We now have {{active_subscriber_count}} active subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
💰 💰 ShinyHunters says 1.5 billion Salesforce records from 760 companies were stolen. Attackers used stolen Salesloft Drift OAuth tokens to exfiltrate data and hunt for credentials. The FBI warned about the groups and Salesforce urges MFA, least privilege, and careful app management.
🇬🇧 Jaguar Land Rover has extended its production shutdown by a week after a cyberattack disrupted its systems. The attackers stole some data and a group calling itself "Scattered Lapsus$ Hunters" posted screenshots and claimed responsibility. JLR is still investigating and has not officially identified the culprits or confirmed the full impact.
🧱 SonicWall said attackers accessed its MySonicWall cloud portal and exposed backup firewall configuration files for less than 5% of devices. The files included encrypted passwords and detailed settings that could help attackers, so SonicWall disabled the backup feature and opened an investigation. Affected customers were notified and told to reset credentials, remediate, and monitor systems while SonicWall works with responders and law enforcement.
🇺🇸 🇨🇦 Tiffany & Co. says hackers accessed its systems around May 12, 2025 — They stole gift card data and customer contact details (names, emails, addresses, phone numbers, sales, card numbers and PINs). More than 2,500 U.S. and Canadian customers were affected, and it’s unclear if this is linked to the recent Salesforce/Scattered Spider attacks.
🇫🇷 Kering, which owns Gucci, Balenciaga and other luxury brands, confirmed a data breach — Hackers stole names, emails, phone numbers, home addresses and purchase totals, but not credit card numbers. The group ShinyHunters claims 7.4 million email addresses were taken, and Kering says it has contacted affected customers.
→ More breaches:
🔗 Partners and Affiliates
With its user-friendly interface, robust security features, and commitment to privacy, NordVPN continues to be a popular choice for individuals seeking online protection and unrestricted internet access.
Special Offer: get up to 73% off with a 2-year plan!
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
❌ Microsoft and Cloudflare disrupted RaccoonO365 and seized 330+ domains — The service rented easy phishing kits that stole over 5,000 credentials and targeted healthcare. Microsoft says the suspected leader is Joshua Ogundipe and has notified law enforcement.
🇺🇸 ⚖️ Conor Brian Fitzpatrick, known as "Pompompurin" was resentenced to three years in prison for running BreachForums. He pleaded guilty to access device fraud and possession of child sexual abuse material after an earlier 17-day sentence was overturned on appeal. Courts also ordered forfeiture of domain names, devices, and cryptocurrency tied to the site, which hosted billions of stolen records.
🇮🇱 💰 Israel ordered the seizure of 187 cryptocurrency wallets it says belong to Iran’s IRGC. Blockchain firm Elliptic says those wallets received about $1.5 billion over time but now hold only $1.5 million. Experts warn ownership is unclear and the addresses may be tied to exchanges or other services.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests (and don’t forget to star the project); Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🗳️ Google quietly urged people and funded groups to oppose Assembly Bill 566, a California bill that would let browsers tell websites not to share users' data. It hid its role by using front groups like the Connected Commerce Council and the California Chamber of Commerce. The secretive campaign raised worries about money and influence, but the bill passed anyway.
🔗 Partners and Affiliates

🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
🦠 MALWARE & THREATS
🎠 🏨 The threat actor TA558 (RevengeHotels) used AI-generated scripts to deploy Venom RAT against hotels in Brazil and Spanish-speaking markets. Phishing emails in Portuguese and Spanish trick staff into running JavaScript and PowerShell loaders that download the RAT to steal credit card data. Venom RAT has strong persistence and anti-kill features, can disable defenses and spread via USB, and LLMs helped create the malicious code and lures.
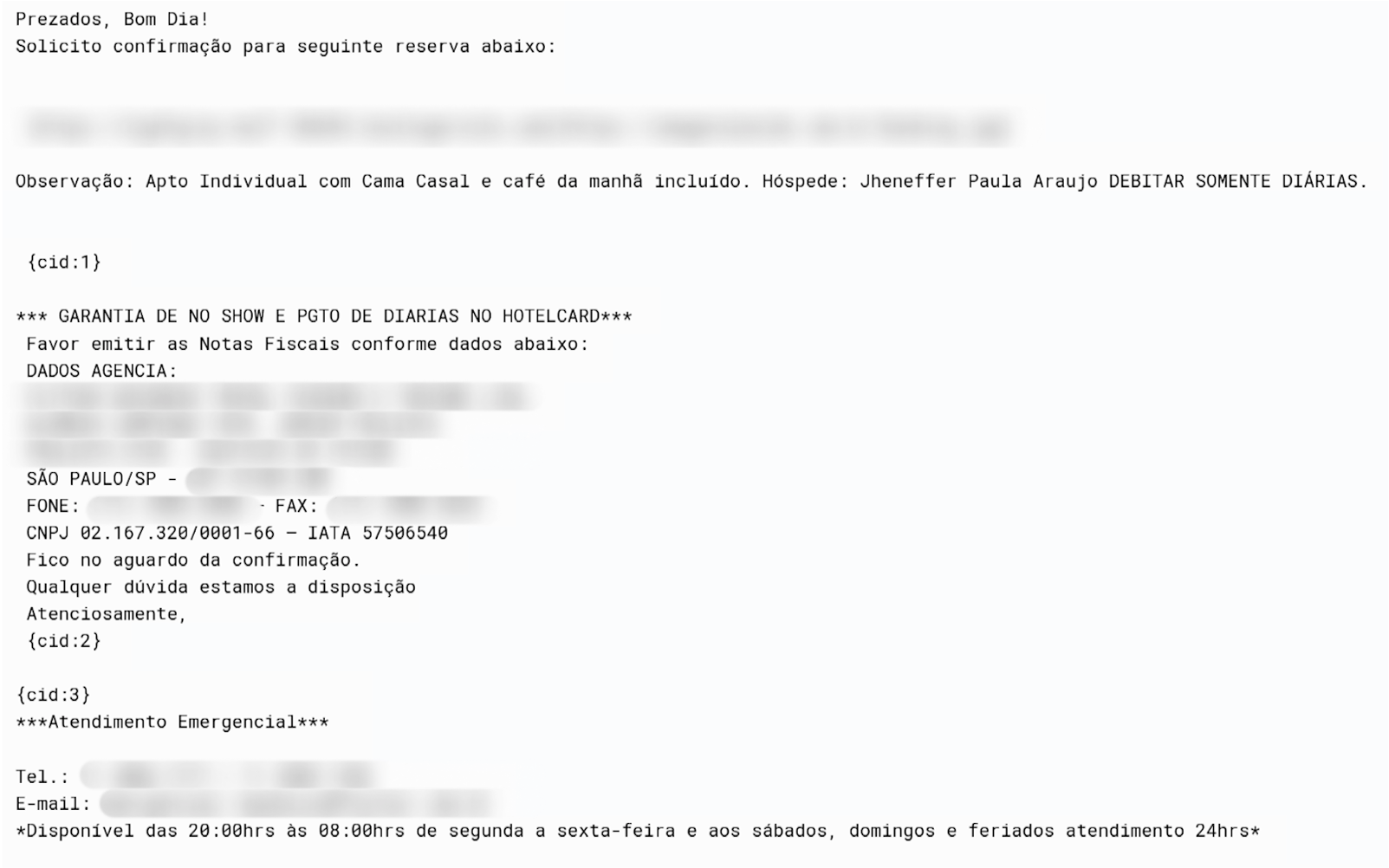
Figure: Example of a phishing email about a booking confirmation/securelist.com
🤖 🛍️ A massive ad fraud operation called SlopAds used 224 Android apps on Google Play to generate about 2.3 billion ad requests per day. The apps hid malicious code with obfuscation and steganography to assemble a "FatModule" that used hidden WebViews to fake ad impressions and clicks. Google removed the apps and updated Play Protect, but researchers warn the attackers will likely try again.
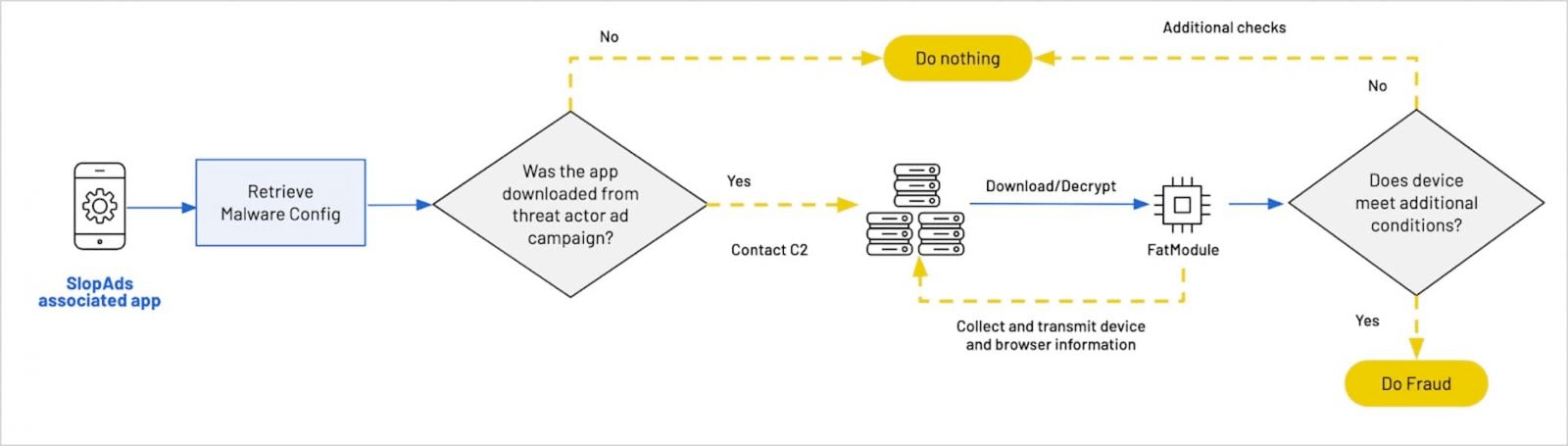
Figure: SlopAds ad fraud malware workflow/HUMAN SATORI
🪱 ♾️ A self-replicating worm named Shai-Hulud infected at least 187 JavaScript packages on NPM — It steals developer tokens and keys, posts them publicly on GitHub, and uses stolen NPM tokens to inject itself into other packages. Researchers call it a serious supply-chain attack and urge phish-proof 2FA and stricter publishing controls.
🪱 🇨🇳 China-aligned Mustang Panda is using a new USB worm called SnakeDisk to drop the Yokai backdoor on devices with Thailand-based IPs. Researchers also found updated TONESHELL variants that hide in normal network traffic and open two reverse shells. The campaign shows a focused, evolving toolkit reused across multiple malware families targeting Thailand.
🎠 🇨🇳 Attackers used SEO poisoning and lookalike sites (including GitHub Pages) to trick Chinese-speaking users into downloading trojanized installers. The installers drop RATs like HiddenGh0st, Winos (ValleyRAT) and a new kkRAT that spy on users, steal data, and replace cryptocurrency addresses. The malware evades analysis, disables antivirus (via vulnerable drivers and DLL sideloading), keeps persistence, and connects to remote command-and-control servers.
🤖 🧰 AI, CRYPTO, TECH & TOOLS
🇺🇸 🤖 Salesforce has launched Missionforce, a new business unit focused on national security. It will use AI, cloud, and platform technology to improve personnel, logistics, and decision-making for defense. The move follows a broader trend of tech companies offering AI services to the U.S. government.
🔐 GitHub is adding a hybrid post-quantum SSH key exchange (sntrup761x25519 + X25519) to protect Git traffic from future quantum attacks. This change affects SSH only, not HTTPS, and will roll out on September 17, 2025 for github.com and non‑US Enterprise Cloud (the US/FIPS region is excluded). Up‑to‑date clients (e.g., OpenSSH 9.0+) will use it automatically; older clients will fall back to current algorithms and keep working but without post‑quantum protection.
🐛 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
🔥 🧱 WatchGuard released updates to fix a critical remote code execution bug (CVE-2025-9242) in Firebox firewalls. The flaw is an out-of-bounds write in the Fireware iked process that affects devices using IKEv2 VPN or with certain past VPN configurations. Administrators should apply the patches or follow WatchGuard’s workaround now to avoid compromise.
🐛 Researchers from ETH Zurich and Google created Phoenix, a Rowhammer attack that defeats DDR5 protections. They caused bit flips on 15 SK Hynix DDR5 modules by reverse‑engineering refresh defenses. Those flips let them gain root on a default PC, and tripling refreshes blocks the attack but hurts performance.
🛰️ ICS, OT & IoT
🛜 The Pixie Dust Wi‑Fi attack from 2014 can still break many routers and extenders — NetRise tested 24 device models and found only four patched, while the rest—many still sold—had WPS PINs recoverable in seconds. Insecure firmware and hidden WPS flaws leave millions of devices quietly exposed.
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Enjoying our newsletter? Forward it to a colleague—
it’s one of the best ways to support us.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.