We now have {{active_subscriber_count}} subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
☁️ Oracle has denied a claim by a hacker that they stole 6 million data records from its Oracle Cloud servers. The hacker, known as rose87168, is offering the data for sale and alleges they accessed Oracle's systems around 40 days ago. Oracle stated that no customers were affected and that the published credentials do not belong to their cloud services.
🇨🇭 The HellCat hacking group has targeted the Swiss company Ascom by breaching its Jira ticketing system and stealing about 44GB of data. Ascom confirmed the attack but stated it did not affect business operations and is cooperating with authorities. This incident is part of a broader trend where HellCat exploits compromised credentials to access Jira servers of various companies.
👀 SpyX, a consumer-grade spyware app, suffered a data breach last year, affecting nearly 2 million users, including many Apple customers. The breach exposed sensitive information like email addresses and iCloud credentials, but the operators did not notify those impacted. This incident highlights the ongoing risks associated with stalkerware and the need for users to secure their accounts.
🇺🇸 Hackers stole sensitive personal data from over 500,000 members of the Pennsylvania State Education Association (PSEA) during a cyberattack in July 2024. The stolen information includes Social Security numbers, medical details, and financial data. PSEA has stated they took steps to address the breach but did not confirm if the stolen data was deleted.
🇮🇳 Infosys Limited will pay $17.5 million to settle six class action lawsuits related to a 2023 data breach involving its subsidiary, Infosys McCamish System. The breach affected about 6.5 million individuals, resulting in the theft of personal information. The settlement will resolve all allegations without any admission of liability once approved by the court.
🇺🇸 Western Alliance Bank experienced a data breach affecting about 22,000 individuals due to a vulnerability in Cleo file transfer software. Personal information, including Social Security numbers and financial account details, was stolen during the attack in October 2024. The bank is offering one year of identity protection services to those affected. [Data Breach Notification]
🚗 Over 100 car dealership websites were compromised in a supply chain attack, serving harmful ClickFix code to visitors. This malicious code tricked users into executing commands that installed malware on their devices. The attack, linked to Russian-speaking cybercriminals, aimed to spread the SectopRAT remote access trojan.
🔗 Partners and Affiliates
🔐 NordVPN Spring Campaign 🌷 (March 19 — May 19)
Special Offer: up to 77% off + 3 extra months on selected 2-year plans.
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
🇨🇳 🇺🇸 Chinese hackers from the I-Soon firm targeted seven organizations in multiple countries, including the US and Taiwan, during a campaign called Operation FishMedley. They gained unauthorized access to sensitive networks and used various hacking tools to extract data. In March, the US indicted ten I-Soon employees for their involvement in these cyber espionage activities.

Names of FishMonger / I‑SOON members (source: FBI)
🇷🇺 Green Corridor: Leaked chat logs from the Black Basta ransomware group suggest that their leader, Oleg Nefedov, may have received assistance from Russian officials to escape after his arrest in Armenia. The messages reveal the group’s use of advanced tools and frameworks for cyberattacks, including a new automated system for credential-stuffing attacks. Researchers believe this information complicates the group's ability to start fresh without ties to their past activities.
🇨🇳 🇯🇵 The Chinese hacking group MirrorFace has targeted a Central European diplomatic institute as part of a campaign linked to the upcoming Expo 2025 in Japan. This marks the group's first known attack against a European entity, utilizing updated tools and techniques. MirrorFace is associated with the state-sponsored APT10 and continues to focus on Japanese interests while expanding its geographical reach.

The first email sent to the target/welivesecurity.com
🇪🇺 🤖 The EU's law enforcement agency warns that artificial intelligence is boosting organized crime and threatening society across Europe. AI is making cyberattacks more precise and dangerous, with criminals using it for fraud, extortion, and identity theft. The report highlights the need for urgent action to counter these evolving threats as they become more intertwined with state-sponsored activities.
💬 Not out of the woods just yet: Pavel Durov, the founder of Telegram, can now leave France despite an ongoing criminal investigation. He was previously arrested for allegations related to organized fraud and illegal activities on the platform. Durov has returned to Dubai and expressed gratitude for the change in his supervision conditions but still faces potential legal challenges. [Also, Russian zero-day seller is offering up to $4 million for Telegram exploits]
🔓 A security researcher released a free decryptor for the Akira ransomware that uses GPU power to unlock encrypted files. It took three weeks and $1,200 in GPU resources to develop this tool, which brute-forces encryption keys based on timestamps. The decryptor is available on GitHub, but users should back up their files before attempting to use it, as there are risks involved.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests. Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇺🇸 🤦🏻♂️ The U.S. Department of the Treasury has lifted economic sanctions against Tornado Cash, the crypto mixer, after reviewing legal and policy issues. They remain concerned about North Korea's cyber activities and are committed to stopping malicious actors from using digital assets for illegal purposes. FYI back in 2023, the Tornado Cash co-founders were charged by the U.S. Justice Department with helping criminals launder over $1 billion of stolen cryptocurrency through their decentralized crypto-mixing service. Just sayin’.

🇰🇵 North Korea is creating a new hacking group called Research Center 227 within its intelligence agency. This unit will focus on developing offensive hacking technologies and studying Western cybersecurity systems. North Korean hackers have previously targeted crypto exchanges, leading to significant thefts.
🇪🇺 🇺🇸 The European Commission is taking action against Apple and Google to enforce stricter regulations on Big Tech. Apple must allow support for non-Apple accessories, while Google faces potential fines for violating the Digital Markets Act. Despite Donald Trump's criticisms, Europe continues to push for fairer digital market practices.
🇫🇷 🇺🇸 A French researcher was denied entry to the U.S. because he expressed a personal opinion about Trump's research policies. His phone messages were deemed as expressing hatred towards Trump, leading to his expulsion back to France. The French government criticized this action, emphasizing the importance of freedom of opinion and academic cooperation.
💰 Clearview AI tried to buy millions of arrest records, including sensitive personal information like social security numbers and email addresses, to enhance its facial recognition database. This attempt faced legal disputes and ultimately fell through, with ongoing issues over payment. The company's practices raise serious privacy concerns, especially regarding biases in facial recognition technology that disproportionately affect people of color.
👀 A report by Citizen Lab suggests that Australia, Canada, Cyprus, Denmark, Israel, and Singapore may be using spyware from the Israeli company Paragon Solutions. The report highlights concerns about Paragon's claims of being a responsible vendor, especially after WhatsApp alerted users about potential spyware targeting. Citizen Lab found evidence linking Paragon's spyware to specific government customers, raising questions about its operations and accountability. [Also, WhatsApp patched zero-click flaw exploited in Paragon spyware attacks].
🇺🇸 A staff member at the Department of Government Efficiency (DOGE) violated Treasury rules by emailing unencrypted personal data to Trump administration officials. This breach was revealed in a court filing after the staffer, Marko Elez, resigned amidst controversy over racist social media posts. Elez has since been rehired at the Social Security Administration, raising concerns about data security.
🔗 Partners and Affiliates
🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.

🦠 MALWARE & THREATS
🌐 World Domination: The 'DollyWay' malware campaign has infected over 20,000 WordPress sites since 2016, redirecting users to malicious websites. It uses advanced techniques to maintain persistence and generate fraudulent traffic, now targeting users with fake dating, gambling, and other scam sites. Researchers have linked DollyWay to multiple malware operations, revealing a sophisticated network of attacks.
👾 A new malware called Arcane is stealing sensitive data from users by disguising itself as game cheats shared on YouTube and Discord. It targets various applications, including VPNs, messaging apps, and gaming clients, capturing account details and other personal information. Users are advised to avoid downloading unverified cheat tools due to the high risk of infection.
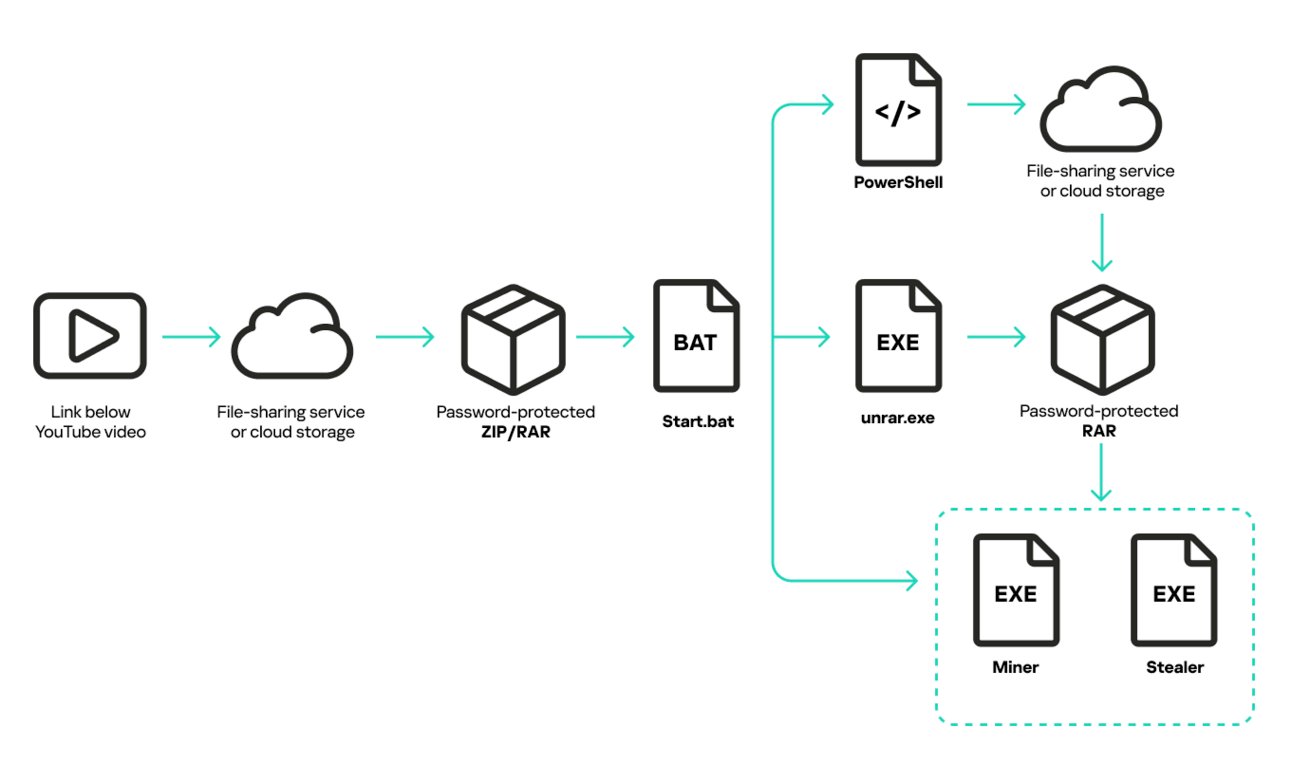
Original distribution scheme/securelist.com
🇺🇦 💬 CERT-UA warns of a new cyberattack targeting Ukraine's defense sector using Dark Crystal RAT malware sent through malicious messages on the Signal app. These messages contain fake meeting minutes and are sent from compromised accounts to trick recipients. The attacks are part of a broader trend of Russian cyber threats, as Ukraine increasingly relies on Signal for communication.
🎠 Microsoft has identified a new remote access trojan called StilachiRAT, which uses advanced techniques to avoid detection and steal sensitive information, particularly related to cryptocurrency. Although not widely distributed yet, Microsoft is sharing guidance to help protect against this threat. StilachiRAT can collect data from compromised systems, monitor clipboard activity, and impersonate users in active sessions.
🤖 🧰 AI, CRYPTO, TECH & TOOLS
🤑 Round 2.0.: Google's parent company, Alphabet, is in advanced talks to acquire cloud cybersecurity startup Wiz for around $30 billion. This follows a previous attempt last summer to secure a deal at a $23 billion valuation, which fell through. Wiz's strong annual recurring revenue and cloud security products are seen as a good fit for Google Cloud.
Today we have reached yet another milestone on our journey - we have signed a deal to be acquired by Google. The deal is subject to regulatory review, and Wiz will join Google Cloud after close.
→ Also, Industry Reactions to Google Buying Wiz: Feedback Friday [on SecurityWeek]
🏞️ Early Look: This Cloudflare's blog post explores cryptographic watermarking as a potential solution for identifying AI-generated content. As AI models improve, distinguishing their outputs from human-created content becomes challenging, raising concerns about authenticity. Watermarking embeds identifying information directly into AI-generated content, ensuring traceability even after modifications. This approach complements initiatives like C2PA, which relies on digital signatures, but watermarking offers a more embedded and persistent verification method. While still an emerging field, cryptographic watermarking shows promise in enhancing content integrity.
🗣️ Echo-out: Amazon is ending a rarely used privacy feature that allowed some Echo users to stop their voice commands from being sent to the cloud. Starting March 28, this option will be removed to support new AI features that require cloud processing. Users can still choose not to save voice recordings, and those affected will be switched to this option automatically.
🇵🇱 Poland has successfully created its first secure quantum-encrypted connection using domestic quantum key distribution (QKD) technology. This connection links the Ministry of Digital Affairs with the Military University of Technology, using advanced encryption to protect against cyber threats. The initiative is part of Poland's involvement in a European project aimed at enhancing quantum communication infrastructure.
🛠️ Google has released an updated version of its OSV-Scanner, a free tool for detecting vulnerabilities in open source software. The new version integrates features from OSV-SCALIBR and offers detailed scanning of various software formats and container images. OSV-Scanner V2.0.0 is now available on GitHub, and Google encourages user feedback and contributions.
💬 iPhone and Android users will soon be able to send encrypted messages to each other using the Rich Communication Services (RCS) protocol. This new feature, based on end-to-end encryption, ensures that only the sender and recipient can read the messages. The update aims to enhance privacy and security for users while communicating across different devices.
🔗 Partners and Affiliates
⚡️ Unlock Your Peak Performance – First Month FREE!
Optimize your sleep, recovery, and performance with WHOOP. Perfect for cybersecurity pros who need to stay focused and ahead of the threat. Try it out, get a free WHOOP 4.0 and one month free.
🪳 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
💥 Smart. Not: SANS is seeing attempts to exploit two critical Cisco Smart Licensing Utility vulnerabilities tracked as CVE-2024-20439 and CVE-2024-20440.
💥 Hackers are increasingly targeting three year-old vulnerabilities in ServiceNow software to access unpatched systems. Security firm GreyNoise reported a spike in these attacks, particularly affecting organizations in Israel and other countries. The flaws can be exploited to gain full access to sensitive data, raising concerns for companies using the ServiceNow platform.
🤑 VulnCheck has raised $12 million in a Series A funding round to enhance its vulnerability intelligence platform. The funding, led by Ten Eleven Ventures, will help the company grow and expand internationally.
💥 Cybersecurity firm Veriti reports that a vulnerability in ChatGPT, known as CVE-2024-27564, is being exploited by attackers against US government and financial organizations. This flaw allows unauthorized users to make arbitrary requests, leading to potential data theft. Veriti warns that many organizations are at risk due to misconfigurations in their security measures.
💥 Exploit code for a serious vulnerability in Apache Tomcat was shared on a Chinese forum shortly after patches were released. This vulnerability allows attackers to gain control of servers with a simple request, without needing authentication. Experts warn that this could lead to more serious attacks in the future, as attackers may adapt their tactics.
🔓 A popular GitHub Action called tj-actions/changed-files was compromised, risking secrets in over 23,000 repositories. The attack modified the action's code to leak sensitive information, such as AWS keys and GitHub tokens, in build logs. Users are advised to update to the latest version and review their workflows for any unexpected outputs.

Diagram: overview of the compromised GitHub Action's malicious functionality / Source: wiz.io
🛰️ ICS, OT & IoT
🐛 Researchers have discovered two critical flaws in the mySCADA myPRO system that could allow attackers to take control of industrial control systems. These vulnerabilities could lead to severe disruptions and financial losses due to unauthorized access. Organizations are advised to apply patches and improve their security measures to protect against these risks.
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.






