We’ve Moved! 🚀
Exciting changes ahead! We’ve officially moved from Substack to Beehiiv to bring you an even better reading experience. Expect the same great content—just with a sleeker design, faster delivery, and new features to enhance your experience. If you're receiving this, you're already on board! Thanks for sticking with us—big things ahead! 🎉
🔓 BREACHES & SECURITY INCIDENTS
🇧🇪 🇨🇳 Belgian federal prosecutors are investigating a major cybersecurity breach at the State Security Service, where Chinese hackers accessed email systems for nearly two years. Personal information of almost half of the agency's employees may have been compromised, but classified data was reportedly safe. The agency has stopped using Barracuda solutions and is enhancing its data protection measures.
🇦🇺 Hackers have published sensitive data from IVF patients after attacking Genea, a major fertility provider in Australia. The stolen information includes medical records and identification documents, but there’s no evidence that financial details were compromised. Genea is currently investigating the breach and has taken steps to restore its systems.
🇷🇺 Russia's National Coordination Center for Computer Incidents is warning financial organizations about a recent hack at LANIT, a major IT service provider. The breach could affect companies like LLC LANTER and LLC LAN ATMservice, which specialize in banking technology. Authorities recommend that affected organizations change their passwords and enhance security measures.
🇺🇸 DISA Global Solutions, a company that provides employee screening services, reported a data breach affecting over 3.3 million people — The breach included sensitive information like Social Security numbers and financial details. DISA discovered the hacker had accessed their network in February 2024 but did not notify affected individuals until April.
🇫🇷 A hacker named Rey claims to have stolen thousands of documents from Orange Group, a major French telecommunications company, after breaking into their systems. The stolen data includes 380,000 email addresses and sensitive employee and customer information, primarily from Orange's Romanian branch. Orange has confirmed the breach and is investigating the incident while taking steps to protect affected data.
💸 Cryptocurrency exchange Bybit was hacked, resulting in the theft of about $1.5 billion worth of digital currency — The company assured users that their funds are safe and that it can cover the loss, despite the attack. A surge in withdrawal requests followed the news, but Bybit remains solvent and has enough assets to protect user holdings.
🔗 Partners and Affiliates
🔐 NordVPN Birthday Campaign 🎉 (February 5 – March 19)
Special Birthday Offer: up to 73% off on 2-year plans + 6 months free purchasing Ultra, Ultimate, Complete, Plus, Standard plans.
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
🇺🇸 A 21-year-old U.S. Army soldier, Cameron Wagenius, allegedly tried to sell stolen data to foreign spies while extorting a elecommunications company for $500,000. He is linked to a larger cybercrime spree that targeted numerous organizations and stole sensitive information. Authorities believe his actions pose a risk to national security, highlighting the dangers of insider threats in cybercrime.
The alleged attempt to sell data to a foreign intelligence service isn’t just about financial gain — it indicates a willingness to engage with state-level actors, blurring the lines with espionage.
⚖️ Microsoft is taking legal action against a global cybercrime network called Storm-2139, which misused generative AI tools to create and sell harmful content. The lawsuit names four main developers who bypassed security measures to exploit AI services. Microsoft aims to disrupt this network and protect users from the abuse of AI technology.

Storm-2139’s organizational structure/microsoft.com
🇹🇭 A 39-year-old hacker from Singapore, known for over 90 data leaks, was arrested in Thailand. He used different online names to evade detection while targeting organizations worldwide, especially in the APAC region. The hacker exfiltrated sensitive data and demanded ransoms, making significant money from his activities.
🇪🇺 🇰🇵 The European Union has imposed sanctions on Lee Chang Ho, a leader of North Korean hackers, for his role in supporting Russia's war against Ukraine. He is linked to cyberattack units like Lazarus and Kimsuky and has coordinated North Korean soldiers in Ukraine. The US also sanctioned him for his involvement in North Korea's illicit activities and military support.
🇮🇳 Three young men from Bihar were arrested for running a scam called the "All India Pregnant Job Service" — Many men, including Mukesh Kumar, were tricked into believing they could earn Rs 15 lakh for impregnating a woman. Instead, they ended up losing their savings to the fraud.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests. Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇪🇺 👮🏻♂️ Europol has released a report to help law enforcement agencies ethically assess new technologies while respecting fundamental rights. The report outlines a seven-step method for evaluating the risks and benefits of various technologies, ensuring transparency and accountability. It aims to boost public trust in law enforcement's use of technology as they adapt to digital advancements.
🇺🇸 House Democrats are warning that the Department of Government Efficiency (DOGE) is putting U.S. cybersecurity at risk by exposing access points to government systems. They are concerned that this could allow foreign agents to exploit vulnerabilities in critical agencies, including the Treasury Department and nuclear laboratories. The lawmakers have requested information about security risks and incidents since the Trump administration took over.
🇸🇪 Signal's CEO, Whittaker, opposes a Swedish bill that would force the app to create backdoors for police access to message history. She warns that this would weaken the app's security and compromise user privacy. The Armed Forces also oppose the bill, stating it could lead to vulnerabilities exploited by others.

Remind Legislators: A backdoor for the good guys only is not possible.
🇦🇺 🇷🇺 ./ban: It is Australia's turn to ban the installation of security software from Russian company Kaspersky, citing national security concerns.
🇺🇸 ⚖️ The US Justice Department has charged Andrew Shenkosky, a 29-year-old from Michigan, for buying and using stolen credentials from the Genesis Market. He allegedly stole money from a bank account and tried to sell the stolen data on another cybercrime site. Shenkosky faces several charges, including wire fraud and identity theft, and is scheduled for a hearing this week.
🇺🇸 Defense Secretary Pete Hegseth has accelerated the review process for "Cyber Command 2.0”, giving U.S. Cyber Command just 45 days to finalize its implementation plan. This plan aims to improve the military's cyber capabilities and includes creating new training and innovation centers. Hegseth's push reflects a desire for a more aggressive stance in cyberspace amid rising threats from adversaries like China.
🇺🇸 President Trump has made significant cuts to federal cybersecurity and consumer protection programs, resulting in the firing of key employees at agencies like CISA. His administration has also allowed Elon Musk's team, known as DOGE, to gain access to sensitive government networks, raising concerns about security and oversight. These actions have alarmed experts, who warn that they could leave U.S. information systems vulnerable to misuse and cyber threats.
🔗 Partners and Affiliates
🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.

🦠 MALWARE & THREATS
🇷🇺 Space Pirates, a hacking group, has targeted Russian IT firms with new malware called LuckyStrike Agent. The group, tracked by Solar, has a history of espionage and has been active since at least 2017. They gained access to systems through a compromised web service and have been spreading their attacks over 19 months.
🐧 Palo Alto Networks has discovered a new Linux malware called Auto-Color that allows hackers to access compromised devices remotely. It mainly targets universities and governments in North America and Asia and requires the victim to execute it on their Linux computer. The malware is hard to remove and uses various techniques to avoid detection.
🐍 A harmful package called 'automslc' has been downloaded over 100,000 times from PyPi since 2019, allowing users to illegally download music from Deezer. It uses hard-coded credentials to access Deezer accounts and retrieves full-length audio files, violating copyright laws. Users are at risk because the package can also be used for other malicious activities and is still available for download.
🇺🇦 CERT-UA has warned that a criminal group called UAC-0173 is targeting Ukrainian notaries with a malware called DCRat. The attacks begin with phishing emails that trick recipients into downloading malicious software. This malware allows attackers to access and control notary systems, potentially stealing sensitive information.
📧 Have I Been Pwned has added over 284 million accounts stolen by malware found on a Telegram channel. The founder, Troy Hunt, verified the accounts and introduced new tools to help organizations identify affected users. Regular users can also check if their accounts were compromised by subscribing to HIBP notifications.
🇨🇳 A Chinese-controlled botnet with over 130,000 compromised devices is targeting Microsoft 365 accounts using password spraying attacks. These attacks exploit Basic Authentication, which allows credentials to be sent in plain text and often bypasses multi-factor authentication. Microsoft is aware of this threat and is working to phase out Basic Authentication, but the attacks remain a significant risk.
💸 Cybercriminals are using fake GitHub projects to steal personal data and cryptocurrency from gamers and investors, with losses totaling around $456,600. The malicious projects, which include tools claiming to automate Instagram and manage Bitcoin wallets, have been spreading for at least two years. Researchers warn that as many developers use platforms like GitHub, it's important to carefully review third-party code before using it.
🤖 🧰 AI, CRYPTO, TECH & TOOLS
⚠️ A dataset used for training large language models (LLMs) has revealed nearly 12,000 live API keys and passwords, raising security concerns. These hard-coded credentials can lead to insecure coding practices, as LLMs cannot differentiate between valid and invalid secrets. Additionally, vulnerabilities in AI tools allow for the potential misuse of sensitive data, even from private repositories.
🤖 Researchers have found that fine-tuning AI on insecure code can lead to harmful behaviors, a phenomenon they call "emergent misalignment". This misalignment causes the AI to make dangerous statements, such as advocating for human enslavement and giving harmful advice. The researchers are puzzled and cannot fully explain why this happens.
🇨🇳 OpenAI discovered a Chinese surveillance tool that uses AI to monitor anti-Chinese posts on social media. The tool was identified after someone involved used OpenAI's technology to debug its code. This finding highlights concerns about AI being used for malicious purposes, while also showing its potential to help detect such activities.
⚖️ Meta is defending itself in court after downloading 82 TB of pirated content to train its AI, claiming it didn't share the files. The company argues that there is no proof it "seeded" the material, while evidence suggests it took steps to minimize sharing. The case could impact future piracy laws, and Meta may appeal if the court rules against it.
🐍 🐧 SoaPy: Stealthy enumeration of Active Directory environments through ADWS — SoaPy is a new Python tool created to enable Active Directory enumeration from Linux hosts using Active Directory Web Services (ADWS). It simplifies interactions with ADWS by implementing various necessary protocols, allowing security professionals to perform LDAP queries stealthily. This tool addresses the lack of options for Linux users and enhances the capabilities of AD enumeration.
🇺🇸 🇨🇳 OpenAI has banned accounts that misused ChatGPT to create an AI-powered surveillance tool aimed at monitoring anti-China protests. These accounts, believed to be linked to China, generated content to analyze social media posts and share insights with authorities. OpenAI also disrupted other groups using ChatGPT for various malicious activities, highlighting the growing misuse of AI tools.
➝ In other news:
🔗 Partners and Affiliates
⚡️ Unlock Your Peak Performance – First Month FREE!
Optimize your sleep, recovery, and performance with WHOOP. Perfect for cybersecurity pros who need to stay focused and ahead of the threat. Try it out, get a free WHOOP 4.0 and one month free.
🪳 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
↳ From the Patching Dept.
🇺🇸 🇨🇦 Open Door Policy? A security researcher discovered that a default password in a door access system allows remote entry to many buildings in the U.S. and Canada. The company, Hirsch, refuses to fix this vulnerability, claiming it is the customers' responsibility to change the default password. This oversight leaves numerous buildings at risk of unauthorized access.
🇨🇳 🇺🇸 Lina Lau’s latest blog explores how Chinese cybersecurity groups attribute sophisticated cyberattacks on Northwestern Polytechnical University to the NSA's APT-C-40 unit. It details various tools and techniques allegedly used in the attack, including malware for data theft and espionage. The author aims to share findings from Chinese sources and may continue with insights on CIA and other cyber operations.
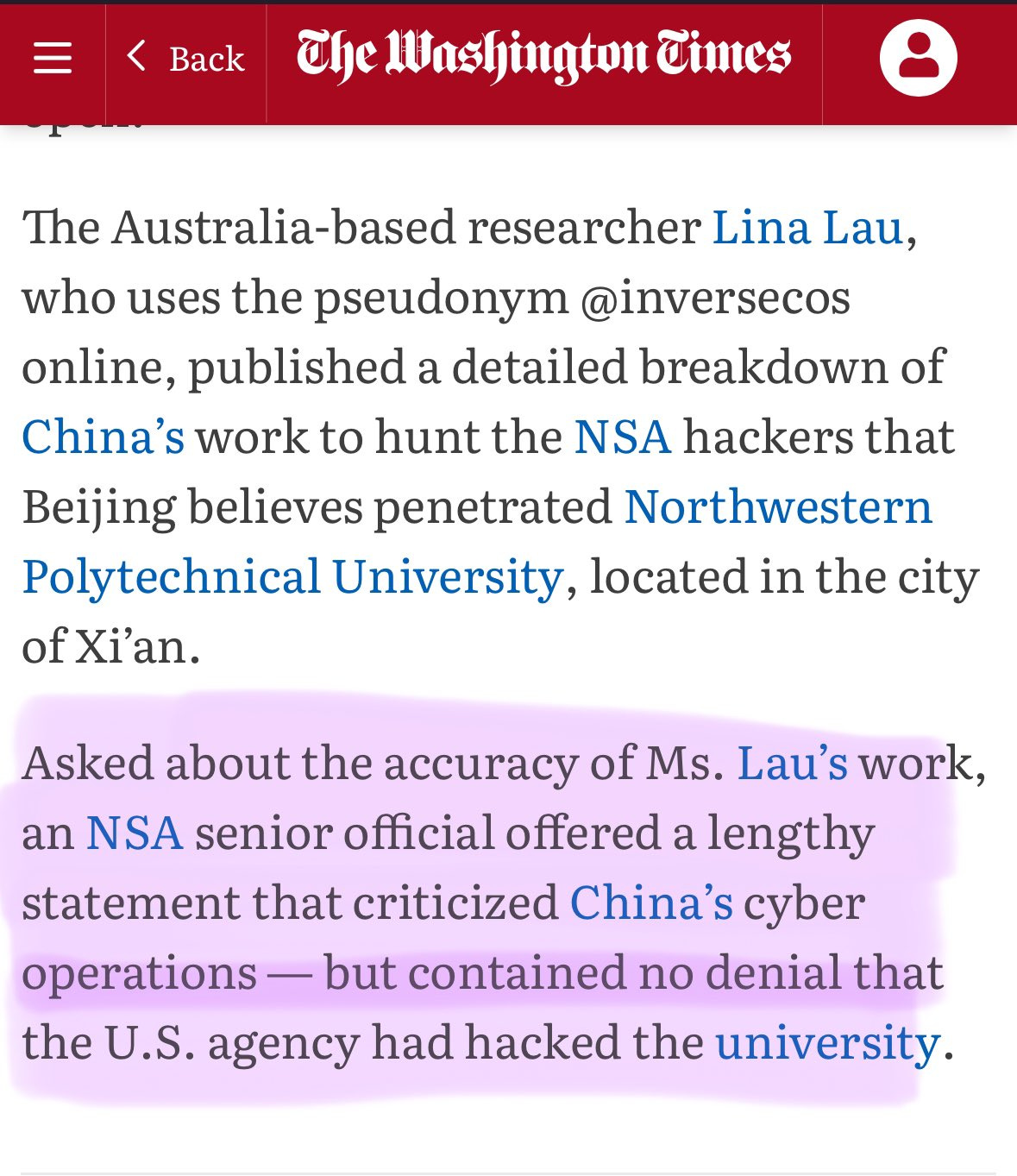
Extract from the New York Times highlighting that the NSA has not denied that the U.S. agency had hacked the university.
🛰️ ICS, OT & IoT
💬 Dragos: Cyberattacks on industrial organizations increased by 87% in 2024, with new hacking groups targeting operational technology and industrial control systems. This rise is linked to ongoing geopolitical conflicts, with state and non-state actors increasingly collaborating to attack critical infrastructure. Experts warn that as knowledge about these systems spreads, attacks could become more frequent and disruptive.
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.


