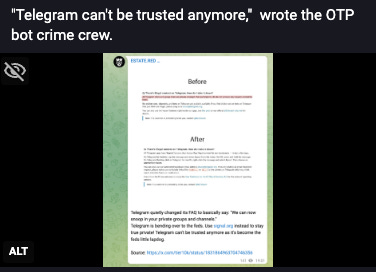
[InfoSec MASHUP] 37/2024
Meta fixes WhatsApp's "View Once" feature vuln.; U.S. elections still target of nation state threat actors; New sextortion scams using spouse's name; Patch Tuesday; Fortinet confirms customer breach;
Welcome to the 45 new members from the last 30 days! This newsletter now has 1,539 subscribers.
Keep reading with a 7-day free trial
Subscribe to X’s InfoSec Newsletter to keep reading this post and get 7 days of free access to the full post archives.