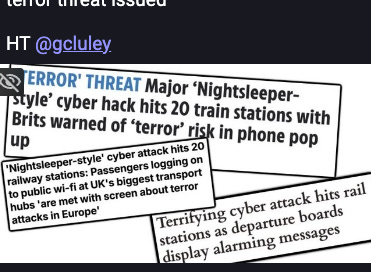
[InfoSec MASHUP] 39/2024
Microsoft's security reboot; Kaspersky deletes itself; Deloitte breached but clients are safe; Tor Project merges with Tails; Critical vulnerability in the NVIDIA Container Toolkit;
Welcome to the 32 new members from the last 30 days! This newsletter now has 1,549 subscribers.
Keep reading with a 7-day free trial
Subscribe to X’s InfoSec Newsletter to keep reading this post and get 7 days of free access to the full post archives.