We now have {{active_subscriber_count}} active subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
🇬🇧 UK telecom firm Colt confirmed hackers accessed some of its systems and stole data — Colt says the affected support systems are separate from customer networks, but some customer-related files may have been taken. Ransomware group WarLock claims about one million documents and is auctioning them on the dark web.
🇳🇱 🏎️ 📸 Speed cameras in several Dutch locations have been disabled due to a cyber attack. The incident has raised concerns about the security of such systems. Authorities are working to restore the cameras and investigate the attack.
🇺🇸 Inotiv, an American pharmaceutical company, suffered a ransomware attack on August 8, 2025, which encrypted some of its systems and data. The Qilin ransomware gang claimed responsibility and allegedly stole around 162,000 files. The attack disrupted Inotiv's business operations, and the company is working to restore affected systems with help from external security experts.
🇺🇸 A data breach at Allianz Life exposed the personal information of 1.1 million customers. Hackers accessed names, contact details, and Social Security numbers from a cloud database. Allianz Life, targeted by the hacking group ShinyHunters, is currently investigating the incident.
🇺🇸 Workday, the major HR technology provider, has confirmed a data breach where hackers stole personal information from a third-party database. The stolen data mainly includes contact details like names and email addresses, and it may be used for social engineering scams. Workday has not ruled out the possibility that customer information was affected but insists there was no access to customer-specific data.
→ More breaches:
🔗 Partners and Affiliates
With its user-friendly interface, robust security features, and commitment to privacy, NordVPN continues to be a popular choice for individuals seeking online protection and unrestricted internet access.
Special Offer: get up to 73% off with a 2-year plan!
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
🌍 Interpol-led Operation Serengeti 2.0 arrested over 1,200 suspected cybercriminals across Africa. Authorities seized $97.4 million and dismantled 11,432 malicious infrastructures tied to nearly 88,000 victims. The crackdown involved 18 African countries, the UK and private partners to fight ransomware, scams and BEC.

Figure: Operation Serengeti 2.0/interpol.int
🇰🇵 🇨🇳 Two hackers, Saber and cyb0rg, broke into a computer and realized it belonged to a hacker tied to the North Korean government — They found evidence of cyberespionage tools and attacks on South Korean and Taiwanese firms, and leaked the data to alert researchers and victims. They admit the intrusion was illegal but say exposing the operations was necessary, and they suspect the hacker may be based in China.
🇺🇸 ⚖️ Noah Michael Urban, 21, was sentenced to 10 years in federal prison for SIM‑swapping and related cybercrimes. He pleaded guilty to wire fraud and conspiracy and must pay about $13 million in restitution for thefts from victims and breaches of many companies. The attacks used SMS phishing to steal one‑time codes, and the case even involved a hack of a judge’s email.
🇷🇺 A Russian state-backed group called Static Tundra has been compromising network devices worldwide for years. They use a 2018 Cisco Smart Install bug on unpatched or end-of-life devices to steal data and maintain long-term access.
Victims include telecoms, universities, and manufacturers across many regions, and attacks on Ukraine rose after the war began.
🇺🇸 ⚖️ An Oregon man, Ethan J. Foltz, was arrested for allegedly running a massive botnet called "Rapper Bot" that conducted large-scale DDoS attacks, including one that disrupted Twitter in March 2025. Foltz and an accomplice reportedly rented out the botnet to extortionists, generating significant income while trying to avoid detection by law enforcement. He faces charges that could lead to a maximum of 10 years in prison if convicted.
🤑 A hacker is selling 15.8 million PayPal email-password pairs on the Dark Web for $750. The data likely comes from malware on users' devices, not a breach of PayPal itself.
🇬🇧 ⚖️ A 26-year-old man from the UK, Al-Tahery Al-Mashriky, was sentenced to 20 months in prison for hacking over 3,000 websites and stealing personal data from millions of Facebook users. He pleaded guilty to multiple charges after being arrested in 2022, and his attacks caused significant disruption to various organizations. Al-Mashriky was linked to extremist groups and used his hacks to promote political messages.
🇺🇸💰 The U.S. Department of Justice has seized over $2.8 million in cryptocurrency from Ianis Aleksandrovich Antropenko, a ransomware operator linked to the Zeppelin ransomware. Antropenko used this malware to extort businesses and individuals by encrypting their data and demanding ransom payments. He faces multiple charges, including computer fraud and money laundering, for his criminal activities.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests (and don’t forget to star the project); Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇬🇧 The U.K. government has dropped its plan to force Apple to weaken encryption and create a backdoor for accessing user data. This decision follows pushback from U.S. officials who wanted to protect Americans' civil liberties. Apple previously disabled its Advanced Data Protection feature in the U.K. due to these government demands.
🇩🇪 Germany's Federal Supreme Court has reopened a case that could make ad blockers illegal, following a lawsuit from Axel Springer against Adblock Plus. The court will review whether ad blockers violate copyright by altering website code, which could impact other browser extensions as well. Mozilla warns that this situation may limit user choices and affect the freedom of browser developers and extension creators.
🔗 Partners and Affiliates

🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
🦠 MALWARE & THREATS
📧 IBM X-Force researchers found QuirkyLoader, a new email-spread loader that delivers information stealers and remote-access trojans. It uses DLL side-loading and process hollowing to inject payloads like Agent Tesla, AsyncRAT, and Snake Keylogger. Attackers also use hidden QR codes and advanced phishing kits to steal logins and bypass defenses.
🔙 🚪 Attackers use fake CAPTCHA pages called ClickFix to trick users into running a malicious PowerShell downloader. That access lets actors deploy the CORNFLAKE.V3 backdoor in Node.js or PHP to persist, steal credentials, and run more malware.
🎣 Hackers used legitimate office.com redirects and a custom Microsoft ADFS tenant to send users to a phishing page that stole Microsoft 365 logins — The attack started from a malicious sponsored Google ad and used a trusted domain with conditional redirects to evade detection and bypass MFA.
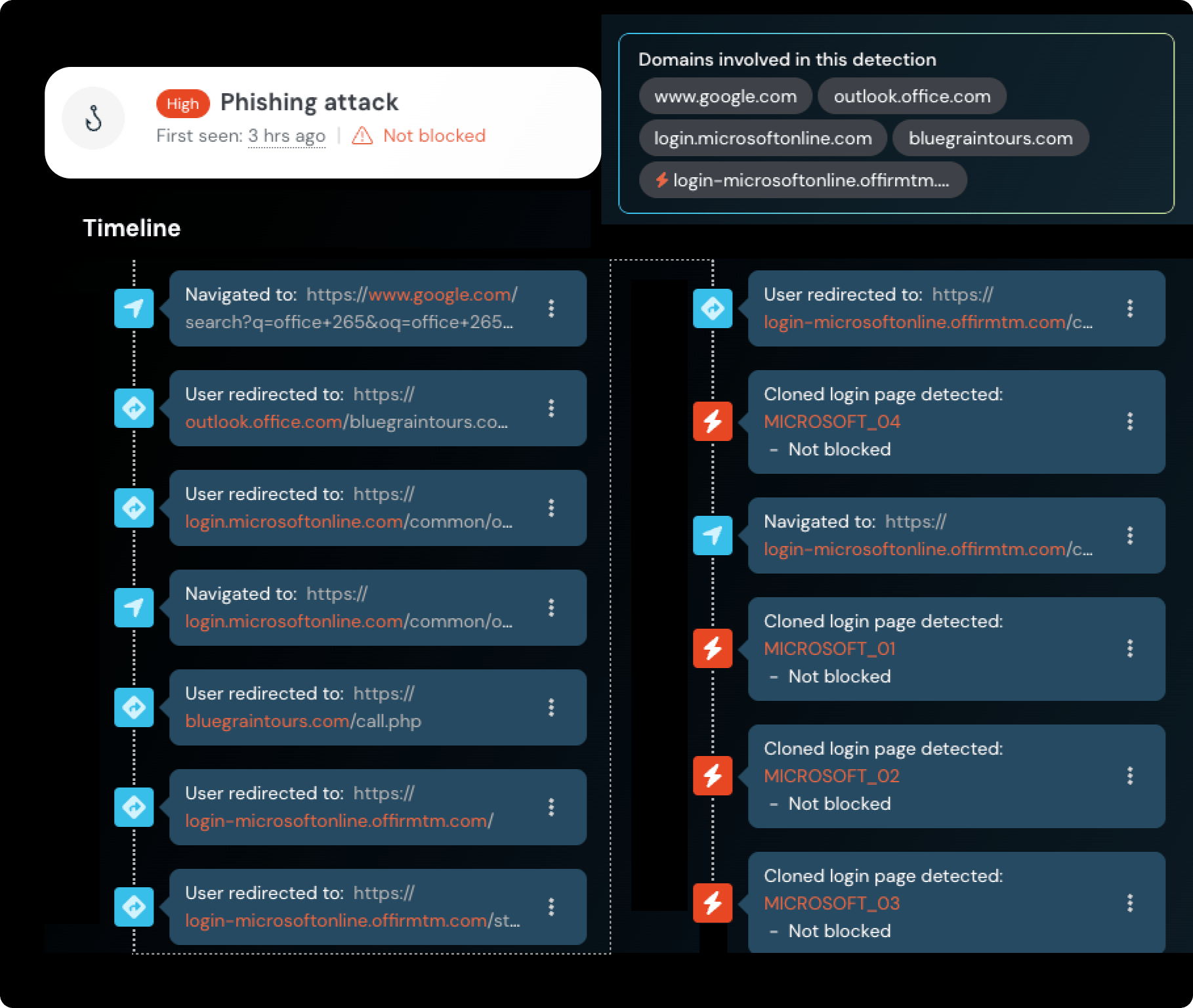
Figure: Timeline from the detection event/Pushsecurity.com
🔬 Microsoft has analyzed PipeMagic, a modular backdoor used in ransomware attacks this year. This malware disguises itself as a ChatGPT application and gives attackers persistent access to infected systems. It employs various modules for tasks like communication and execution, making it hard to detect and analyze.
©️ 🎣 The Noodlophile malware campaign is using spear-phishing emails that pretend to be copyright infringement notices to target businesses in various regions. These emails contain links to malicious files that install the malware, which can steal sensitive information from web browsers. The attackers are continuously improving the malware's capabilities, making it a growing threat to companies with a strong social media presence.
🇰🇷 🇰🇵 🇨🇳 A state-sponsored campaign is targeting foreign embassies in South Korea with XenoRAT malware through spearphishing emails. Researchers believe the attacks, which began in March, show signs of both North Korean and Chinese involvement. The emails often impersonate diplomats and contain malicious files disguised as legitimate documents.
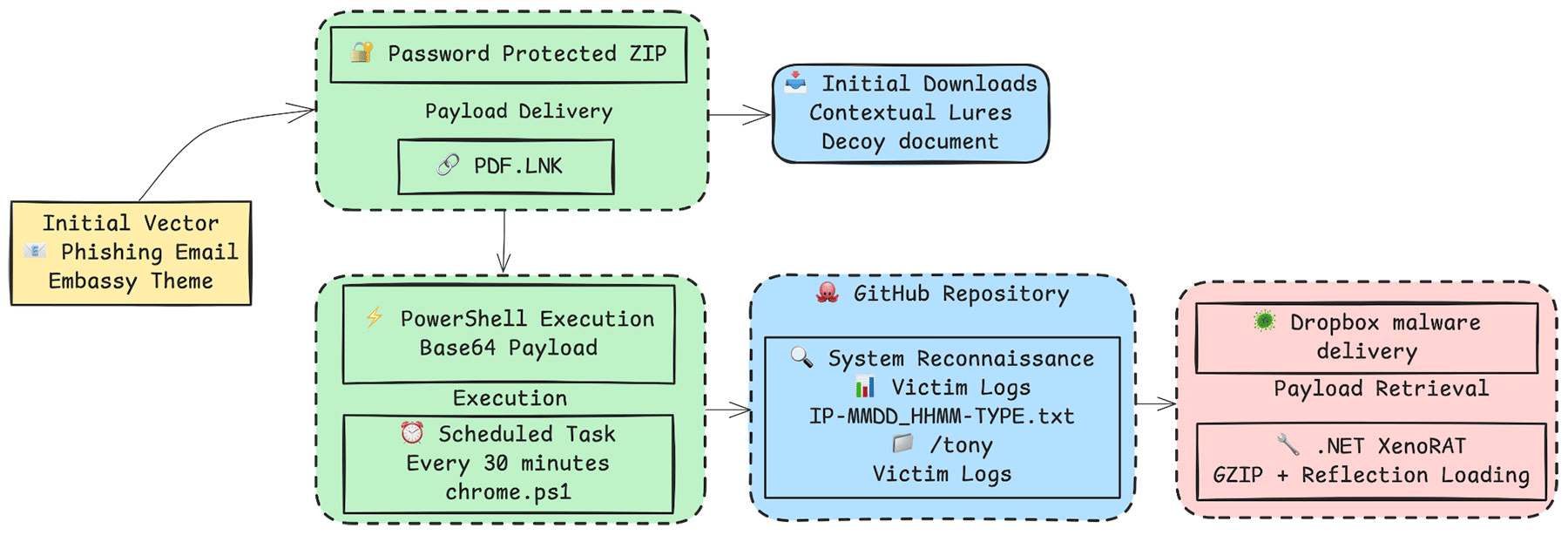
Figure: Campaign infection chain/Trellix.com
🐍 Cybersecurity researchers found a malicious Python package called termncolor on the PyPI repository that uses a harmful dependency to execute code and maintain persistence on systems. Similarly, malicious npm packages were discovered that can steal sensitive information and are disguised as legitimate tools. Both incidents highlight the growing risks of supply chain attacks in software development.
🤖 🧰 AI, CRYPTO, TECH & TOOLS
🇦🇪 🛠️ A new startup in the UAE, Advanced Security Solutions, is offering up to $20 million for hacking tools that can exploit any smartphone. They aim to provide these tools to government agencies and intelligence services worldwide. The company is attracting attention for its high bounties, but it's unclear who runs it or who its customers are.

Figure: Bounties offered by Advanced Security Solutions for zero-days in operating systems/TechCrunch
👀 Okta has open-sourced a collection of Sigma-based queries to help Auth0 users detect account takeovers and suspicious behavior. This new Customer Detection Catalog allows security teams to easily analyze logs and improve threat detection capabilities. Users can access the repository on GitHub, customize the rules, and contribute to the community's security efforts.
🐛 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
🐛 ✅ MITRE revised its Most Important Hardware Weaknesses list to 11 items, adding new entries while keeping five from 2021. The top issue is CWE-226 — sensitive data not cleared before resource reuse — and the list highlights resource reuse, debug bugs, and fault injection. Experts warn hardware flaws embed in silicon, so they must be fixed early with vendor transparency.
🔓 A security researcher found vulnerabilities in Intel's internal websites that exposed the personal information of 270,000 employees — Although sensitive data like Social Security numbers was not leaked, details such as names and email addresses were accessible. Intel stated there was no breach and took immediate action to fix the issues after being notified.
💥 A new exploit targets SAP NetWeaver instances by combining two serious vulnerabilities that allow attackers to execute code. These flaws, identified as CVE-2025-31324 and CVE-2025-42999, had already been exploited before patches were released. Organizations are urged to ensure their systems are updated to prevent attacks from exploiting these vulnerabilities again.
🛰️ ICS, OT & IoT
🛜 Researchers from the Singapore University of Technology and Design have revealed a new 5G attack called Sni5Gect that does not need a malicious base station. This attack allows hackers to intercept and inject messages into 5G communications without the victim's device credentials. The Sni5Gect framework has been tested successfully on several smartphones and is now available as open source.

Figure: Sni5Gect framework
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Enjoying our newsletter? Forward it to a colleague—
it’s one of the best ways to support us.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.