicious link to make Microsoft Copilot leak user data. The attack tricked Copilot into repeating requests and fetching hidden instructions, letting an attacker siphon data continuously even after the chat closed. Microsoft fixed the issue and says enterprise Microsoft 365 Copilot customers are not affected.
🔗 Meta fixed a bug that let outsiders send Instagram password reset requests and said there was no breach. Separate leaked data for about 17.5 million accounts surfaced, but experts say it matches a 2022 scrape and is unrelated to the reset issue. No passwords appear compromised.
🐛 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
🎧 Researchers found a flaw called WhisperPair that can let attackers take over Google Fast Pair Bluetooth devices — The bug affects many models from makers like Sony, Nothing, JBL, OnePlus, and Google. An attacker can hijack headphones quickly (about 10 seconds) from up to 14 meters away.
🩸 MongoBleed (CVE-2025-14847) is a critical, unauthenticated MongoDB memory-leak vulnerability in zlib-compressed messages that can expose sensitive secrets. About 146,000 internet-facing MongoDB instances were found vulnerable and active exploitation was observed. Mitigations like blocking TCP/27017 can help detect and reduce risk.
🛜 Researchers found a Broadcom Wi‑Fi chipset flaw that lets unauthenticated attackers disable 5 GHz networks with a single crafted frame. The bug bypasses WPA2/WPA3, can be repeated indefinitely, and affects many routers; 2.4 GHz and wired Ethernet are not impacted. Broadcom issued a patch and Asus released updates, but other affected vendors are unclear.
🛰️ ICS, OT & IoT
📆 🩹 ICS Patch Tuesday — Major industrial vendors including Siemens, Schneider Electric, Phoenix Contact, and Aveva released Patch Tuesday advisories fixing multiple high- and critical-severity vulnerabilities in ICS/OT products. The flaws include authentication bypass, remote code execution, privilege escalation, command injection, and issues in third-party components. Other vendors and agencies, including Honeywell, ABB, and CISA, also published related security notices.
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Enjoying our newsletter? Forward it to a colleague—
it’s one of the best ways to support us.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.



