[InfoSec MASHUP] 47/2024
T-Mobile Confirmed Breach; Jen Easterly Leaving CISA in Jan. '25; US Gov. and Security Related Bills; DPRK Workers Funding Missile Programs; Apple Confirms Zero-Day Attacks;
Welcome to the 23 new members from the last 30 days! This newsletter now has 1,603 subscribers.
Partners and Affiliates
🔐 NordVPN - Save up to 75% + 3 Extra Months!
Breaches & Security Incidents
🇺🇸 🔓 Finastra is investigating a data breach involving the theft of over 400 gigabytes of information from its internal file transfer platform — The company notified its customers after a cybercriminal started selling the stolen data online. Finastra assures that there is no direct impact on customer operations and is working to determine the scope of the compromised data.
🇺🇸 🔓 Ford is investigating a possible data breach after a hacker claimed to leak 44,000 customer records on a hacking forum. The leaked information includes names, addresses, and purchase details, which could be used for phishing attacks. Ford is actively looking into the claims and has acknowledged the potential security issue.
🇺🇸 🔓 Maxar Space Systems experienced a data breach where hackers accessed personal information of its employees. The company discovered the intrusion about a week after it occurred and took immediate action to secure its systems. Current and former employees affected by the breach are being offered identity protection services.
🇺🇸 🔓 T-Mobile confirmed it was hacked as part of a series of attacks by Chinese threat actors targeting telecom companies. The company stated that, so far, customer data has not been significantly affected. This breach is one of several T-Mobile has experienced since 2019.
➝ More breaches:
Cyberattack at French hospital exposes health data of 750,000 patients
Hackers broke into Andrew Tate's online course and stole data from nearly 800,000 users
🔊 Interested in Reaching a Cybersecurity Audience?
Amplify your brand’s presence by sponsoring the InfoSec MASHUP newsletter!
Reach dedicated readers in the cybersecurity field with each issue! Contact us to explore sponsorship opportunities.
Cybercrime, Cyber Espionage, APT’s
CISA says BianLian ransomware now focuses only on data theft
🇨🇳 A China-linked group called TAG-112 has targeted Tibetan media and university websites with a cyber espionage campaign using malicious JavaScript to deliver a harmful tool called Cobalt Strike. They tricked visitors into downloading a disguised executable by creating a fake TLS certificate error on the compromised sites. This attack highlights ongoing cyber threats against Tibetan entities, which are often linked to state-sponsored activities.
🇷🇺 Hackers linked to the Russian GRU breached a high-value target's network by first hacking a nearby Wi-Fi-enabled device — This method allowed them to exploit the target's Wi-Fi accounts without being physically close. The attack highlights how skilled hackers can find innovative ways to bypass security when initial efforts fail.
🇺🇸 💸 Meta has removed millions of accounts linked to "pig butchering" scams, which trick victims into losing money — This crackdown is part of a broader effort to combat scams that have cost U.S. victims billions. The company aims to share its strategies to help protect people from these criminal activities.
🇪🇬 Microsoft has seized 240 websites linked to an Egyptian seller of DIY phishing kits that target its user accounts. The kit-maker, known as MRxC0DER, created tools that can bypass multifactor authentication, posing a significant threat, especially to the financial services industry. While this action won't eliminate the threat, it aims to disrupt the operations of cybercriminals.
🇺🇸 The U.S. has shut down the cybercrime website PopeyeTools and charged its three administrators for selling stolen data. Authorities seized multiple domains and $283,000 in cryptocurrency linked to the site. PopeyeTools was a marketplace for cybercriminals, offering stolen personal information and tools for fraud.
🇨🇳 👀 Researchers from ESET have discovered two new Linux backdoors named WolfsBane and FireWood, which are used for cyberespionage — WolfsBane is linked to a Chinese hacking group called Gelsemium, while FireWood's connection to the group is uncertain.
☎️ 👀 CAPE has launched a privacy-focused mobile phone designed for high-risk individuals, aiming to protect user data without keeping metadata. The phone complies with U.S. surveillance laws and targets politicians, journalists, and activists who face privacy risks. CAPE's CEO emphasizes their commitment to security while distinguishing their product from those aimed at the criminal market.
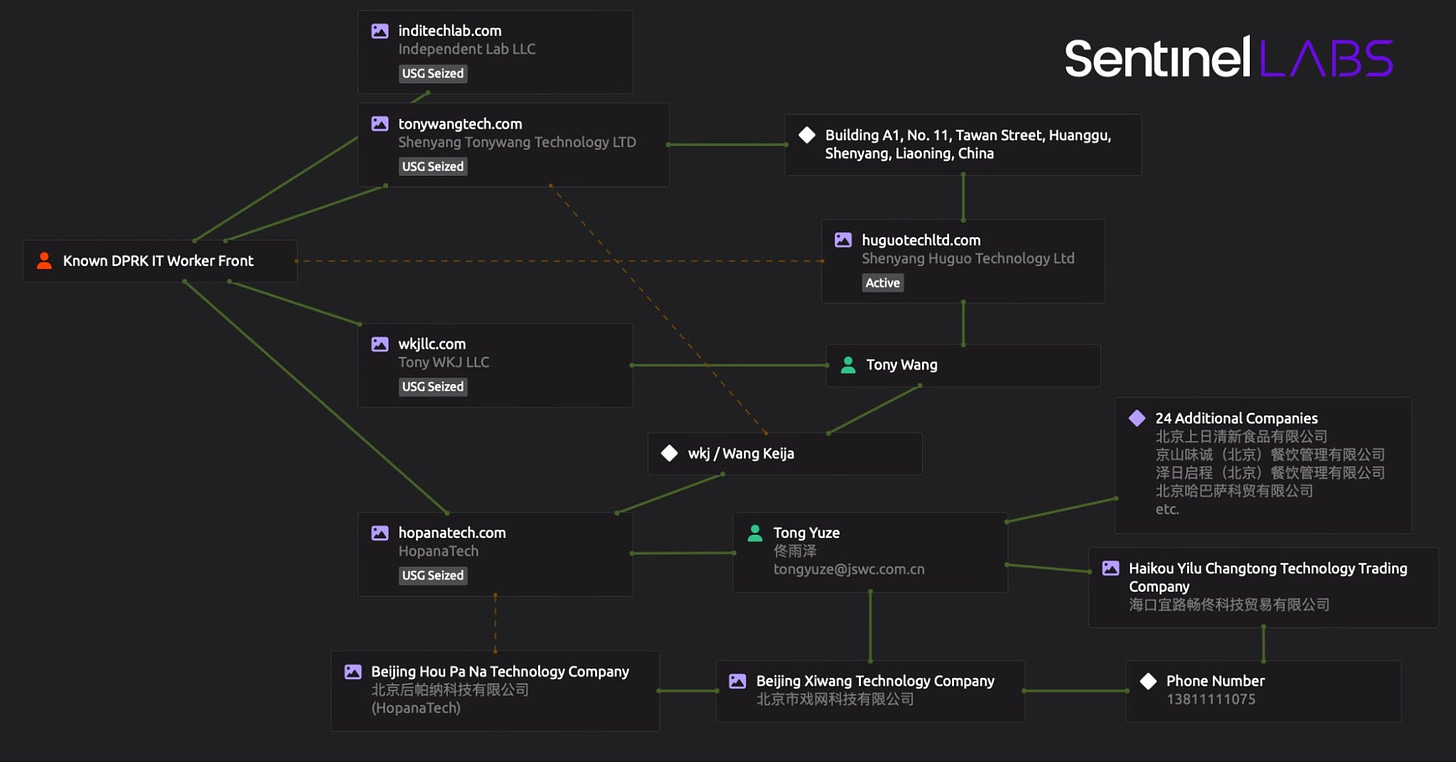
🇰🇵 North Korean operatives are using fake U.S. IT companies to hide their identities and fund missile programs — They work through front companies in places like China and Russia, sending money back to North Korea. The U.S. government has seized multiple fraudulent websites linked to this scheme.
🇨🇳 A new China-linked hacking group called Liminal Panda has been targeting telecom networks in South Asia and Africa since 2020 to collect intelligence. They use advanced malware and exploit mobile communication protocols to access sensitive data and infiltrate other telecom providers.
🇺🇸 ⚖️ Evgenii Ptitsyn, a Russian man linked to the Phobos ransomware operation, has been extradited from South Korea to face charges in the U.S. — Phobos has been involved in hacking over 1,000 organizations and extorting more than $16 million in ransom payments. Ptitsyn faces serious charges, including wire fraud and extortion, and could receive lengthy prison sentences if convicted.
Government, Politics, and Privacy
🇺🇦 The Computer Emergency Response Team of Ukraine has launched TRYZUB, a cyber training service to help military and government sectors defend against cyber threats — TRYZUB uses real-world attack scenarios to train teams in protecting critical infrastructure.
🇺🇸 ⚖️ The U.S. government has charged five individuals linked to a hacking group called 0ktapus for stealing data and cryptocurrency from tech companies and employees. They used phishing attacks and SIM swapping to access sensitive information, allegedly stealing millions of dollars. The hackers targeted at least 45 companies, and more suspects may still be involved in their activities.
🇺🇸 A bill requiring federal contractors to have vulnerability disclosure policies has passed a key Senate panel and is set for a full vote. This legislation aims to improve cybersecurity by ensuring contractors can effectively manage reports of software vulnerabilities. It is part of a broader effort to strengthen the nation's cybersecurity defenses and protect sensitive data.
🇺🇸 A new bipartisan Senate bill aims to enhance the security of the U.S. IT supply chain by giving the Federal Acquisition Security Council more oversight powers. The legislation focuses on combating threats from foreign adversaries, especially China, by allowing Congress to investigate and potentially ban risky technology products. Senators Peters and Rounds emphasize that protecting the federal supply chain is crucial for national security.
🇺🇸 Jen Easterly, the director of the U.S. Cybersecurity and Infrastructure Security Agency (CISA), will leave her position on January 20 — She has led CISA for over three years, focusing on improving cybersecurity and defending against foreign attacks. Both she and deputy director Nitin Natarajan are departing as the new Trump administration takes over.
Partners and Affiliates
🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
Malware & Threats
Helldown ransomware exploits Zyxel VPN flaw to breach networks
🦠 🇷🇺 Russian hackers, linked to a cyber espionage campaign, are using malware named HATVIBE and CHERRYSPY to target organizations in Europe and Asia — They primarily attack government and educational institutions to gather intelligence, especially in Central Asia. This activity is part of a broader Russian strategy to influence geopolitical developments and destabilize NATO allies.
🦠 💳 NodeStealer malware is now targeting Facebook Ads Manager accounts to steal credit card data and account details. It uses advanced techniques to access browser files and avoid detection in Vietnam. This malware aims to hijack accounts for malicious advertising campaigns, posing financial risks to users and businesses.
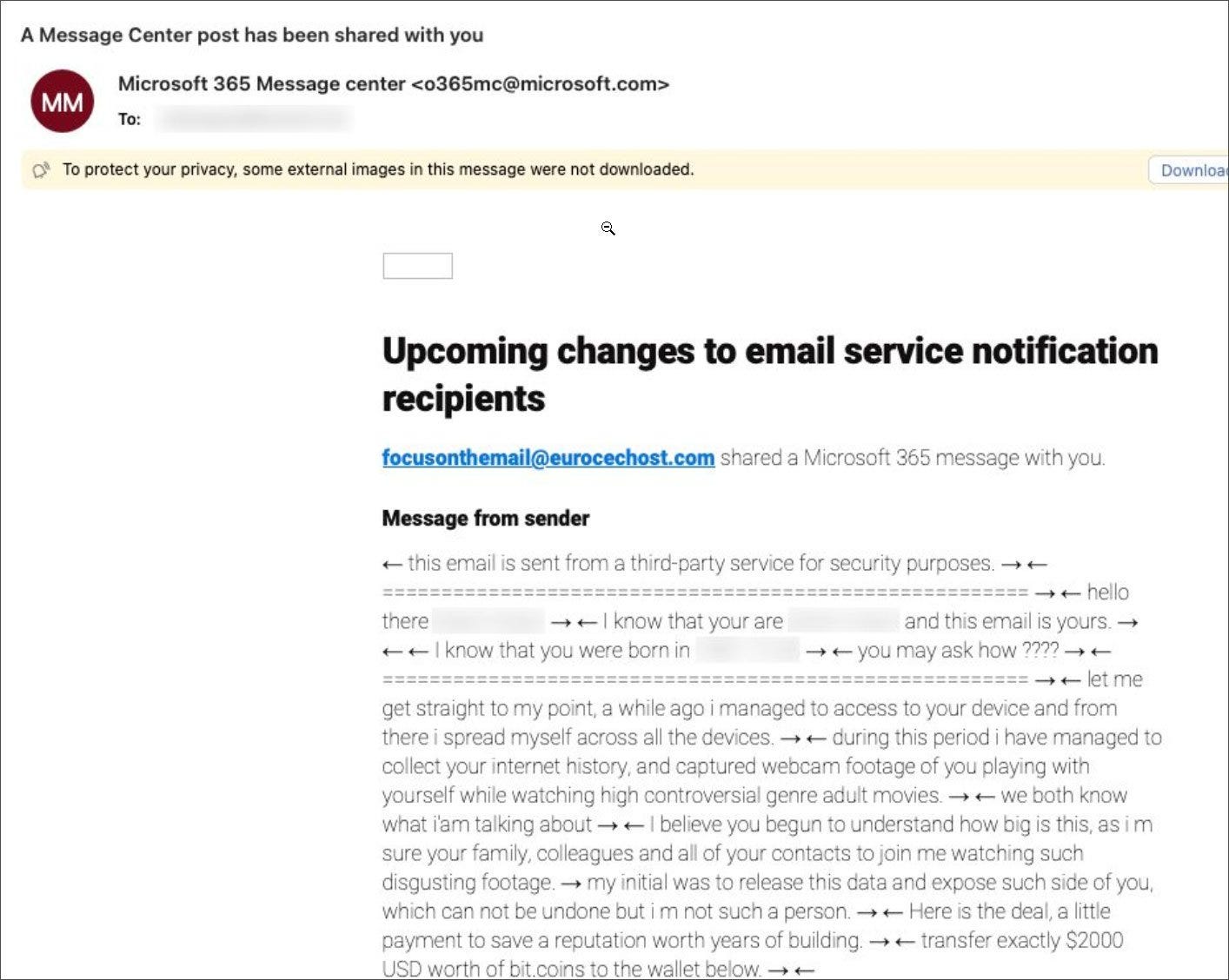
📨 Scammers are using the Microsoft 365 Admin Portal to send sextortion emails that appear legitimate. These emails falsely claim to have compromising information and demand payment to prevent sharing it. Microsoft is investigating this issue, but it's important to recognize these emails as scams and avoid engaging with them.
🦠 💸 A new variant of the Helldown ransomware is now targeting VMware and Linux systems, expanding its attack focus beyond Windows. This ransomware group, known for exploiting security vulnerabilities, has attacked at least 31 companies recently and uses tactics like double extortion to pressure victims. Researchers note that the Linux version of Helldown is less sophisticated and may still be in development, as it lacks certain security features.
🦠 A new stealthy malware called BabbleLoader has been discovered, which delivers information stealers like WhiteSnake and Meduza — It uses advanced techniques to avoid detection by antivirus software, making it very difficult to analyze. BabbleLoader is part of a growing trend of loaders that help spread malware while evading security measures.
🦠 🤖 Fake AI video and image generators are spreading malware that steals sensitive information from Windows and macOS users — The malware, called Lumma Stealer for Windows and AMOS for macOS, collects data like passwords and cryptocurrency wallets and sends it to attackers. Users who have downloaded these fake applications should reset their passwords and enable multi-factor authentication to protect their accounts.
AI, Crypto, Tech & Tools
📨 👀 Google is introducing a new feature called Shielded Email that lets users create unique email aliases for signing up for services, which helps protect their privacy and reduce spam. This feature allows messages to be forwarded to the user's main email without revealing their real address. Similar privacy options have been offered by Apple and other companies in recent years.
Vulnerabilities, Research, and Threat Intelligence
Apple fixes two zero-days used in attacks on Intel-based Macs
Oracle patches exploited Agile PLM vulnerability (CVE-2024-21287)
🔓 💥 Attackers have compromised about 2,000 Palo Alto Networks firewalls using two recently discovered vulnerabilities. Most affected devices are found in the US and India. Palo Alto Networks has warned that these flaws could lead to increased attacks and has provided guidance for affected organizations.
📊 🪳 MITRE has released its 2024 list of the top 25 most dangerous software weaknesses, based on over 31,000 vulnerabilities identified from June 2023 to June 2024. These weaknesses can be easily exploited by attackers to take control of systems, steal data, or disrupt services. Organizations are encouraged to review this list to improve their software security strategies and prevent vulnerabilities.
🧪 🤖 Microsoft is launching the Zero Day Quest hacking event with $4 million in rewards to encourage researchers to find vulnerabilities in its AI and cloud services. The event includes an open Research Challenge for all and an invite-only onsite hacking event for top researchers. Participants will have opportunities to work directly with Microsoft engineers and enhance AI security.
🇨🇳 💥 Chinese hackers are using a tool called 'DeepData' to exploit a security flaw in Fortinet's VPN software to steal user credentials. This vulnerability was discovered by researchers earlier this summer, but it remains unaddressed by Fortinet. The hackers can access sensitive corporate networks by compromising VPN accounts, increasing the risk of surveillance and data theft.
🪳 💥 Attackers are exploiting two critical vulnerabilities in VMware vCenter Server, including one that allows remote code execution. Broadcom has released security updates but warns that the initial patch did not fully fix the issues. Users are urged to apply the latest updates immediately to protect against these active threats.
🧩 🔓 A serious security flaw in the WordPress plugin 'Really Simple Security' allows attackers to gain admin access to millions of sites. The vulnerability, discovered by Wordfence, affects both free and Pro versions of the plugin and can be exploited easily. Users are urged to update to version 9.1.2 to protect their sites from this critical issue.
ICS, OT & IoT
🔓 Research has revealed over 145,000 Industrial Control Systems (ICS) exposed online across 175 countries, with the U.S. having the highest number. Many of these systems use outdated security protocols, making them vulnerable to cyber attacks. Organizations must take action to secure these devices and monitor for potential threats.