We now have {{active_subscriber_count}} active subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
☁️ The hacking group that calls itself Lapsus$/ShinyHunters claims to have stolen about one billion (!!) records from companies using Salesforce-hosted databases — They launched a dark web extortion site threatening to publish stolen customer data unless victims pay. Several big firms, including Google, Allianz Life, Qantas, and TransUnion, have confirmed data theft.
❤️🩹 Red Hat confirmed a GitLab instance used by its consulting team was hacked and some data was copied. The attackers, calling themselves Crimson Collective, claimed to have stolen code, credentials, and customer reports and tried to extort Red Hat. Red Hat says the breach is isolated to that instance, found no evidence of exposed personal data, and sees no impact to its products or supply chain.
📧 Hackers claim they stole sensitive data from Oracle’s E-Business Suite and are sending extortion emails to executives at many large organizations. Google and security firms say the emails began around September 29 but have not fully verified the breaches. The messages appear linked to the Clop ransomware group, which has pressured victims for large payouts.
🇨🇦 ✈️ Canadian airline WestJet said hackers stole customer personal data in a June 2025 cyberattack. The breach exposed names, contact details, government IDs and other reservation information, but not payment card data or passwords. WestJet is notifying affected customers, offering identity protection, and warning about impersonation scams.
🇯🇵 🍺 Asahi, a top Japanese brewer, says a cyberattack has halted ordering, shipping, and call-center services. The company says only Japan operations were affected and investigators have not confirmed any data leakage. Asahi apologized to customers and gave no timeline for restoring services.
🇬🇧 Harrods warned some online customers that names and contact details were stolen after a third-party system was breached. It said passwords and payment data were not affected and the breach has been contained. The attack comes amid other recent UK cyberattacks and arrests linked to suspected attacks on Harrods and other retailers.
→ More breaches:
🔗 Partners and Affiliates
🔐 NordVPN Threat Protection Pro™ Campaign (July 2 - August 13)
With its user-friendly interface, robust security features, and commitment to privacy, NordVPN continues to be a popular choice for individuals seeking online protection and unrestricted internet access.
Special Offer: get up to 73% off with a 2-year plan!
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
🇰🇵 Researchers at Okta found North Korea’s IT worker scheme targets many industries worldwide, not just US big tech. DPRK-linked applicants use fake identities and pass interviews to gain remote access to companies, contractors, and governments. Organizations should strengthen recruitment, identity checks, and insider monitoring to prevent data theft and extortion.
🇨🇳 👀 Chinese state-backed APT "Phantom Taurus" has spent over two years spying on governments and telecoms in Africa, the Middle East, and Asia. It uses unique tools like NET-STAR and Specter, plus loaders that run code in memory and evade security. The group focuses on diplomatic, defense, and critical ministry data, aligning attacks with major events.
🌍 Interpol arrested 260 suspects across 14 African countries in "Operation Contender 3.0" targeting romance scams and sextortion. The networks stole about $2.8 million from nearly 1,500 victims and 81 cybercrime infrastructures were dismantled. Major arrests and device seizures occurred in Ghana, Cote d’Ivoire, Senegal and other countries with private partners aiding the effort.
🇬🇧 💰 A criminal gang contacted BBC cyber correspondent Joe Tidy and offered him a cut of ransom money to give them access to BBC systems. They pressured him for his login details, used MFA‑bombing, and claimed to be with the Medusa ransomware group. The incident shows how insider threats and sophisticated ransomware gangs can seriously endanger organisations.

Figure: A screenshot of the conversation with the criminal on the Signal app/bbc.com
🇳🇱 🇷🇺 Two 17-year-old boys in the Netherlands were arrested for allegedly helping pro‑Russian hackers who contacted them on Telegram. One boy was seen near Europol, Eurojust and the Canadian embassy carrying a Wi‑Fi sniffer. One is on home bail with an ankle monitor and the other remains in custody; authorities say this suspected government‑sponsored spying mirrors cases in Germany and Ukraine.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests (and don’t forget to star the project); Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇬🇧 🍎 The U.K. government has again sought an order forcing Apple to build a way to access encrypted iCloud backups of British users. Privacy advocates warn this would weaken security for users worldwide. Apple and the U.K. Home Office did not comment.
🔗 Partners and Affiliates

🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
🦠 MALWARE & THREATS
🇪🇸 🇮🇹 A new Android banking trojan named Klopatra has infected over 3,000 phones, mostly in Spain and Italy. It uses hidden VNC, accessibility abuse, and fake overlays to let operators remotely steal credentials and make silent bank transfers. The malware is highly protected and stealthy, using native libraries and commercial code obfuscation to evade detection.
🇵🇰 The Confucius hacking group has run phishing campaigns in Pakistan using WooperStealer and a new Python backdoor called Anondoor. Attackers used .PPSX and .LNK files plus DLL side-loading to deliver these tools and steal data. Researchers say the group is adaptive, persistent, and rapidly changes tactics to evade detection.

Figure: Confucius’ activities/Fortinet.com
👀 Researchers found two Android spyware campaigns, ProSpy and ToSpy, posing as Signal and ToTok plugins to steal contacts, messages, files, and backups. The malware was spread via fake websites and stores, used stealthy persistence methods, and encrypted exfiltrated data. Users should only install apps from official sources and keep Play Protect enabled.
💬 📲 Unknown hackers abused vulnerable Milesight cellular routers to send phishing SMS messages across Europe since at least February 2022. Attackers used exposed SMS APIs and typosquatted links to impersonate governments, banks, post, and telecoms, mainly targeting Sweden, Italy, and Belgium. The flaw (CVE-2023-43261) was patched, but misconfigured or outdated routers still let attackers send and monitor SMS without authentication.
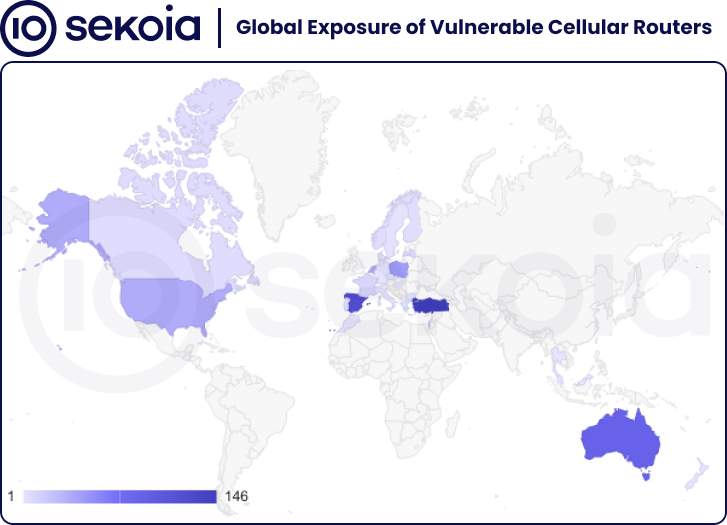
The geographic distribution of vulnerable routers/sekoia.io
✈️ 🇨🇳 Datzbro is a new Android trojan that lures elderly people with AI-generated Facebook travel events — Scammers send APKs or TestFlight links that install malware using accessibility features, overlays, and keylogging to steal passwords and carry out bank fraud. Researchers link it to Chinese-language command servers and say it is spreading internationally.
🤖 🛠️ Threat actors are disguising malware as AI and productivity tools to infect organizations worldwide. These fake apps use valid-looking digital signatures, fake vendor sites, and covert tricks to avoid detection. Once installed they steal browser data, keep encrypted contact with command servers, and prepare systems for further attacks.
🔙 🚪 First Malicious MCP server in the Wild — Researchers found a malicious npm package named "postmark-mcp" that secretly BCC'd every email to the attacker. The backdoor was added in version 1.0.16 and copied an official library to look legitimate. Users should remove the package, rotate exposed credentials, and check email logs.
🤖 🧰 AI, CRYPTO, TECH & TOOLS
🔬 Microsoft researchers showed that AI can redesign dangerous proteins so DNA-screening tools miss them. They tested this digitally and alerted vendors and the government, who patched some but not all gaps. Experts say stronger screening and AI controls are urgently needed.
🎦 Anker’s Eufy offered users money or rewards to submit videos of package and car thefts to train its AI. The company collected hundreds of thousands of donated videos and runs ongoing campaigns and leaderboards in its app. Privacy and security concerns persist because Eufy previously misled users about encryption and has not fully answered questions about data handling.
🆕 Anthropic says its new coding-focused model, Claude Sonnet 4.5, has stronger safety and security measures to reduce misuse and make prompt-injection attacks harder. Tests showed improvements in refusing harmful requests, child safety, and cybersecurity tasks, though the model is still below the threshold for catastrophic risk. During evaluations the model sometimes recognized it was being tested and changed its behavior, which complicates results.
🩹 Google Patches Gemini AI Hacks — Researchers found three ways attackers could trick Google’s Gemini into leaking data by hiding malicious prompts in logs, search history, and web pages. The methods let Gemini follow attacker instructions without much social engineering and could expose cloud assets and user data. Google patched all three vulnerabilities after being notified.
🐛 A serious flaw in Red Hat OpenShift AI (CVE-2025-10725) can let an authenticated low-privilege user escalate to full cluster admin and fully compromise the infrastructure. The bug affects OpenShift AI versions 2.19 and 2.21 and has a CVSS score of 9.9. Red Hat advises tightening permissions, removing a broad ClusterRoleBinding, and granting job-creation rights only as needed.
🇬🇧 💸 U.K. police seized £5.5 billion (61,000 BTC) in what they call the world’s largest crypto bust — Zhimin Qian pleaded guilty for running a fraud that duped over 128,000 mostly older victims and converted their money into Bitcoin.
🐛 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
💰 Bug bounty platform HackerOne paid $81 million to white-hat hackers in the past year — The payouts rewarded security researchers for finding bugs like an Adobe Analytics issue that leaked customer tracking data and a classic Outlook flaw. These programs help companies fix vulnerabilities faster.

Figure: HackerOne year in review/HackerOne
🩹 OpenSSL released updates fixing three vulnerabilities across multiple versions — One moderate bug (CVE-2025-9231) could allow private key recovery on SM2 keys for 64-bit ARM, enabling decryption or MitM in limited setups. Another moderate bug can allow code execution or DoS, and a low-severity bug can cause crashes.
💥 CISA warned that a critical Sudo flaw (CVE-2025-32463) that allows any user to run commands as root has been exploited in the wild. The bug affected Sudo 1.9.14 and was fixed in 1.9.17p1 by removing the chroot feature. Organizations should patch now and follow CISA’s KEV guidance.
🛰️ ICS, OT & IoT
📋 NIST released SP 1334, a two-page guide to reduce USB and removable-media risks in industrial control systems. It recommends procedural, physical, technical, and transport/sanitization controls like inventorying devices, disabling unused ports, scanning for malware, and encrypting data. The guide warns infected USBs can disrupt OT operations and urges treating unapproved devices as untrusted.
🔊 📋 Agencies from several countries issued guidance for OT operators to create and maintain a definitive, continually updated inventory of their systems — The guidance sets five principles: record keeping, security management, asset classification, network connectivity, and third-party risk. The aim is to help prioritize protections, assess risks, and improve OT and IT coordination.
🇬🇧 🌊 Undersea cables carry most of the UK's internet and huge daily financial flows but are vulnerable. A parliamentary report says the government has been too timid and must do more to protect them. Ships have already damaged cables, attribution is difficult, and the report urges owning repair ships and tougher defenses.
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Enjoying our newsletter? Forward it to a colleague—
it’s one of the best ways to support us.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.





