We now have {{active_subscriber_count}} active subscribers! Thank you all for being part of my newsletter. Please share it with your friends and colleagues, and let’s keep growing the community.
Let’s now dive into this week’s top insights! 🚀
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
🇺🇸 Checkout.com disclosed a data breach after hackers tried to extort the company. The attackers accessed an old third-party cloud storage system that was not used since 2020 and did not affect payment processing or card data. Checkout refused to pay and instead will donate the ransom amount to cybersecurity research at Carnegie Mellon and Oxford.
🇨🇦 DoorDash says an October cybersecurity incident exposed some users' contact information after an employee was tricked by a social engineering scam. The company has closed the unauthorized access, launched an investigation, and notified affected users (mostly in Canada so far). Customers are warned to watch for phishing and DoorDash says it has strengthened security and informed law enforcement.
🇬🇧 Pathology provider Synnovis confirmed patient personal data was stolen in a June 3, 2024 ransomware attack that disrupted London hospital services. The Qilin gang published about 400 GB of data that included names, birth dates, NHS numbers and some test results. Synnovis rebuilt systems, got an injunction to limit publication, notified partner organizations, and says it will not notify patients directly.
👐 Security firm Wiz found that 65% of Forbes AI 50 companies with GitHub accounts leaked sensitive secrets like API keys and tokens. Some leaks could expose private models, training data, and org details, and many vendors did not respond to notifications.
→ More breaches:
🔗 Partners and Affiliates
With its user-friendly interface, robust security features, and commitment to privacy, NordVPN continues to be a popular choice for individuals seeking online protection and unrestricted internet access.
Special Offer: get up to 73% off with a 2-year plan!
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
🤑 The Akira ransomware group has earned over $244 million by attacking businesses and critical infrastructure since at least March 2023. They target VMware ESXi and other platforms, exploit multiple known vulnerabilities and stolen credentials, and use tools to move laterally and evade detection. In many cases they quickly steal data, disable protections, and encrypt files with extensions like .akira or .powerranges.
🇪🇺 ❌ Europol-led Operation Endgame disrupted Rhadamanthys stealer, Venom RAT, and the Elysium botnet in a global takedown. Authorities arrested a suspect in Greece, seized domains, and removed over 1,025 servers tied to millions of stolen credentials and many compromised machines. Investigations involved multiple countries and found the malware targeted crypto wallets and added stealthy fingerprinting features.
⚖ 🇨🇳 Google sued a China-linked group called Smishing Triad over the Lighthouse phishing kit. The kit sent fake SMS links to trick users into giving up passwords, bank details, and more, targeting over a million people worldwide. Google seeks court orders to seize domains and help unmask the criminals while backing laws to fight scams.
🇺🇸 📰 The Washington Post says hackers stole human resources data for 9,720 people from its Oracle E-Business Suite. The Clop ransomware group exploited a zero-day flaw to access Oracle systems and demand payment. Oracle released a patch and many other organizations were also affected.
🇦🇺 🇰🇵 Australia sanctioned four entities and one person tied to North Korean cybercrime supporting its weapons programs. The measures include financial blocks and travel bans and follow similar U.S. actions. Officials say the sanctions target cryptocurrency theft, fraud schemes, and money laundering that fund Pyongyang’s programs.
🇷🇺 🇺🇸 Aleksei Volkov, a 25-year-old Russian, pleaded guilty to helping run Yanluowang ransomware attacks that hit seven U.S. businesses. He admitted selling access, exploiting systems, and sharing ransom proceeds; victims lost data and some had to shut down. Volkov faces up to 53 years in prison and must pay about $9.2 million in restitution.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests (and don’t forget to star the project); Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇺🇸 🇰🇵 The U.S. Department Of Justice (DOJ) has won multiple cases against people who helped North Korean operatives get hired at U.S. companies by using stolen identities and hosting laptop farms. Several defendants pleaded guilty and agreed to forfeitures after schemes that funneled millions in salaries and compromised U.S. residents’ identities. The department also seized over $15 million in cryptocurrency tied to North Korean hacking groups.
🇺🇸 🪖 The Department of War (the DOD pretty much) is launching CYBERCOM 2.0 to remake how the U.S. builds and keeps cyber forces — It creates targeted recruiting, mission-specific training, new career paths, and support units to keep cyber teams ready and effective. New centers will speed capability development and manage cyber talent to counter major adversaries like China.
🇺🇲 🌏 The U.S. is creating a Scam Center Strike Force to investigate and shut down Southeast Asian cyber scam compounds that stole billions from Americans. The team will use sanctions, seizures, and prosecutions and target groups in Burma, Cambodia, and Laos. The Treasury also sanctioned Myanmar’s DKBA and related companies for helping run and profit from these scam centers and human trafficking.
🇬🇧 The UK has introduced the Cyber Security and Resilience Bill to strengthen defenses for hospitals, energy, water, and transport against costly cyberattacks. The law forces medium and large IT and cybersecurity providers to meet mandatory security standards, report major incidents quickly, and face turnover-based penalties for breaches. Regulators can designate critical suppliers and the government can order actions to protect national security, aiming to reduce annual cyber losses of about £15 billion.
🇦🇺 🇨🇳 Australia’s spy chief says China-backed hackers are probing and sometimes accessing the country’s critical infrastructure. He warned groups like Volt Typhoon and Salt Typhoon are pre-positioning for espionage and possible sabotage. Officials fear these intrusions could disrupt power, water, telecoms and other vital services.
🇺🇸 🇨🇳 The U.S. government may ban sales of TP-Link routers over concerns about Chinese influence and security risks. Many cheap consumer routers from TP-Link and other vendors ship insecure by default and are often vulnerable unless updated or replaced. Users can improve safety by updating firmware, using open-source firmware like OpenWrt, or replacing old routers, but check with your ISP before changing leased or managed devices.
🔗 Partners and Affiliates

🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
🦠 MALWARE & THREATS
💬 🇧🇷 Security researchers found a new WhatsApp-spreading malware called Maverick that hijacks WhatsApp Web and browser sessions to target Brazilian banks. It shares code and tactics with the Coyote banking trojan and uses PowerShell/VBScript, Chrome profiles, and automation to steal credentials and propagate. The campaign is focused on Brazil and features remote control, email-based C2, and tools to evade detection.
🎣 🇰🇷 North Korean-linked hackers used spear-phishing to steal Google account credentials and abused Android’s Find My Device to track and remotely wipe victims’ phones. They targeted South Koreans via KakaoTalk, then hijacked PC sessions to spread malware to contacts.
🧩 🇷🇺 Researchers found three VS Code extensions carrying GlassWorm malware that steal code and crypto credentials. The malware hides code using invisible Unicode and uses stolen tokens and Solana blockchain posts to update itself and spread. Victims include organizations worldwide, and attackers appear to be Russian-speaking.
🎣 A large phishing campaign targets hotels by sending fake Booking.com messages that redirect staff to ClickFix pages to steal credentials. The attack delivers PureRAT via a malicious PowerShell command, giving attackers full remote access and data-stealing abilities. Stolen accounts and logs are sold on crime forums or used to defraud customers.
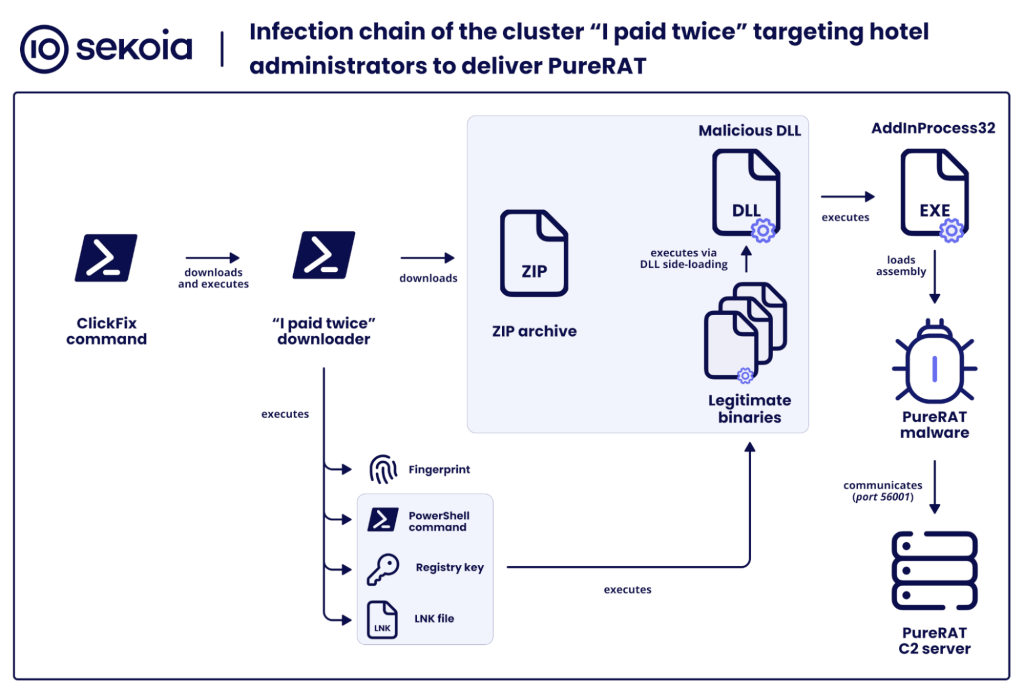
Figure: Infection chain/sekoia
🤖 🧰 AI, CRYPTO, TECH & TOOLS
🇨🇳 👀 Anthropic has detected a large-scale espionage campaign where AI agents ran most of the attack with little human help. A Chinese state-linked group used a jailbroken Claude Code to scan targets, write exploit code, steal credentials, and exfiltrate data. This shows AI agents can greatly lower the bar for powerful cyberattacks and demands better defenses, detection, and safeguards.

Figure: The lifecycle of the attack/anthropic.com
🇮🇪 🇪🇺 The Irish Council for Civil Liberties (ICCL) has complained to the European Ombudsman after the European Commission used ChatGPT-generated content in a public document. This likely breaks the Commission’s own AI rules and may violate its duty to provide accurate information. ICCL says public bodies must disclose AI use and prove any AI-generated claims.
🛂 ✈ Apple Wallet now lets U.S. iPhone and Apple Watch users add their passport as a Digital ID for use at TSA checkpoints in over 250 airports. Setup requires scanning the passport chip and a selfie for verification, and authentication uses Face ID or Touch ID. The feature is in beta, not valid for international travel, and Apple says it protects users’ privacy.
🔓 Microsoft researchers discovered "Whisper Leak", a side-channel attack that infers LLM conversation topics by observing encrypted traffic packet sizes and timing. The attack can reveal sensitive subjects like legal or medical advice even without decrypting messages. Mitigations include random padding, token batching, non-streaming models, VPNs, and provider-side fixes.
🇨🇳 🇬🇧 A Chinese woman called the "Bitcoin Queen" was jailed in London for 11 years and eight months for laundering proceeds from a £5.5 billion ($7.3B) crypto fraud. She led a scheme that defrauded over 128,000 investors and was linked to the seizure of 61,000 Bitcoin — the largest crypto confiscation in UK history. Two associates also received prison terms after assets and wallets were seized.
🐛 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
🗓 🩹 Chipmaker Patch Tuesday — Intel, AMD, and Nvidia released security advisories fixing many recent vulnerabilities in their chips and software. Intel patched over 60 flaws across processors, graphics, firmware, and drivers that could allow DoS, privilege escalation, or data leaks. AMD and Nvidia fixed several high-severity issues in SoCs, AI frameworks, and tools that could enable code execution, data disclosure, or tampering.
🩹 CISA ordered U.S. federal agencies to patch a critical Samsung zero-day (CVE-2025-21042) exploited to install LandFall spyware via malicious WhatsApp images. The spyware can steal calls, messages, photos, location, browsing history, and more from many Samsung flagship models. Agencies must patch by December 1, and CISA urges all organizations to update devices immediately.

Figure: CVE-2025-21042 exploitation timeline/ Palo Alto Unit 42
💥 Researchers warn of an authentication bypass in Fortinet FortiWeb that lets attackers add admin accounts and take over devices. The flaw was silently patched in version 8.0.2 after active in-the-wild exploitation was observed. Organizations using older FortiWeb versions should check for compromise and apply the patch immediately.
🍯 Amazon found an advanced persistent threat (APT) group exploiting zero-day bugs in Cisco ISE and Citrix NetScaler before vendors patched them. Their honeypot and investigation showed custom backdoors and rapid weaponization, likely for espionage. The attacks highlight rising focus on identity and network edge infrastructure.
💰 Google paid $458,000 in bug bounties at its bugSWAT live-hacking event during the ESCAL8 conference. 38 top hackers submitted 107 reports focused on AI, Android, and Google Cloud, and Google launched a new AI Vulnerability Reward Program offering up to $20,000 per finding. The conference also featured a CTF, workshops for over 60 students, and nearly 200 attendees.
🤑 🤖 Amazon launched an invite-only bug bounty program for its NOVA AI models — Selected researchers will test for prompt injection, jailbreaking, and other exploitable flaws, including misuse for dangerous weapon-related assistance. The program aims to improve security as NOVA is used across Amazon products and services.
🔓 Researchers found vulnerabilities in the runc container runtime that can let malicious containers escape and get root on the host. Patches and advisories from vendors like Red Hat and AWS have been released. The flaws are rated medium but could be more serious for Docker or Kubernetes if untrusted images are run.
🗒 OWASP released a near-final 2025 Top 10 list for web application risks with two new categories and a reordered ranking. Broken Access Control stays first and now includes SSRF; a new Mishandling of Exceptional Conditions appears at ten. OWASP changed its data-driven method, using many more CWEs and CVE/CVSS data plus a community survey.
🛰️ ICS, OT & IoT
🗓 🩹 ICS Patch Tuesday — Industrial control vendors Siemens, Rockwell, Aveva, and Schneider released Patch Tuesday advisories fixing multiple security flaws in ICS/OT products. The bugs include critical code execution, authentication bypasses, XSS, path traversal, and other high-severity issues that could allow tampering or credential theft. Other vendors like Moxa, ABB, Honeywell, and Mitsubishi reported fixes recently, and VDE@CERT also published advisories.
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Enjoying our newsletter? Forward it to a colleague—
it’s one of the best ways to support us.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.





