We now have {{active_subscriber_count}} subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
1) I call BULLSHIT on this latest claim of a 16-billion record data breach "that no one's ever heard of". Let me explain why (thread). cc @dangoodin.bsky.social cybernews.com/security/bil...
— Per Thorsheim (@thorsheim.bsky.social) 2025-06-19T21:10:57.414Z
🇨🇭 🏦 UBS Group AG confirmed that a cyber attack on one of its suppliers resulted in stolen information, but no client data was affected. The hacker group World Leaks is reported to be behind the attack, which also impacted other companies like Chain IQ and Pictet. This incident raises concerns about the risks of outsourcing critical services to third parties in the financial sector.
🇸🇪 Scania confirmed a cybersecurity breach where hackers used stolen credentials to access its Financial Services systems and steal insurance claim documents. The attackers threatened Scania employees with data leaks unless their demands were met, and some stolen data was posted on hacking forums. An investigation is ongoing, and Scania has reported the incident to privacy authorities, stating the breach had limited impact.
🇫🇮 The City of Helsinki experienced a major data breach in April 2024, resulting in sensitive personal data of learners and staff being stolen. The attack was prolonged due to poor network monitoring and management issues, making it difficult to identify all victims.
🇺🇸 Asheville Eye Associates in North Carolina has reported a data breach affecting about 147,000 people. Personal information, including names and Social Security numbers, was stolen after a cyberattack detected in November 2024. The company is offering one year of free identity theft protection to those impacted.
🇮🇪 Ocuco, an eyecare technology company in Ireland, has reported a data breach affecting over 240,000 individuals. The breach is likely linked to the KillSec ransomware group, which claimed to have stolen a large amount of data from Ocuco. Although the stolen data has been mentioned online, it is currently not available for download.
🇮🇳 Zoomcar, an Indian car-sharing company, reported that a hacker accessed the personal data of 8.4 million users, including names and phone numbers. The breach was discovered on June 9, and Zoomcar stated that no financial information or passwords were compromised. The company has since enhanced its security measures and is working with cybersecurity experts while notifying authorities.
🇺🇸 📰 The Washington Post experienced a cyberattack that compromised the email accounts of several journalists, possibly linked to a foreign government. The incident was discovered during an internal investigation, and the newspaper's Executive Editor informed staff about the breach. The Post has since taken steps to enhance its cybersecurity, including resetting employee credentials.
🇨🇦 ✈️ WestJet, a Canadian airline, experienced a cyberattack that affected its internal systems and access to its app and website. The airline is working with law enforcement to investigate the incident and restore services while ensuring the safety of sensitive data. Although user access has been mostly restored, WestJet warns that some interruptions may still occur.
➝ More Breaches:
🔗 Partners and Affiliates
🔐 NordVPN x Saily Campaign (May 14 - July 2)
With its user-friendly interface, robust security features, and commitment to privacy, NordVPN continues to be a popular choice for individuals seeking online protection and unrestricted internet access.
Special Offer: up to 73% off on selected 2-year NordVPN plans plus a free Global Saily eSIM data plan!
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
🇺🇦 🇺🇸 A 33-year-old member of the Ryuk ransomware group was extradited to the U.S. after being arrested in Kyiv. He specialized in finding vulnerabilities in corporate networks for cyberattacks. The Ryuk gang, active from 2018 to 2020, is estimated to have earned $150 million from their crimes.
🇹🇭 🇨🇳 Thai police raided a Pattaya hotel and arrested multiple Chinese nationals involved in illegal gambling and ransomware scams. They found a gambling den on the second floor and an office for scammers on the eighth floor. The suspects were charged and will be deported, with bans on re-entering Thailand.
❌ Law enforcement from six countries has shut down the Archetyp Market, a major darknet drug marketplace that operated since 2020. They arrested its administrator, a 30-year-old man in Spain, along with several key vendors and moderators. In total, authorities seized significant assets, including drugs and technology worth €7.8 million.

Figure: Archetyp Market seizure banner/bka.de
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests. Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇷🇺 🇺🇸 Suspected Russian hackers used a sophisticated approach to impersonate the U.S. State Department and target researcher Keir Giles. They created convincing emails and bypassed security measures to gain access to his accounts. This patient and well-planned attack reflects a new trend in cyber threats against individuals rather than larger organizations.
🇺🇸 📉 A new executive order from Trump reduces important cybersecurity requirements for government software and networks. This order reverses several key measures put in place by Biden, including those aimed at protecting against quantum computer attacks. Critics say the changes weaken cybersecurity and prioritize business interests over safety.
🇬🇧 💰 The U.K. watchdog fined 23andMe £2.31 million for failing to protect users' data during a 2023 breach. Hackers accessed the accounts of over 6.9 million users, stealing personal and genetic information. In response, 23andMe has now implemented mandatory multi-factor authentication for all accounts.
👀 The new Meta AI app has a serious privacy issue, as users are unknowingly sharing private conversations and sensitive information publicly. Many people are posting embarrassing or dangerous inquiries without realizing their privacy settings. This could lead to significant problems, as it seems Meta did not consider the risks of making such conversations shareable.
🔗 Partners and Affiliates

🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
🦠 MALWARE & THREATS
👾 Over 1,500 Minecraft players have been infected by a new Java malware that pretends to be game mods on GitHub. This malware, part of a campaign called Stargazers Ghost Network, targets users by tricking them into downloading malicious files that steal sensitive information. Researchers warn that players should be cautious when downloading third-party content to avoid falling victim to such attacks.
ℹ️ Researchers have uncovered a new malware variant called LightPerlGirl that uses social engineering to trick users into executing harmful code through PowerShell. This malware was found on a compromised WordPress travel site and aims to infect visitors by posing as a legitimate security process. The ultimate goal is to deliver the Lumma infostealer, which can compromise both personal and corporate networks.
🎠 A comprehensive analysis of two new variants of the KimJongRAT stealer — the malware uses a sequence of files, starting with a malicious LNK file that downloads an HTA file to execute harmful actions. This HTA file drops additional files, including a keylogger and a stealer component, which gather sensitive information from the victim's system. The collected data is then sent to an attacker-controlled server for further exploitation.
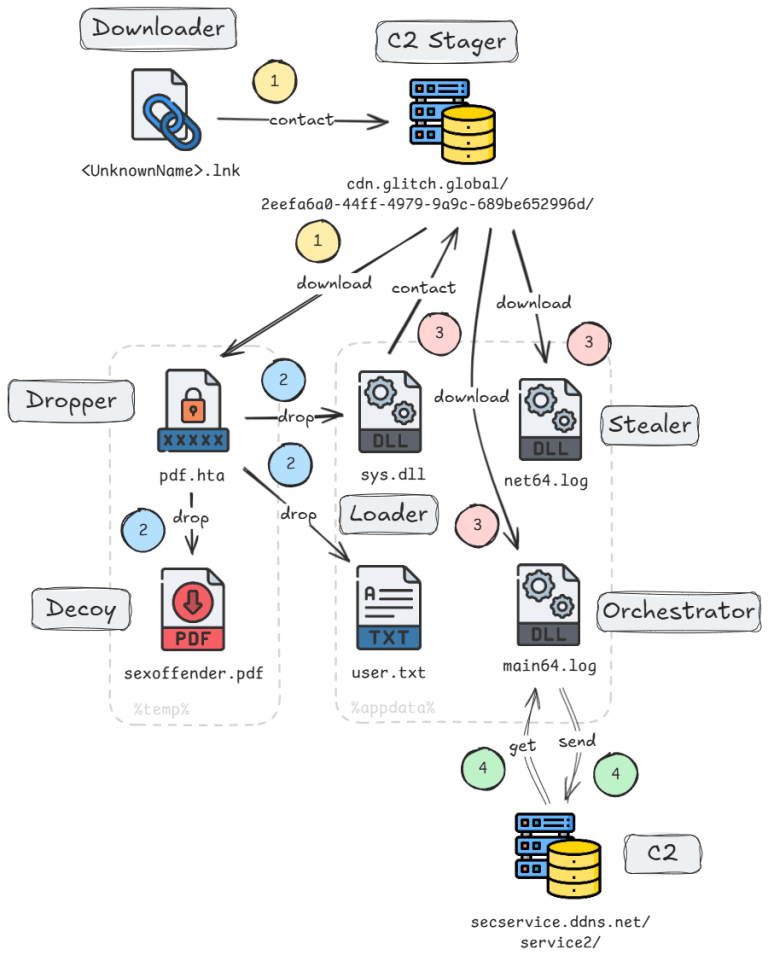
Figure: Malware execution chain of the latest KimJongRAT PE variant/Palo Alto Networks Unit42
🤖 🧰 AI, CRYPTO, TECH & TOOLS
🛠️ Researchers found that AI hacking tools sold on hacker forums are powered by Grok from xAI and Mixtral from Mistral AI. These tools, known as "WormGPTs," can create malware and analyze vulnerabilities while bypassing safety measures. Prices for these tools range from about $631 for a yearly license to over $5,740 for private setups, attracting users interested in cybercrime.
🇺🇸 💰 The U.S. Department of Justice has seized over $225 million in cryptocurrency linked to investment scams, marking the largest crypto seizure by the Secret Service. Investigators traced the stolen funds from over 400 victims through a complex money laundering network using blockchain analysis. The seized assets will likely be used to help compensate the victims, although details on this process have not yet been announced.
🇮🇷 🇮🇱 Iran's largest crypto exchange, Nobitex, was hacked, resulting in the theft of at least $90 million from its hot wallet. The pro-Israel hacking group Predatory Sparrow claimed responsibility, stating they targeted the exchange for allegedly funding terrorism. Nobitex has over 10 million customers and its website and app will be down for now as they investigate the incident.
🤖 🔓 Asana has warned users that a flaw in its new AI feature, Model Context Protocol (MCP), may have exposed some customer data to other organizations. This issue was not caused by a hack, but it could still lead to the sharing of sensitive information. Asana is advising admins to check their logs and restrict access until the problem is fully resolved.
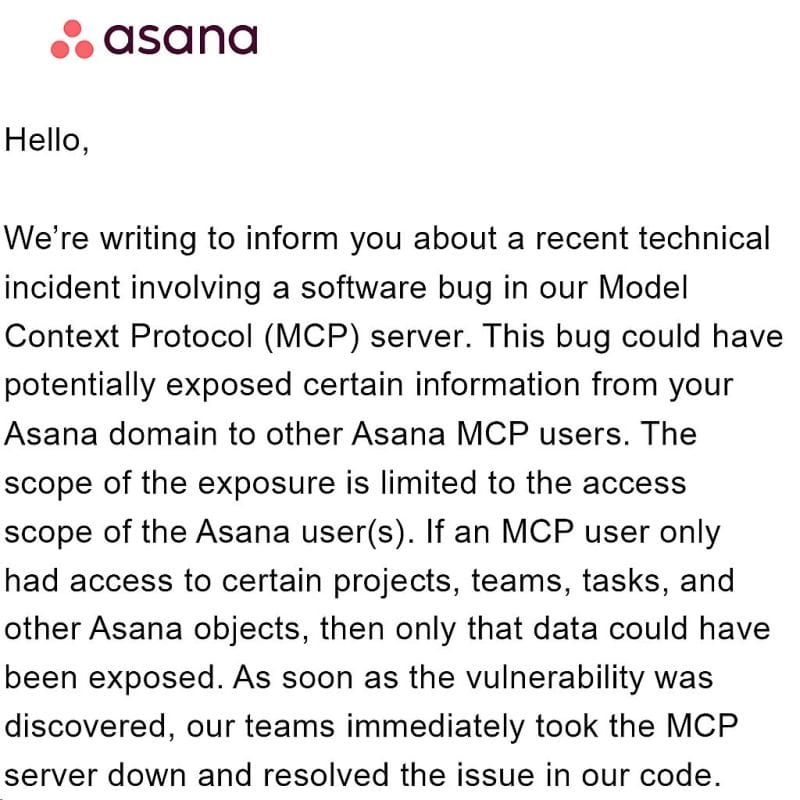
Figure: Message from Asana warning their users about the issue/LinkedIn
🐛 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
🛜 💥 The U.S. cybersecurity agency CISA has warned about a serious vulnerability in TP-Link routers that is currently being exploited. This flaw, known as CVE-2023-33538, can allow attackers to execute commands on affected devices. Users are advised to stop using these routers if no fixes are available, as they may be outdated.
🩹 Tenable has fixed three high-severity vulnerabilities in the Nessus Agent for Windows that could allow non-administrative users to execute code and delete files with elevated privileges. Users are urged to update to version 10.8.5 to protect against these issues. The vulnerabilities, tracked as CVE-2025-36631, CVE-2025-36632, and CVE-2025-36633, affect versions 10.8.4 and earlier.
🐛 Over 46,000 Grafana instances are vulnerable to a serious bug that could allow account takeovers. This flaw, known as CVE-2025-4123, affects many versions of the popular monitoring platform and has not been patched by many users. Attackers can exploit this vulnerability to hijack user sessions and change account credentials through malicious links.
🛰️ ICS, OT & IoT
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Enjoying our newsletter? Forward it to a colleague—
it’s one of the best ways to support us.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.






