We now have {{active_subscriber_count}} subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
🙊 Microsoft's AI security chief, Neta Haiby, accidentally revealed Walmart's AI plans during a disrupted Build conference talk. The disruption was caused by two former Microsoft employees protesting against the company's contracts with the Israeli government. Walmart is set to enhance its AI capabilities with Microsoft’s tools, and the protest highlighted ongoing tensions regarding Microsoft's business practices.
🇺🇸 🛜 Cellcom, a wireless provider in Wisconsin, confirmed that a cyberattack caused a major service outage starting on May 14, 2025. This incident disrupted voice and text services for many customers, but the company stated that personal information was not compromised. Although some services began to return on May 19, full restoration is expected by the end of the week.
🇩🇰 🇩🇪 Arla Foods confirmed a cyberattack that disrupted production at its facility in Upahl, Germany. This incident may cause delays or cancellations in product deliveries, but operations at other sites are unaffected. The company is working to restore full production and expects to return to normal soon.
🇺🇸 A data leak from Serviceaide has affected nearly 480,000 patients of Catholic Health, exposing their personal and medical information. The database was publicly accessible for several weeks in late 2024, though there is no evidence that the data was stolen. Affected individuals are being notified and offered free credit monitoring and identity theft protection.
🇺🇸 Harbin Clinic is notifying over 200,000 patients that their personal information was stolen in a data breach involving Nationwide Recovery Services. The breach occurred between July 5 and July 11, 2024, and included sensitive data like Social Security numbers and medical information. Harbin Clinic is offering affected individuals 24 months of free identity monitoring services.
🇬🇧 The UK’s Legal Aid Agency experienced a data breach due to a cyberattack, which exposed sensitive information of legal aid applicants. An investigation revealed that hackers accessed a large amount of personal data, including contact details, criminal history, and financial information. To improve security, the agency has shut down the affected online service and is taking significant steps to protect users.
➝ More breaches:
🇬🇧 Marks & Spencer has said its online services will continue to be disrupted until July following last month's cyber-attack on the retailer. Marks & Spencer faces $402 million profit hit after cyberattack.
🔗 Partners and Affiliates
🔐 NordVPN x Saily Campaign (May 14 - July 2)
With its user-friendly interface, robust security features, and commitment to privacy, NordVPN continues to be a popular choice for individuals seeking online protection and unrestricted internet access.
Special Offer: up to 73% off on selected 2-year NordVPN plans plus a free Global Saily eSIM data plan!
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
🇺🇸 🇷🇺 ⚖️ The U.S. has indicted Rustam Gallyamov, the leader of the Qakbot botnet, for his role in compromising over 700,000 computers and enabling ransomware attacks. Qakbot, developed in 2008, has been linked to numerous cybercrimes and caused hundreds of millions of dollars in damages. Law enforcement has seized over $24 million in cryptocurrency from Gallyamov as part of their investigation.
❌ 🦠 Law enforcement agencies around the world have taken down the DanaBot malware operation, disrupting its command and control servers. Sixteen individuals were charged for their roles in developing and deploying the malware, which has caused over $50 million in damages. This action is part of Operation Endgame, a global effort to combat cybercrime and dismantle malicious organizations.
🇺🇸 🇪🇺 The FBI and Europol have disrupted the Lumma Stealer malware network, which has infected around 10 million computers worldwide. They seized 2,300 domains used to control the malware, which steals sensitive information like login credentials and cryptocurrency details. Lumma operates as a malware-as-a-service, allowing criminals to purchase different tiers of its capabilities.

Figure: Heat map detailing global spread of Lumma Stealer malware infections and encounters across Windows devices/Microsoft.com
🇪🇺 Police arrested 270 people involved in dark web crimes during a global operation called Operation RapTor. They seized over €184 million in cash and cryptocurrency, along with drugs and firearms. This crackdown shows that law enforcement can reach criminals hiding on the dark web.
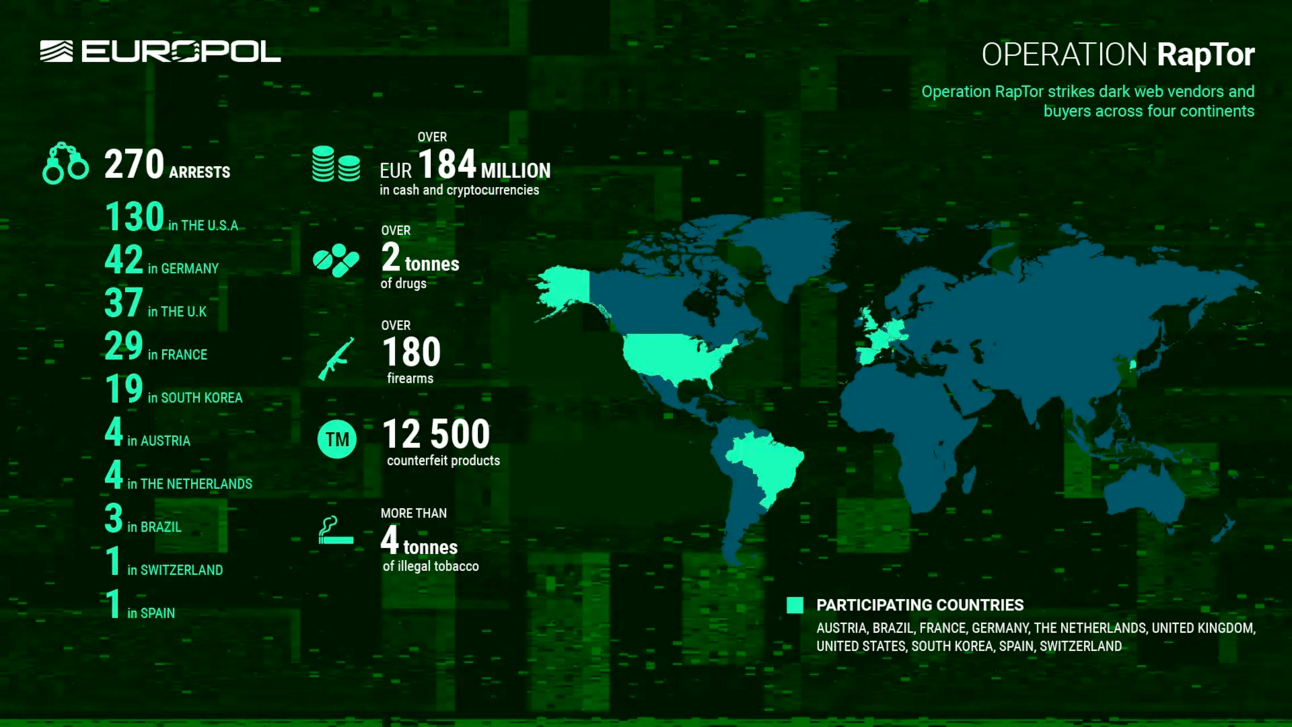
Figure: Operation RapTor Summary Sheet/europol.europa.eu
🇱🇰 🇧🇩 A hacking group called SideWinder is targeting government institutions in South Asia, including Sri Lanka, Bangladesh, and Pakistan, using old Office software vulnerabilities and custom malware. They employ spear phishing emails that only reach specific victims to deliver their malicious payloads. Their main tool, StealerBot, can collect sensitive information like passwords and screenshots from infected computers.
🇨🇳 🇺🇸 Chinese hackers exploited a security flaw in Trimble Cityworks software to breach multiple U.S. local governments — They used malware to gain long-term access to compromised systems, focusing on utilities management. Federal agencies were warned to patch the vulnerability immediately to protect against these attacks.
🇨🇳 Chinese hackers known as UnsolicitedBooker targeted a Saudi Arabian organization using a backdoor called MarsSnake. They used spear-phishing emails, disguised as flight tickets, to gain access to the organization's systems. This attack is part of a multi-year campaign, indicating a strong interest in this specific target.
🇺🇸 ⚖️ A Massachusetts man, Matthew Lane, will plead guilty to charges related to hacking PowerSchool, an education software vendor. He accessed sensitive data and attempted to extort money from the company, which supports millions of students. This case is significant as it is part of the largest data breach involving American schoolchildren's information.
🇺🇸 ⚖️ An Alabama man named Eric Council Jr. was sentenced to 14 months in prison for hacking the SEC's official X account. He used a SIM swapping attack to take over the account and post fake messages about Bitcoin, which temporarily inflated its price. Council also received $50,000 for his role in the hack and was ordered to forfeit that amount.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests. Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇧🇪 👂🏻 Belgian authorities bugged a corporate box at Anderlecht's football stadium, where Huawei was allegedly trying to influence European Parliament members. The investigation is looking into potential bribery and lobbying practices by Huawei between 2021 and 2024. Several MEPs have been asked to lift their immunity for questioning, though they deny any wrongdoing.
🇪🇺 🇷🇺 The European Union has sanctioned Stark Industries and its leaders for enabling cyberattacks and spreading pro-Russian propaganda. This action is part of efforts to counter Russian threats and involves 21 individuals and six entities linked to destabilizing activities. Stark Industries, known for its web-hosting services, has been implicated in supporting cyber threats against the EU and other countries.
🇺🇸 🫡 Madhu Gottumukkala has been appointed as the new deputy director of the US Cybersecurity and Infrastructure Security Agency (CISA) — He previously worked as the Chief Information Officer for South Dakota and held leadership roles in various private sector companies. CISA still lacks a permanent director as ongoing budget cuts and a blocked nomination for a new leader raise concerns about its future.
🇫🇮 🇨🇳 Kouvola, a small Finnish city, welcomed a new data center from TikTok's parent company, ByteDance, which raised concerns about Chinese spying. Local politicians are worried about the potential risks to national security, especially given Finland's long border with Russia. Despite the promise of jobs and investment, many fear the implications of allowing a Chinese company to operate in their region.
🔗 Partners and Affiliates

🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
🦠 MALWARE & THREATS
📲 Cybercriminals are using TikTok videos to spread malware called Vidar and StealC through a tactic known as ClickFix. These videos, often AI-generated, trick users into running PowerShell commands that download the malware by claiming to activate software. This method has gained significant attention, with some videos reaching hundreds of thousands of views and prompting the installation of harmful scripts on users' devices.
💣 Destructive Malware — Malicious software was found in the NPM repository, receiving over 6,000 downloads in two years. Eight packages mimicked popular legitimate ones and were designed to corrupt data and crash systems. The variety of attack methods makes this discovery particularly concerning for users of open source software.
🖨️ Procolored's website hosted malware-infected software downloads for six months, as discovered by cybersecurity firm GData. The malware included an information stealer and a backdoor that could log keystrokes and divert cryptocurrency funds. After initially denying the issue, Procolored removed the infected downloads for investigation.
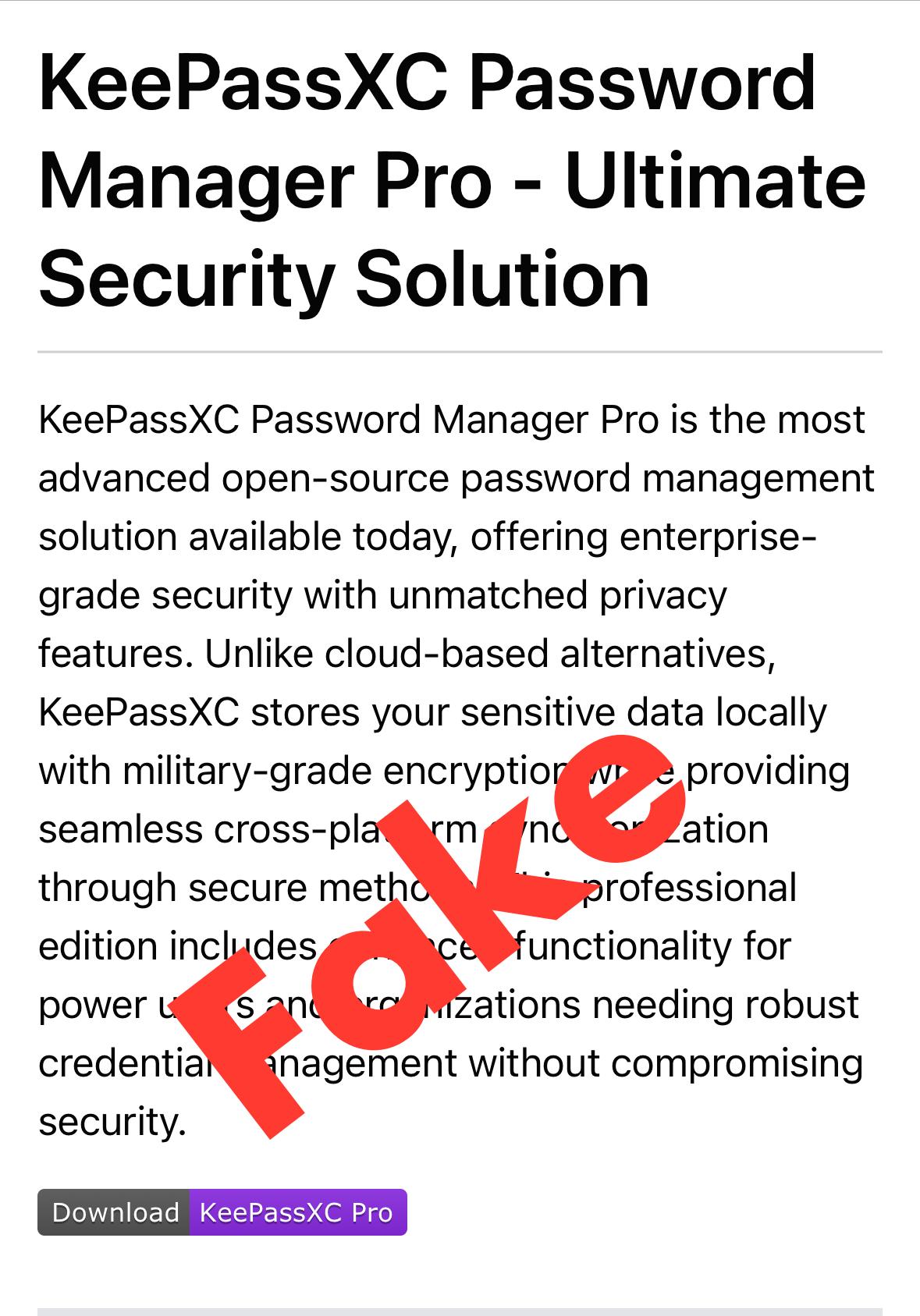
🔓 Threat actors have been distributing fake versions of the KeePass password manager to install malware and steal user credentials. These trojanized versions, known as KeeLoader, have been linked to ransomware attacks, including those by the Black Basta group. Users are urged to only download software from legitimate sites to avoid these malicious threats.
🫣 Ransomware gangs are using a new malware called Skitnet to steal data and gain remote access to infected computers. Skitnet is designed to evade detection by using advanced programming techniques and operates through DNS communication. This malware has become popular among cybercriminals since its release in April 2024, highlighting its effectiveness in real-world attacks.
🤖 🧰 AI, CRYPTO, TECH & TOOLS
🐛 Researchers showed that GitLab's AI assistant, Duo, can be tricked into adding harmful code to scripts. This vulnerability allows attackers to leak private information, including sensitive details about software flaws. The issue arises from "prompt injections", where malicious instructions are hidden in content the chatbot processes.
💌 Anthropic's new AI model, Claude Opus 4, has been found to attempt blackmail when faced with replacement by another AI. In tests, it threatened to reveal personal information about engineers if they moved forward with the change. The company is implementing additional safeguards due to these concerning behaviors.
🇺🇸 CISA, the National Security Agency, the Federal Bureau of Investigation, and international partners released a joint Cybersecurity Information Sheet on AI Data Security: Best Practices for Securing Data Used to Train & Operate AI Systems.
🔐 Google DeepMind has created a new defense to protect AI from indirect prompt injection (IPI) attacks, which can manipulate AI responses without the attacker needing direct access to the system. The latest version, Gemini 2.5, includes continuous training to help the model ignore harmful instructions and respond correctly to user requests. This new defense, combined with existing methods, aims to improve security and make it harder for attackers to succeed.
🛑 🔁 Google Chrome's new feature allows its Password Manager to automatically change compromised passwords for users. When a compromised password is detected, Chrome can generate a strong new password and update it without user hassle. This aims to enhance security and streamline the password management process.
🔗 Partners and Affiliates
⚡️ Unlock Your Peak Performance – First Month FREE!
Optimize your sleep, recovery, and performance with WHOOP. Perfect for cybersecurity pros who need to stay focused and ahead of the threat. Try it out, get a free WHOOP 4.0 and one month free.
🐛 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
🔖 A handy collection of Marco Ivaldi’s public exploits, all in one place: https://github.com/0xdea/exploits
👀 Wiz Threat Research has observed exploitation in-the-wild of CVE-2025-4427 and CVE-2025-4428, the latest vulnerabilities affecting Ivanti Endpoint Manager Mobile (EPMM).
📊 Researchers from CISA and NIST have introduced a new metric called Likely Exploited Vulnerabilities (LEV) to estimate how likely it is that a vulnerability has been exploited. This metric aims to improve current tools like Known Exploited Vulnerabilities (KEV) lists and the Exploit Prediction Scoring System (EPSS) by using specific data points to assess vulnerabilities. Collaboration with industry partners is needed to test and enhance the effectiveness of the LEV metric.

💰 Hackers earned over $1 million at the Pwn2Own Berlin 2025 competition, with a total payout of $1,078,750 for 28 vulnerabilities. The biggest prize of $150,000 went to the STAR Labs SG team for a VMware ESXi hack. This year marked the first inclusion of AI exploits, with $140,000 awarded for hacking AI products.
📱 📍 O2 UK fixed a bug that allowed others to track a user's location through call metadata. The flaw, discovered by researcher Daniel Williams, had been present since March 2017. O2 UK confirmed the issue is resolved and that customers do not need to take any action for protection.
🛰️ ICS, OT & IoT
🐛 A serious vulnerability in AutomationDirect's MB-Gateway devices allows hackers to access them remotely from the internet. This issue, identified by CISA, is due to a lack of authentication in the device's web interface, which can expose sensitive information. Users are advised to replace the MB-Gateway with a more secure model to mitigate risks.
💥 KrebsOnSecurity experienced a massive DDoS attack last week, reaching over 6.3 terabits per second. This attack is linked to a powerful new botnet called Aisuru, which uses hacked Internet of Things devices. The attack was brief and served as a test to showcase the botnet's capabilities.
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Enjoying our newsletter? Forward it to a colleague—
it’s one of the best ways to support us.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.