We now have {{active_subscriber_count}} subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
🇰🇷 SK Telecom, South Korea's largest wireless carrier, was recently hacked, leading to a leak of customer data. The company detected the intrusion on April 19 and is investigating the incident, while offering free SIM protection to customers. It is unclear if the attack was a ransomware incident, and no group has claimed responsibility yet.
🇺🇸 Two healthcare organizations have confirmed data breaches affecting over 100,000 people due to ransomware attacks. Bell Ambulance in Milwaukee and Alabama Ophthalmology Associates in Birmingham both reported that hackers accessed sensitive personal and medical information. The incidents are part of a growing trend, with over 700 healthcare data breaches reported in the U.S. last year.
🇺🇸 Abilene, Texas, is working to restore its systems after a cyberattack began on April 18, causing some city services to go offline. The city has disconnected affected systems, engaged cybersecurity experts, and is investigating the incident, which may involve ransomware. Emergency services remain operational, and residents can still pay their bills, though online services may be slower than usual.
🇬🇧 Marks & Spencer has confirmed a cybersecurity incident causing disruptions for customers. While the stores are open, some in-store payment systems are not working, and the company is investigating the issue with external experts. The retailer is also taking steps to protect customer data and has informed data protection authorities. [More at bbc.com]
☁️ Microsoft is enhancing its cybersecurity by moving all account security keys into secure hardware and rotating them automatically to prevent hacks. They have also purged 6.3 million inactive Azure tenants and improved authentication methods for their services. This initiative aims to address vulnerabilities exposed by last year nation-state breach and improve overall security.
➝ More breaches:
🔗 Partners and Affiliates
🔐 NordVPN Spring Campaign 🌷 (March 19 — May 19)
With its user-friendly interface, robust security features, and commitment to privacy, NordVPN continues to be a popular choice for individuals seeking online protection and unrestricted internet access.
Special Offer: up to 77% off + 3 extra months on selected 2-year plans.
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
🇺🇸 💰 In 2024, the FBI reported that cybercriminals stole a record $16.6 billion, a 33% increase from the previous year. Older Americans, especially those over 60, were the most affected, filing complaints that totaled about $4.8 billion in losses. The report highlights that many cybercrimes go unreported, meaning actual losses could be much higher.
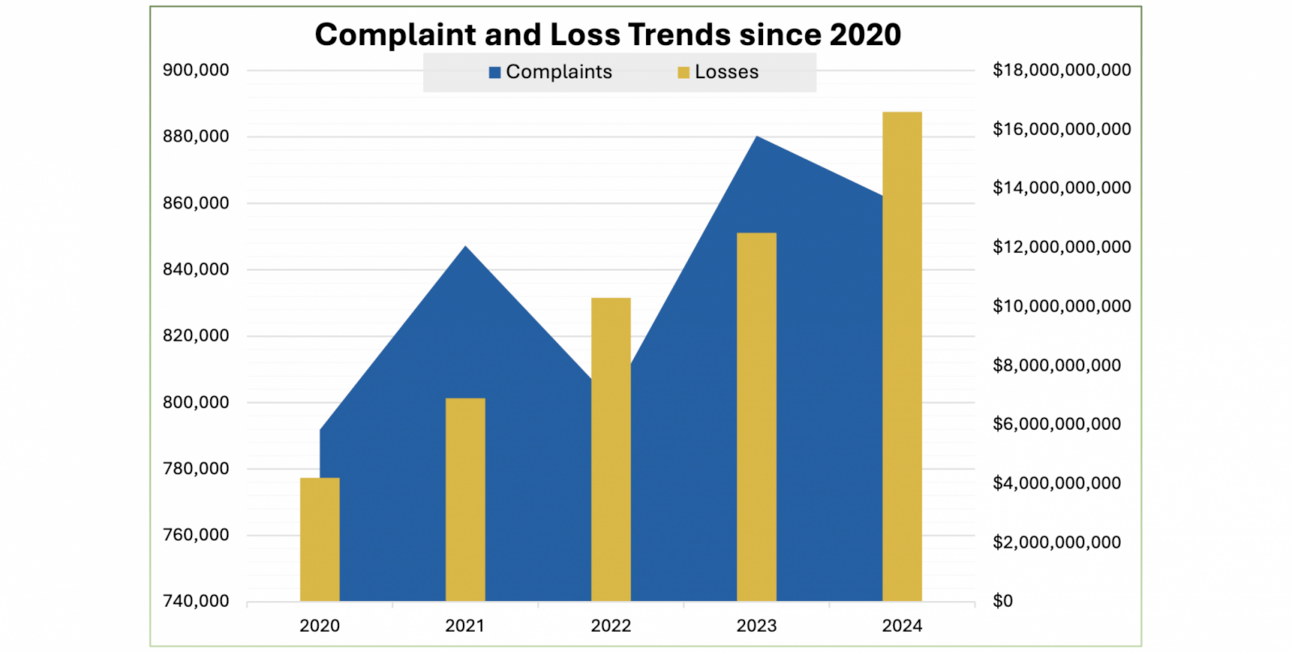
IC3 COMPLAINT STATISTICS/ic3.gov
☝🏻 🇺🇸 🇨🇳 The FBI is seeking public help to identify Chinese hackers known as Salt Typhoon, who have breached telecom providers in the U.S. and around the world. These hackers accessed sensitive networks, including a U.S. law enforcement wiretapping platform. The FBI is committed to protecting U.S. telecommunications and is offering rewards for information on these cybercriminals.
🇰🇵 🇰🇷 North Korean hackers, known as Lazarus, are targeting at least six South Korean organizations using a new strategy that combines watering hole attacks with software vulnerabilities. They exploited flaws in specific applications required for online banking and government services to deploy malware. The attacks, part of Operation SyncHole, highlight Lazarus's advanced techniques and ability to evade detection.
👀 🇷🇺 Russian military personnel are being targeted by new Android spyware that steals contacts and tracks locations. This malware is disguised as a modified version of the Alpine Quest mapping app. It is distributed through a Telegram channel and unofficial app stores, promoting itself as a free version of the paid app.
🌏 Asian crime groups are expanding their scam operations worldwide due to increased law enforcement actions in their home regions. These scams, which involve fake romantic schemes and bogus investments, now reach places like Africa and Latin America, generating nearly $40 billion annually. As these operations grow, new technologies are enabling criminals to adapt and continue their illicit activities.
🇰🇵 North Korean hackers have stolen $137 million from TRON users in a phishing attack, targeting the cryptocurrency sector to fund their weapons programs. They use various techniques, including fake job offers and social engineering, to access victims' digital assets. Additionally, DPRK IT workers create fake identities to infiltrate companies and steal data while evading detection.
🇰🇵 North Korean hackers are using Zoom's remote control feature to steal information from cryptocurrency traders. They pose as legitimate investors and trick victims into granting access to their computers during meetings. This method has led to significant financial losses and highlights the risks of social engineering attacks in the blockchain industry.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests. Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇨🇳 Chinese Wall. Again — A Chinese startup called Sand AI has launched a video-generating AI model named Magi-1, which is praised for its quality but censors politically sensitive images. The platform blocks uploads of images related to figures like Xi Jinping and events like Tiananmen Square to comply with government regulations. Other Chinese companies also censor content, but Sand AI's filtering is notably strict.
🇺🇸 PEBCAK — Defense Secretary Pete Hegseth shared sensitive details about upcoming military strikes in Yemen in a private Signal chat with his wife, brother, and lawyer. This raised concerns about security protocols, as those included had no clear need for such information. The situation is under review, and there have been criticisms regarding Hegseth’s judgment and adherence to military protocols.
🇺🇸 ⚖️ A federal judge has limited the evidence NSO Group can use in its trial with WhatsApp, preventing them from discussing their customers' identities or claiming the targeted users were criminals. This ruling is seen as a victory for WhatsApp and its users, as it focuses the trial on NSO Group's actions rather than attacking the victims. While WhatsApp also had some limitations on what it can present, the judge's decision significantly impacts NSO Group's defense strategy.
🇺🇸 👋🏻 Two top officials from CISA, Bob Lord and Lauren Zabierek, are resigning after leading the "Secure by Design" initiative, which aimed to improve cybersecurity in products from the start. Their departures raise concerns about the future of this important program. Despite leaving, both expressed optimism about the ongoing movement for better cybersecurity practices.
🇺🇸 New Deputy Director for CISA: Madhu Gottumukkala has been appointed as the new deputy director of the Cybersecurity and Infrastructure Security Agency (CISA). He previously served as the commissioner of the Bureau of Information and Telecommunication in South Dakota. Gottumukkala aims to enhance the nation’s digital and physical infrastructure in his new role.
🔗 Partners and Affiliates

🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
🦠 MALWARE & THREATS
🚢 Cybersecurity researchers have uncovered a new malware campaign that targets Docker environments to mine cryptocurrency using fake heartbeat signals. The malware connects to a Web3 service called Teneo, earning rewards without actually scraping data. This shift in tactics reflects a move away from traditional cryptojacking methods like XMRig, as attackers seek less detectable ways to profit.
🇷🇺 The Proton66 network, linked to Russian cybercriminals, supports various malware campaigns and bulletproof hosting services. Security researchers have seen a rise in attacks from this network, including ransomware and phishing targeting organizations worldwide. Proton66 has been involved in exploiting vulnerabilities and distributing malware across multiple sectors, particularly in technology and finance.

Figure: Sectors targeted by scans, brute force, and exploit attempts from 193.143.1.65/SpiderLabs
🎣 Phishers are using a sophisticated attack that sends fake emails appearing to come from Google, tricking users into providing their credentials. The emails pass security checks and direct victims to a fraudulent Google Sites page that looks legitimate. Google has implemented measures to combat this issue, urging users to enable two-factor authentication for better protection.

Figure: Alarming email that looked strikingly legitimate/easydmarc.com
🤖 🧰 AI, CRYPTO, TECH & TOOLS
📷 Microsoft has launched the controversial Windows Recall feature after nearly a year of delays and testing. Recall, available only on certain Windows 11 PCs, continuously takes screenshots and saves them in a searchable database, raising privacy concerns. The feature faced harsh criticism for its security issues before its public release.
🔗 Partners and Affiliates
⚡️ Unlock Your Peak Performance – First Month FREE!
Optimize your sleep, recovery, and performance with WHOOP. Perfect for cybersecurity pros who need to stay focused and ahead of the threat. Try it out, get a free WHOOP 4.0 and one month free.
🐛 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ Pre-RSA Announcements:
RSA Conference 2025 – Pre-Event Announcements Summary (Part 1) [by Security Week]
RSA Conference 2025 – Pre-Event Announcements Summary (Part 2) [by Security Week]
🩹 SAP has released urgent updates to fix a critical vulnerability in NetWeaver that allows attackers to upload malicious files and take control of servers. This flaw, tracked as CVE-2025-31324, can be exploited without authentication, leading to remote code execution. Users are urged to apply the latest patch immediately to protect their systems.
🐛 💥 In the first quarter of 2025, VulnCheck found 159 actively exploited vulnerabilities, with many being attacked within a day of disclosure. The report highlights an increase in exploitation rates, especially targeting network edge devices like VPNs and firewalls. Researchers urge quick action from defenders to address these emerging threats.
🔓 Cisco has confirmed that several of its products are affected by a critical vulnerability in Erlang/OTP, which can allow attackers to take control of systems. The flaw, tracked as CVE-2025-32433, makes it easy for unauthorized users to access sensitive data or launch attacks. Cisco is investigating the impact on its products and plans to release patches in May.
📨 A critical vulnerability in the Active! Mail web-based email client is being exploited in attacks on large organizations in Japan. Users are urged to update to the latest version to protect against potential remote code execution. Two web hosting providers have temporarily suspended their Active! Mail services due to these attacks.
🛰️ ICS, OT & IoT
🐛 A vulnerability in the Lantronix XPort device, used in critical infrastructure like energy and transportation, can allow remote hacking. This flaw could let attackers access and control systems, posing significant risks, especially in the oil and gas sectors. Lantronix has not yet released a fix but recommends users upgrade to a safer product.
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Enjoying our newsletter? Forward it to a colleague—
it’s one of the best ways to support us.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.