We now have {{active_subscriber_count}} active subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
✈️ A cyberattack disrupted check-in and boarding systems at major European airports, forcing manual check-ins and causing delays and some cancellations. The problem hit systems run by Collins Aerospace, a third-party provider, not the airlines or airports themselves. Experts warn this shows the risk of shared vendors and supply-chain attacks, while the attacker remains unknown.
🇬🇧 An April Scattered Spider hack forced Co-op to shut systems and caused a £80m operating loss ($107m) — Hackers stole data on all 6.5 million members and disrupted trading and stock availability. Co-op says it has £800m in liquidity and four suspects were arrested.
🇺🇸 🇸🇪 Volvo Group North America says employee data was exposed after supplier Miljödata was hit by a ransomware attack. Hackers stole names, emails, addresses, phone numbers and Social Security numbers. Volvo is offering 18 months of free identity protection and credit monitoring to affected people.
🇺🇸 🎰 Boyd Gaming suffered a cyberattack that stole data, including employee and some other personal information. The company hired outside cybersecurity experts, notified law enforcement, and is informing affected individuals and regulators. Boyd says operations were not affected, it does not expect material financial harm, and insurance should cover the costs.
🇬🇧 ⏸️ Continued Pause — Jaguar Land Rover paused production at its U.K. factories after a cyberattack that stole company data. The shutdown, now in its third week, will continue at least until October 1 but the company gave no firm restart date. Suppliers warn the prolonged halt could push them toward bankruptcy.
🇺🇸 Stellantis says customer personal data was stolen — The breach hit a third-party platform for North American customer service and reportedly took contact information. Reports tie the hack to a Salesforce breach by ShinyHunters, who claim 18 million records.
🔗 Partners and Affiliates
With its user-friendly interface, robust security features, and commitment to privacy, NordVPN continues to be a popular choice for individuals seeking online protection and unrestricted internet access.
Special Offer: get up to 73% off with a 2-year plan!
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
🇨🇳 Recorded Future says a Chinese state-backed hacking group called RedNovember (aka TAG-100/Storm-2077) is targeting governments and private organizations worldwide. From mid-2024 to mid-2025 they exploited internet-facing appliances and used open-source tools (Pantegana, Spark RAT) and Cobalt Strike to gain and maintain access. Victims include defense and aerospace firms, law firms, government ministries, and contractors across the US, Asia, Latin America, and other regions.
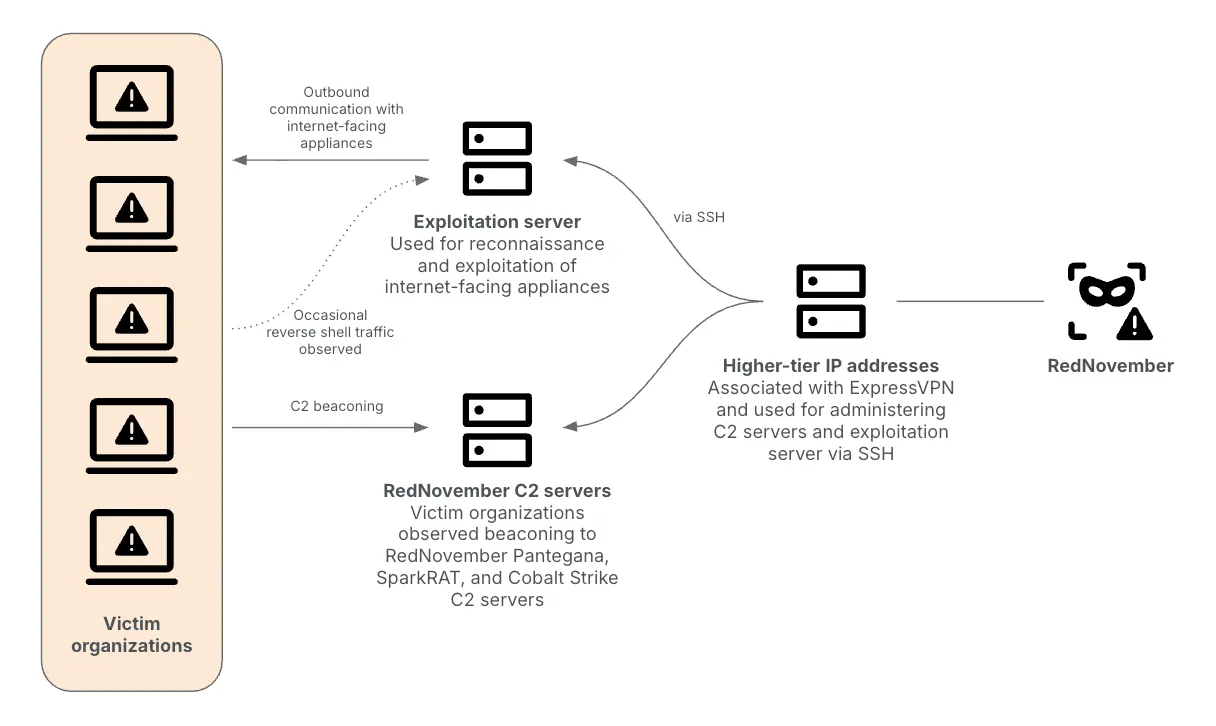
Figure: Overview of RedNovember operations/Recorded Future
🇺🇸 🔓 CISA says hackers breached an unnamed U.S. federal agency by exploiting an unpatched GeoServer flaw (CVE-2024-36401). The attackers used web shells, brute force, and lateral movement to compromise multiple servers and stayed undetected for three weeks. CISA urges rapid patching of known exploited flaws and stronger EDR monitoring and incident response.
🇺🇸 📡 The U.S. Secret Service shut down a massive SIM farm near the UN summit in New York. The network used 300+ servers and 100,000 SIM cards to cripple telecoms, launch denial-of-service attacks, and enable untraceable communications. Investigators found links to nation-state actors and are probing who planned the disruption.
🇺🇸 The FBI warns criminals are spoofing the official IC3 website to steal personal and financial data. They use misspellings, different top-level domains, and fake search results to trick people. The FBI says type www.ic3.gov, avoid sponsored links, never pay or share sensitive information, and report suspicious sites.
🇬🇧 ⚖️ Two UK teens, Thalha Jubair (19) and Owen Flowers (18), were arrested for alleged links to the Scattered Spider cybercrime group. Authorities say Jubair helped carry out at least 120 ransomware and extortion attacks from 2022–2025 that netted over $115 million. Police seized millions in cryptocurrency and have filed charges in the U.K. and U.S.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests (and don’t forget to star the project); Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇮🇷 🇮🇱 Iran released documents it says show secret details of Israel’s nuclear program and personal data on 189 experts. Tehran calls it a major intelligence victory and says insiders leaked the files, but the materials have not been independently verified. Analysts say it is likely propaganda to pressure Israel and could raise tensions at the UN and across the region.
🇺🇸 🇮🇱 Microsoft stopped some cloud services to an Israeli military unit after a report said they used the tech to track Palestinians' phone calls. The company found evidence supporting the report and acted after employee protests. This move follows a UN claim that Israel committed genocide against Palestinians in Gaza.
🇺🇸 Senate Democrats say the Musk-created team called DOGE at three federal agencies broke cybersecurity and privacy rules and put Americans’ data at risk. They cite a risky Numident upload, a private Starlink network, and attempts to pool agency data in an unmonitored cloud that could be exposed to foreign adversaries. Agencies dispute the report, but it urges stripping DOGE’s access to sensitive data until it meets federal security and privacy rules.
🔗 Partners and Affiliates

🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
🦠 MALWARE & THREATS
🧱 🇺🇸 Researchers found a stealthy, advanced malware campaign called Brickstorm that has lived inside U.S. networks for long periods. The hackers target legal, tech, and security-as-a-service firms to steal source code and intellectual property and to find zero-day flaws to attack downstream customers. Mandiant and Google released a scanner and warned many organizations may already be or become compromised.
🔙 🚪 Researchers discovered YiBackdoor, a new malware that shares major code with IcedID and Latrodectus and likely comes from the same developers. YiBackdoor can run commands, steal system data and screenshots, inject into svchost.exe, load plugins, evade analysis, and persist via the Windows Run registry. Zscaler also found new ZLoader versions with stronger obfuscation and improved C2 networking using DNS and WebSockets in targeted attacks.
🧨 DDoS Service Lets Customers Self-Manage Attacks — ShadowV2 infects misconfigured Docker containers and runs its C&C from GitHub CodeSpaces. It builds custom containers that run a stealthy Go-based HTTP-flood malware with evasion tricks. Customers can rent access via an authenticated API and UI to launch their own DDoS attacks.
🍎 Search engine ads are impersonating services to trick Mac users into downloading fake apps. Fake LastPass macOS ads led to malicious GitHub pages that installed Atomic Stealer (also called Amos Stealer). LastPass detected the campaign, took down the pages, and shared indicators to help protect users.
🇰🇵 North Korea–linked hackers used fake job sites and ClickFix lures to deliver BeaverTail and InvisibleFerret malware to crypto, retail, and marketing job applicants. They switched to compiled binaries and password‑protected archives, expanding beyond developers to less technical targets. Other DPRK groups also abused GitHub, ChatGPT deepfakes, and new ransomware and stealers, showing a broader evolution of tactics.

Figure: Infection chain/GitLab
🤖 🧰 AI, CRYPTO, TECH & TOOLS
💸 Two malicious Rust crates posing as fast_log were downloaded 8,424 times and stole Solana and Ethereum private keys — They scanned .rs source files at runtime and sent keys to a fake Cloudflare Workers endpoint. Crates.io removed the packages and disabled the accounts, showing how typosquatting can breach the software supply chain.
☁️ 🏗️ The Cloud Security Alliance published a SaaS Security Controls Framework to standardize customer-facing controls. It asks SaaS vendors to expose consistent settings so customers can configure and protect their data. That should reduce complexity and risk and make compliant vendors easier to buy from.
🇪🇺 European police arrested five suspects in a crypto investment scam — The ring stole more than €100 million from over 100 victims in 23 countries. Investigators say the fraud ran since 2018, used fake platforms, and laundered funds through Lithuanian bank accounts.
🐛 📋 MCP is the leading standard for agentic AI but it has many exploitable flaws — Adversa published a ranked Top 25 MCP vulnerabilities list; prompt injection is the biggest risk. The guide offers immediate fixes, layered defenses, a three-month mitigation timeline, and monthly updates.
🐛 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
😱 Security teams are alarmed by a maximum-severity deserialization bug in GoAnywhere MFT — Researchers say they have evidence of active exploitation, but the vendor has not confirmed it. Exploitation appears to need a private key whose source is unknown, raising fears of leaked keys and hampering defenders.
🔓 ☁️ Researchers showed a practical attack that combines L1TF and half-Spectre to leak memory from public cloud VMs. They used it to steal an Nginx TLS key on a Google Cloud node in about 14 hours and received $151,515 from Google. The attack bypasses common mitigations and shows cloud providers need stronger isolation or secret-free hypervisors.
🩹 Supermicro patched two BMC vulnerabilities that could let attackers install malicious firmware and fully control servers. Binarly found the original patch was bypassed and discovered a second flaw that can defeat the Root of Trust. Supermicro issued new fixes and says no in-the-wild exploitation has been seen, but the risks are severe.
🛰️ ICS, OT & IoT
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Enjoying our newsletter? Forward it to a colleague—
it’s one of the best ways to support us.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.




