- X’s InfoSec Newsletter
- Posts
- 🕵🏻♂️ [InfoSec MASHUP] 30/2025
🕵🏻♂️ [InfoSec MASHUP] 30/2025
Microsoft SharePoint Mayhem; The Lumma infostealer malware is making a comeback; Dior is notifying U.S. customers about a data breach; The UK government has imposed sanctions on three Russian military intelligence units; French authorities announced the arrest of an alleged administrator of the XSS.is cybercrime forum in Ukraine; Proton has launched Lumo, a privacy-focused AI assistant that does not log user conversations or use prompts for training;
We now have 1,604 subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
After a well deserved week off 🌴, I’m back! Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
🇺🇸 ⚖️ Clorox is suing IT company Cognizant for $380 million, claiming it was negligent in handling a cyberattack by resetting a hacker's password without proper identity verification. The attack, carried out by the group Scattered Spider in August 2023, caused significant disruptions to Clorox's operations. Clorox alleges that Cognizant's failure to follow security procedures led to their IT network being compromised and resulted in massive business losses.
🇨🇭 AMEOS Group, a major healthcare provider in Central Europe, announced a security breach that may have exposed personal information of customers, employees, and partners. The organization has shut down its IT systems and is working with experts to investigate the incident. While there are no signs of data being shared online, affected individuals are advised to stay alert for phishing attempts.
🇮🇳 CoinDCX, India's largest crypto exchange, confirmed that hackers stole $44 million from one of its internal accounts. The exchange assured customers that their funds are safe and the incident only affected the compromised account. CoinDCX is now working with authorities to investigate the hack and recover the stolen assets.
🇺🇸 Dell confirmed that the extortion group World Leaks breached its Customer Solution Centers platform and stole data. The stolen information is mostly fake or publicly available, with only an outdated contact list being legitimate. World Leaks, previously known as Hunters International, has shifted its focus from ransomware to data extortion.
🇺🇸 Dior is notifying U.S. customers about a data breach that exposed personal information from a January 2025 incident. The compromised data includes names, contact details, and Social Security numbers, but no payment information was affected. Affected customers are advised to monitor their accounts for suspicious activity and can enroll in free credit monitoring services.
➝ More breaches:
🔗 Partners and Affiliates
🔐 NordVPN Threat Protection Pro™ Campaign (July 2 - August 13)
With its user-friendly interface, robust security features, and commitment to privacy, NordVPN continues to be a popular choice for individuals seeking online protection and unrestricted internet access.
Special Offer: get up to 73% off with a 2-year plan!
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
🇺🇸 🇰🇵 Christina Marie Chapman, 50, was sentenced to over eight years in prison for helping North Korean workers fraudulently secure IT jobs at over 300 U.S. companies, generating $17 million in illegal revenue. She used stolen identities and operated a "laptop farm" to deceive these companies into believing the workers were based in the U.S. The case highlights the ongoing threat of North Korean cyber fraud and the importance of corporate vigilance against such schemes.
❌ Law enforcement has seized the dark web sites of the BlackSuit ransomware gang, which has attacked many organizations globally. This operation, called Operation Checkmate, involved multiple agencies, including the U.S. Homeland Security Investigations. Experts believe the gang may rebrand itself again as Chaos ransomware following the takedown.

Figure: BlackSuit seizure banner
🇫🇷 🇺🇦 French authorities announced the arrest of an alleged administrator of the XSS.is cybercrime forum in Ukraine. The arrest was part of a four-year investigation into cybercrime that involved over $7 million in profits. XSS is a Russian-language forum used for buying and selling malware and stolen data.
🇺🇸 ⚖️ Kristopher Lee Dallmann, the leader of the Jetflix illegal streaming service, was sentenced to seven years in prison for copyright infringement and money laundering. The service, which operated for 12 years, offered tens of thousands of pirated movies and TV episodes to subscribers. Dallmann made millions from this scheme, which harmed many copyright holders and undermined the law.
🇨🇳 China-linked hackers, known as APT41, have launched a new cyber espionage campaign targeting government IT services in Africa. They used sophisticated techniques, including compromised SharePoint servers, to execute commands and steal sensitive data. This marks a notable shift, as Africa had previously seen less activity from this hacking group.
🇬🇧 🇷🇺 The UK government has imposed sanctions on three Russian military intelligence units and 18 individuals linked to cyberattacks and assassination attempts. These units have been involved in serious operations against Ukraine and other countries, including notable attacks on political and military targets. The sanctions also include measures against individuals associated with disinformation campaigns and the development of malware.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests (and don’t forget to star the project); Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇬🇧 The UK government plans to ban public sector organizations from paying ransoms to cybercriminals to combat ransomware attacks. This move aims to disrupt the financial incentives for such crimes and requires private businesses to report ransom demands. The new measures are part of a broader strategy to strengthen cybersecurity and protect essential services.
🇬🇧 🇺🇸 UK officials are reconsidering their demand for Apple to create a backdoor for accessing customer data due to pressure from the US government. This situation has arisen because the UK’s insistence on the backdoor could harm technology agreements with the US. As a result, the UK government is trying to find a way to resolve the issue without damaging its relations with US leaders.
🇺🇸 After website hack, Arizona election officials unload on Trump’s CISA — Arizona election officials reported a hack that replaced candidate photos with images of Ayatollah Khomeini on their online portal. They criticized the Cybersecurity and Infrastructure Security Agency (CISA) for lacking support during the incident and claimed it has become unreliable under the Trump administration. Officials expressed concern that the deteriorating partnership with CISA puts election security at risk.
🇮🇷 🇮🇱 A hacking group linked to Iran, called MuddyWater, is using a new version of Android spyware named DCHSpy to target users during the ongoing Israel-Iran conflict. This spyware is disguised as VPNs and banking apps, collecting sensitive information from infected devices. The group has been active since at least 2017 and is known for its espionage operations in the Middle East.
👀 🇺🇸 Lift me Up! Scott Zuckerman, the founder of a spyware company banned by the FTC after a data breach, is asking to have that ban lifted. He claims the restrictions are too burdensome for his other businesses, despite having continued to operate in spyware after the ban. Privacy advocates are concerned that lifting the ban could allow Zuckerman to exploit consumer data again.
🔗 Partners and Affiliates

🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
🦠 MALWARE & THREATS
🛍️ A new warning alerts Amazon users about a surge in scam texts claiming to offer refunds, which have increased by 5000%. These messages are not from Amazon and lead to fake sites designed to steal your account information. If you receive such a text, delete it immediately and check your account directly through the Amazon app or website.
🪫 💸 A new Linux malware called Koske hides in panda images to secretly deploy cryptocurrency miners on infected systems. It uses clever techniques to run malicious code while appearing as innocent JPEG files. Researchers warn that this AI-driven malware could evolve into even more dangerous threats in the future.
🎣 ✈️ Phishers are targeting executives in the aviation industry, using fake emails to trick customers into sending large payments. An investigation revealed connections to a Nigerian cybercrime group called SilverTerrier, known for business email compromise scams. Victims can report fraud to the FBI to potentially recover lost funds through a process called the "financial fraud kill chain."
🎣 CastleLoader is a new malware loader that has infected 469 devices through fake GitHub repositories and phishing attacks. It uses techniques to avoid detection and connects to command-and-control servers to download additional malicious software. Cybersecurity experts warn that it is being rapidly adopted by various cybercriminal campaigns to steal data.
🇨🇳 Chinese hackers targeted the Tibetan community with fake apps ahead of the Dalai Lama's 90th birthday. They used compromised websites to install malware on victims' devices through two operations called GhostChat and PhantomPrayers. These attacks aimed to gather sensitive information by tricking users into downloading malicious software disguised as legitimate applications.
🔁 The Lumma infostealer malware is making a comeback after a major law enforcement operation disrupted its activities in May. Despite the takedown, the operators quickly restored their services and are using new methods to spread malware through fake software and compromised websites. This resurgence shows that law enforcement efforts alone are not enough to stop determined cybercriminals.
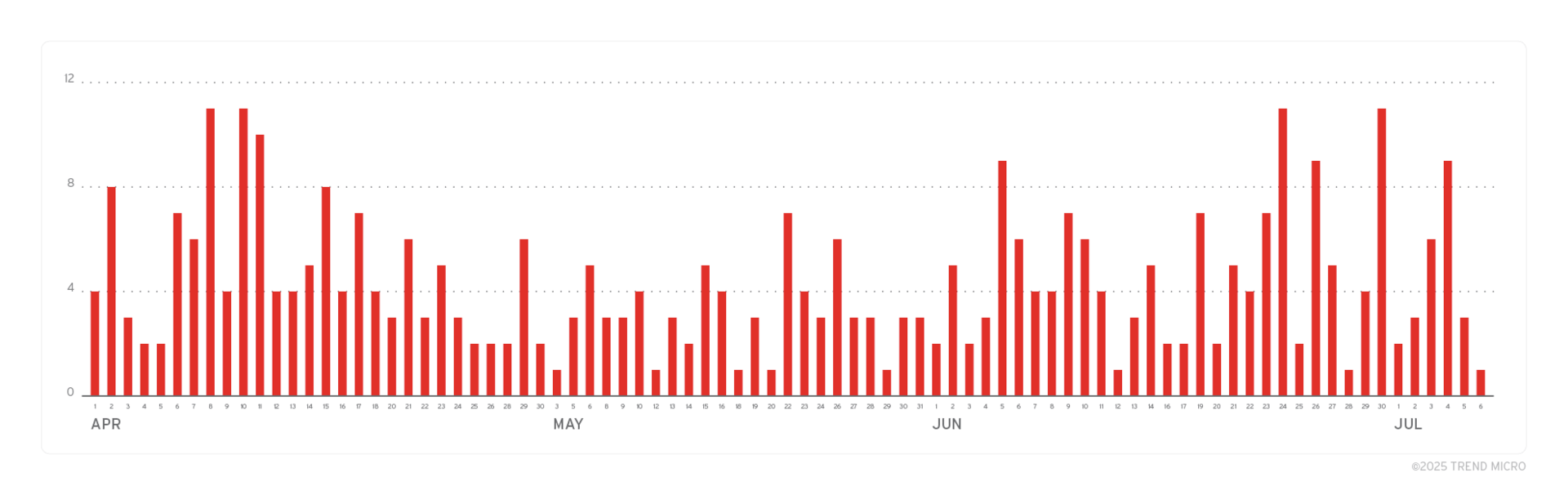
Figure: Lumma Stealer number of targeted accounts (April 1 to July 6, 2025)/Trendmicro.com
🏦 A new variant of the Coyote banking trojan is using a Windows accessibility feature to steal information from banking and cryptocurrency sites. It can identify targeted services by examining the browser's user interface elements. Researchers have warned that this technique can bypass many security protections, making it a significant threat.
🇲🇽 Mexican organizations are being targeted by a hacking group called Greedy Sponge, using modified malware like AllaKore RAT to steal banking credentials for financial fraud. The attacks involve phishing and drive-by downloads that deliver malicious ZIP files and trojanized software. Recent developments also include new malware like PureRAT and Hijack Loader, which are used to extract sensitive information and deploy additional threats.
🤖 🧰 AI, CRYPTO, TECH & TOOLS
🎙️ Enhancing Software Security in the Era of AI — In this episode, Chris Hughes sits down with longtime industry AppSec Leader, Educator, and Innovator Jim Manico to discuss enhancing software security in the era of AI.
🐈 Proton has launched Lumo, a privacy-focused AI assistant that does not log user conversations or use prompts for training. It is built on open-source technology and ensures that no sensitive data is stored on servers, complying with strict European data protection laws. Lumo offers various account tiers and supports multiple languages, making it accessible to a wide range of users.
🥊 AI vs. AI — The rise of A.I. has made cybercrime easier, with phishing attacks and deepfakes increasing significantly. While A.I. enhances both offensive and defensive cybersecurity strategies, it can also lead to serious mistakes. Traditional human defense methods are becoming outdated as automated A.I. systems take over security tasks.
🛠️ Google introduces OSS Rebuild — OSS Rebuild is a new project aimed at enhancing trust in open source software by creating reproducible builds of packages to prevent supply chain attacks. It provides tools and automation for security teams to verify package integrity without burdening the original developers. This initiative seeks to improve transparency and security in open source ecosystems, starting with popular package registries like PyPI, npm, and Crates.io.
🐛 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
🚨 🩹 Microsoft has released urgent security patches for a serious flaw in SharePoint that is being actively exploited in cyber attacks. The vulnerability, which allows remote code execution, affects on-premises versions of SharePoint Server, and organizations are urged to apply the updates immediately. Cybersecurity experts warn that many organizations, including banks and government entities, have already been compromised due to this issue.
🎙️ Not the Situation Room — In this episode, Nick and Dave are excited to welcome a new member to the team, Space Rogue. We conduct what you might call a, “roundtable discussion” on the currently radioactive Sharepoint vulnerability and need for stronger patch management practices.
📄 ToolShell: An all-you-can-eat buffet for threat actors — ESET Research has been monitoring attacks involving the recently discovered ToolShell zero-day vulnerabilities. As part of the attack, the threat actors often chain together four vulnerabilities: the previously patched CVE‑2025‑49704 and CVE-2025-49706, alongside the already mentioned CVE-2025-53770 and CVE-2025-53771. As of July 22, CVE‑2025‑53770 and CVE-2025-53771 have also been patched.
🐛 🛎️ Ring has stated that a bug caused many users to see unauthorized logins on May 28, 2025, leading to fears of hacking. Customers are skeptical, reporting strange devices and logins from locations they have never visited. Ring advises users to check their authorized devices, change passwords, and enable two-factor authentication for security.
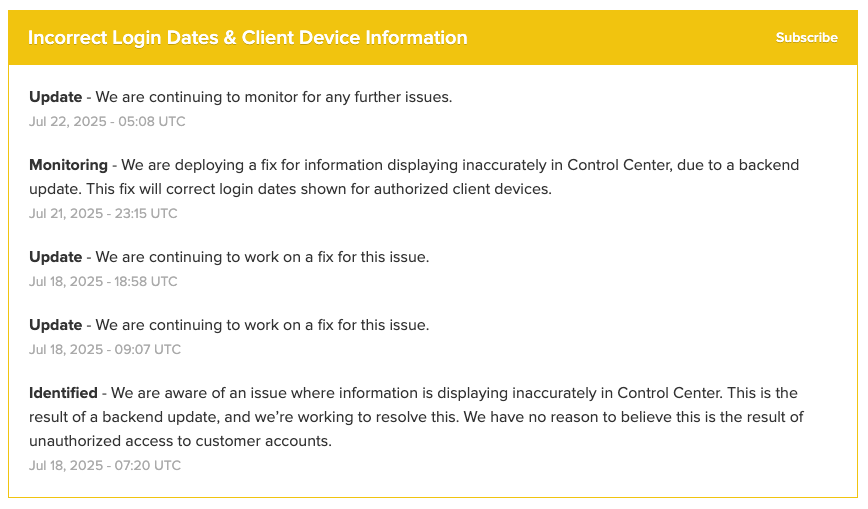
Figure: Updates on Ring’s status page/ring.com
🐛 Hewlett-Packard Enterprise (HPE) warned that hardcoded passwords in Aruba Instant On Access Points let attackers bypass authentication and gain administrative access. This security flaw, rated critical, affects devices running firmware version 3.2.0.1 and below, and users should upgrade to version 3.2.1.0 or newer. A second vulnerability also exists, requiring the same firmware update, and users are urged to patch their devices immediately.
🐛 CrushFTP has revealed a zero-day vulnerability that allows hackers to gain admin access to servers through their web interface. The issue affects versions prior to CrushFTP v10.8.5 and v11.3.4_23, and organizations are advised to update their software to avoid exploitation. Users should also monitor for unusual activity and consider implementing security measures like IP whitelisting.
🛰️ ICS, OT & IoT
🇺🇸 🤖 The Trump administration's AI Action Plan encourages companies and governments to use AI for protecting critical infrastructure from cyberattacks while promoting "secure by design" technology standards. The plan aims to help organizations with limited resources adopt AI tools for cybersecurity but lacks details on funding and definitions of safety-critical systems. Critics worry the deregulatory approach could lead to harmful AI practices without sufficient safeguards.
🩹 Helmholz recently fixed serious vulnerabilities in their REX 100 industrial routers, which are used globally for remote network management. Three of these vulnerabilities are highly severe and could let attackers execute harmful commands. Experts warn that default credentials on these devices pose significant risks, especially since they are always connected to the vendor's cloud.
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Enjoying our newsletter? Forward it to a colleague—
it’s one of the best ways to support us.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.




Reply