We now have {{active_subscriber_count}} subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
🇺🇸 Erie Insurance has confirmed that a recent cyberattack caused significant business disruptions and website outages. Customers have been unable to access their accounts or make claims since June 7, 2025. The company is working with law enforcement and cybersecurity experts to address the situation and ensure customer safety.
🇺🇸 Sensata Technologies experienced a ransomware attack that led to the theft of sensitive employee information, including Social Security numbers and financial details. The hackers accessed the company's systems from March 28 to April 6 before being detected. About 362 residents of Maine are known to be affected, but it is unclear how many others may be impacted.
🇺🇸 United Natural Foods (UNFI), a major grocery distributor, experienced a cyberattack that disrupted its operations. The company is working to restore its systems and has implemented temporary solutions to continue serving customers. UNFI is also the primary distributor for Whole Foods and has reported the incident to law enforcement.
➝ More Breaches:
🔗 Partners and Affiliates
🔐 NordVPN x Saily Campaign (May 14 - July 2)
With its user-friendly interface, robust security features, and commitment to privacy, NordVPN continues to be a popular choice for individuals seeking online protection and unrestricted internet access.
Special Offer: up to 73% off on selected 2-year NordVPN plans plus a free Global Saily eSIM data plan!
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
⚖️ 💸 Five men from different countries pleaded guilty to laundering nearly $37 million stolen from victims of cryptocurrency investment scams. They tricked people in the U.S. into investing, then funneled the stolen money through shell companies and bank accounts. Eight other accomplices have also pleaded guilty in connection to this international crime ring.
🇳🇬 🇺🇸 A Nigerian man named Kingsley Uchelue Utulu has been sentenced to over five years in prison for hacking U.S. tax preparation firms. He stole personal information to file fraudulent tax returns, obtaining about $2.5 million. Utulu must also pay over $3.6 million in restitution and forfeiture.
🇨🇳 SentinelOne reported that it faced a year-long campaign of cyberespionage from Chinese threat actors trying to probe its network and other organizations. Although the attackers never breached SentinelOne's systems, there were concerns about a third-party contractor being compromised. The company highlighted that cybersecurity vendors are increasingly targeted because compromising them can provide access to many clients.

Figure: PurpleHaze activity, September – October 2024/SentinelOne.com
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests. Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
👀 📲 Paragon spyware has been discovered on the phones of European journalists, marking its first detection on Apple devices. This finding comes from a report by the University of Toronto’s Citizen Lab and highlights ongoing concerns about government surveillance in Italy. The situation raises questions about the misuse of spyware technology, with a pattern of targeting critical journalists emerging.
🇺🇸 A House committee has approved a 2026 funding bill that cuts the Cybersecurity and Infrastructure Security Agency's budget by $135 million, which is much less than the Trump administration's proposed $495 million cut. Some lawmakers argue that these cuts weaken national security and make the U.S. more vulnerable to cyber threats. The bill still provides $2.7 billion for CISA, reflecting some bipartisan disagreement over the extent of the budget reductions.
🇺🇸 President Trump signed a new executive order to improve U.S. cybersecurity by changing parts of previous orders from Biden and Obama. This order focuses on software security, AI vulnerabilities, and digital identity issues, removing some mandates related to digital IDs. It also clarifies that cyber sanctions apply only to foreign individuals, not domestic political opponents.
🔗 Partners and Affiliates

🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
🦠 MALWARE & THREATS
🖥️ Over 269,000 legitimate websites were infected with malicious JavaScript called JSFireTruck in just one month. This malware redirects users to harmful sites if they come from search engines. Researchers warn that the scale and stealth of this attack pose a serious threat to online safety.

Figure: Injected code as found in the HTML page consists of only [, ], (, ), !, + and numbers/Palo Alto Networks Unit42
💬 🔗 Check Point Research revealed a malware campaign that hijacks expired Discord invite links to redirect users to malicious servers. Attackers use these links to deploy sophisticated phishing schemes and malware, including data-stealing programs targeting sensitive information. This highlights a serious flaw in Discord's invitation system, allowing criminals to exploit trusted sources for their attacks.
🐣 The hacking group FIN6 is using fake resumes on LinkedIn to spread a malware called More_eggs. They pose as job seekers to connect with recruiters and deliver phishing links that lead to malware downloads. This method helps them evade detection and steal sensitive information.
⌚️ A new attack called SmartAttack uses smartwatches to secretly steal data from air-gapped systems, which are isolated from external networks for security. The attack works by infecting a computer to emit ultrasonic signals that smartwatches can pick up and decode. To prevent this threat, experts recommend banning smartwatches in secure areas and removing built-in speakers from air-gapped machines.
❌ INTERPOL has dismantled over 20,000 malicious IP addresses linked to 69 types of malware in a coordinated effort called Operation Secure. This operation involved law enforcement from 26 countries and resulted in the seizure of 41 servers, more than 100 GB of data, and the arrest of 32 suspects. The malware was used to steal sensitive information like passwords and credit card details, which can lead to further cybercrimes.
👾 A new Rust-based malware called Myth Stealer is spreading through fake gaming sites and targets users of Chrome and Firefox. It tricks users with a fake window while stealing passwords and other sensitive information in the background. The malware is marketed on Telegram and can also be distributed as cracked game software.
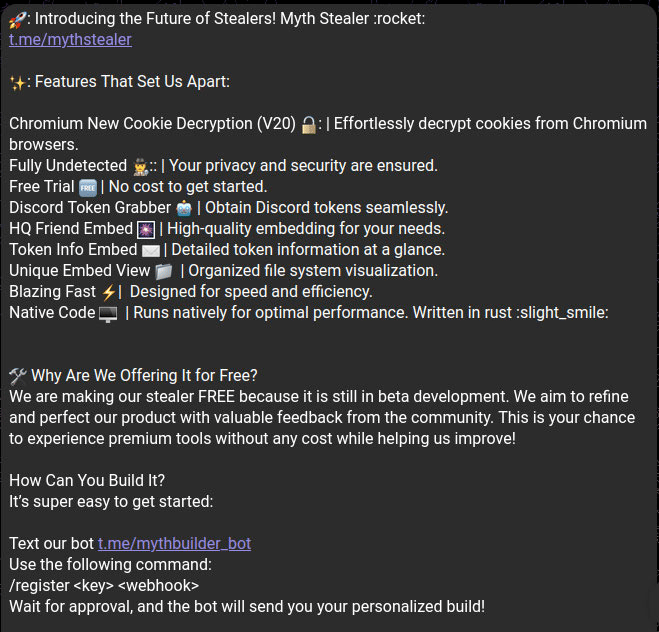
Figure: Promotional post made in telegram groups/Trellix.com
🤖 🧰 AI, CRYPTO, TECH & TOOLS
🇷🇺 🇮🇷 🇨🇳 OpenAI has banned ChatGPT accounts linked to Russian, Iranian, and Chinese hacker groups that used the AI to develop malware and automate social media tasks. These groups exploited the platform for various malicious activities, including creating trojan software and generating deceptive content for political influence. OpenAI's efforts aim to curb the misuse of its technology for cybercrime and misinformation.
🇷🇺 Russian developers are using Western cloud services and open-source apps to create military technology for their war against Ukraine. These apps, often installed outside official stores, exploit decentralized platforms, enabling Russia to conduct military operations with minimal resources. This situation poses a dilemma for Western tech companies, as their infrastructure inadvertently supports both Ukraine and Russia's military efforts.
🐛 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
🩹 🐛 Ivanti has released updates to fix three serious security flaws in its Workspace Control software that could allow attackers to access sensitive SQL credentials. These vulnerabilities are linked to a hardcoded cryptographic key and affect versions 10.19.0.0 and earlier. Fortunately, there is no evidence that these vulnerabilities have been exploited in real attacks before the updates were made public.
👥 Cybersecurity researchers found that a new campaign called UNK_SneakyStrike is targeting over 80,000 Microsoft Entra ID accounts using a tool called TeamFiltration. Attackers are exploiting Microsoft Teams and AWS servers to perform password spraying and account takeovers. This highlights how tools meant for security can be misused by criminals to access sensitive data.
🐛 Researchers found five zero-day vulnerabilities and 15 common misconfigurations in Salesforce Industry Cloud, affecting many organizations. The misconfigurations can pose serious risks, especially in industries like healthcare and finance, where sensitive information could be compromised. Salesforce addressed the vulnerabilities quickly, but users must be cautious about the security settings when customizing their CRM solutions.
🐛 A security researcher found a bug in Google that could expose users' private recovery phone numbers without their knowledge. Google fixed the issue after being alerted, and the researcher received a $5,000 reward for their discovery. The bug could lead to targeted attacks, increasing the risk of account takeovers.
🛰️ ICS, OT & IoT
🩹 ICS Patch Tuesday — Siemens, Schneider Electric, and Aveva have released security advisories addressing various vulnerabilities in their industrial systems. Notable issues include critical flaws with default credentials in Siemens Energy services and vulnerabilities in Schneider Electric's Modicon controllers. CISA also issued advisories on high-severity vulnerabilities in GPS receivers and other products.
🎥 Over 40,000 security cameras worldwide are exposed to hacking, allowing unauthorized users to access their live feeds. Most of these vulnerable cameras are found in the U.S., particularly in California and Texas, and are mostly used in the telecommunications sector. To protect these cameras, users should secure their internet connections, change default passwords, and disable remote access if it's not necessary.
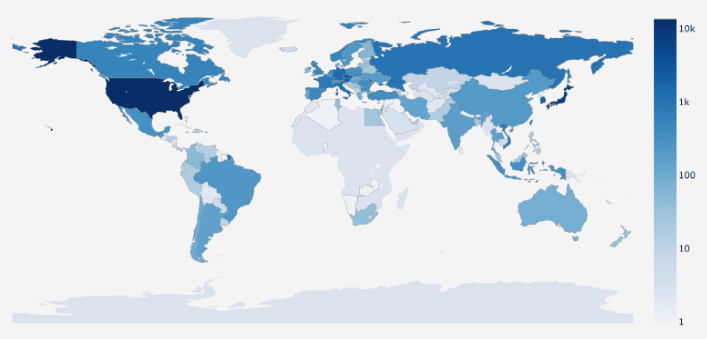
Figure: Geographical distribution of the 40,000+ exposed cameras/bitsight.com
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Enjoying our newsletter? Forward it to a colleague—
it’s one of the best ways to support us.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.