[InfoSec MASHUP] 48/2024
Hacker in Snowflake Extortions May Be a U.S. Soldier; Zoom Pays More For False Encryption Claims; Chinese Spy in US Sentenced; The First UEFI Bootkit Targeting Linux Systems;
Welcome to the 14 new members from the last 30 days! This newsletter now has 1,604 subscribers.
Partners and Affiliates
🔐 NordVPN - Save up to 75% + 3 Extra Months!
Breaches & Security Incidents
🇺🇸 🔓 T-Mobile stated that hackers did not gain access to customer calls, texts, or voicemails during a recent cyberattack — The company detected attempts to infiltrate its systems and quickly cut off connectivity to a potentially compromised telecom provider. T-Mobile emphasized that its cybersecurity measures successfully protected sensitive customer information from being accessed.
🇬🇧 🏥 The Wirral University Teaching Hospital in the UK faced a cyberattack that caused system outages, leading to postponed appointments and procedures — The hospital is currently operating manually, which has resulted in longer waiting times and limited services. Authorities are working to restore systems, but there is no timeline for when normal operations will resume.
🇺🇸 🔓 Blue Yonder, a supply chain management company, suffered a ransomware attack that disrupted its services for many customers, including Starbucks and major grocery chains. Starbucks is now using manual processes to ensure employee payments due to the attack. Blue Yonder is working with cybersecurity firms to recover and monitor their systems.
🔊 Interested in Reaching a Cybersecurity Audience?
Amplify your brand’s presence by sponsoring the InfoSec MASHUP newsletter!
Reach dedicated readers in the cybersecurity field with each issue! Contact us to explore sponsorship opportunities.
Cybercrime, Cyber Espionage, APT’s
🇨🇳 🇺🇸 A 59-year-old U.S. citizen, Ping Li, was sentenced to four years in prison for spying for China's intelligence agency — He shared sensitive information from his jobs at Verizon and Infosys, including details about Chinese dissidents and cybersecurity training. Li was fined $250,000 and will face three years of supervised release after his prison term.
🇮🇹 Italian police have shut down a major pirate streaming service that had over 22 million users and made €250 million a month — The operation, called "Taken Down," involved law enforcement from multiple countries and resulted in numerous arrests and the seizure of illegal channels and servers. The criminals behind the service face charges for streaming copyrighted content and money laundering.
🇹🇭 Thai police arrested a man for sending nearly one million scam text messages from a van in Bangkok — The messages tricked people into clicking a link that stole their credit card information. Authorities are searching for more members of the fraud ring, which used a device to send 100,000 messages an hour.
🇰🇷 APT-C-60, a cyber espionage group aligned with South Korea, targeted a Japanese organization using a phishing email that delivered the SpyGlace backdoor. The attack exploited a vulnerability in WPS Office and utilized legitimate services like Google Drive and Bitbucket to distribute malware. This method involved using a virtual hard disk file to distract the victim while executing malicious code.
🇺🇸 Two men have been arrested for stealing data from companies using Snowflake, while a third hacker, Kiberphant0m, remains at large and is believed to be a U.S. Army soldier stationed in South Korea. Kiberphant0m has been publicly extorting victims and selling stolen data, including sensitive information from major corporations like AT&T. Despite denying involvement with the Army, evidence suggests that Kiberphant0m's multiple online identities link back to military connections.
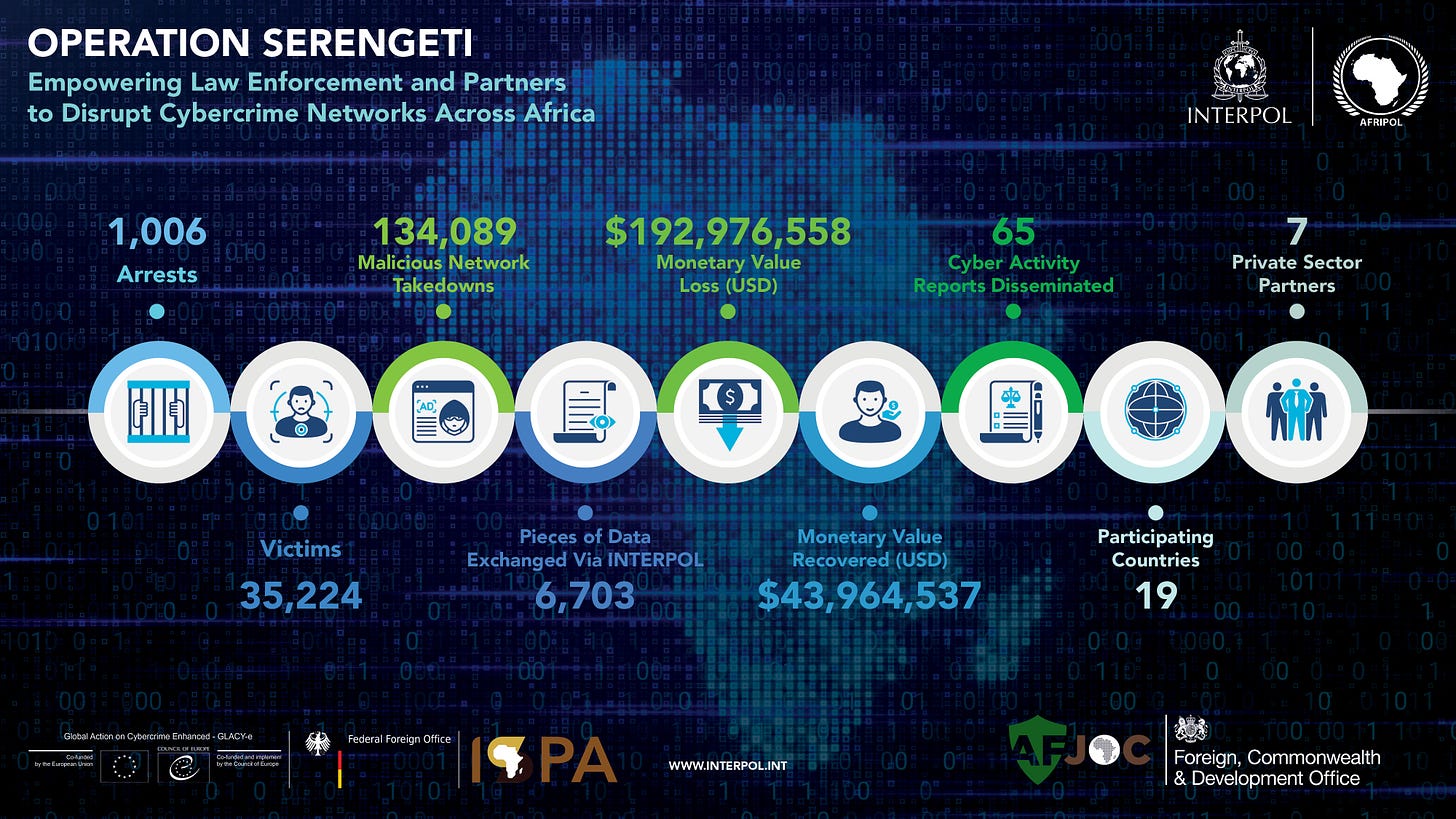
🌍 ⚖️ An international law enforcement operation called Operation Serengeti has arrested over 1,000 cybercrime suspects in 19 African countries — The operation revealed connections to 35,000 victims and $193 million in losses from various cybercrimes. Authorities aim to combat emerging threats and continue their efforts against cybercriminals worldwide.
🇨🇳 🦠 A report from Trend Micro reveals that the cyber-espionage group Salt Typhoon has conducted sophisticated hacks on telecommunications companies worldwide — They use advanced malware and exploit known vulnerabilities to gain access and remain undetected in networks. U.S. officials are alarmed, calling it one of the worst telecom hacks in history, with ongoing concerns about the group's activities.
🇺🇸 ⚖️ A Kansas City man, Nicholas Michael Kloster, has been indicted for hacking into a health club and a nonprofit organization to promote his cybersecurity services. He allegedly accessed their systems, stole information, and caused financial damage. If convicted, Kloster could face up to 15 years in prison and fines.
Government, Politics, and Privacy
🇺🇸 ⚖️ The U.S. Fifth Circuit Court of Appeals ruled that the Treasury Department overstepped its authority by sanctioning the cryptocurrency mixer Tornado Cash in 2022. The court found that Tornado Cash's smart contracts are not considered "property" under the law, so they should not be subject to sanctions. This decision supports the argument that open-source technology should not be penalized for the actions of some users.
Partners and Affiliates
🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
Malware & Threats
🦠 👾 Hackers have exploited the Godot game engine to spread GodLoader malware, infecting over 17,000 computers in just three months. This malware uses the engine's features to hide harmful scripts in game files, targeting users on various platforms. Attackers have been operating through a network of fake GitHub accounts to distribute this malware, taking advantage of the trust in open-source software.
🦠 🐍 The Python package "aiocpa" was quarantined on PyPI after it was found to contain malicious code that exfiltrates private crypto keys via a Telegram bot. This package, which has been downloaded over 12,000 times, was updated with harmful code while the GitHub repository remained clean to avoid detection. The incident highlights the need to carefully check package source codes before downloading, as past safety does not guarantee future security.
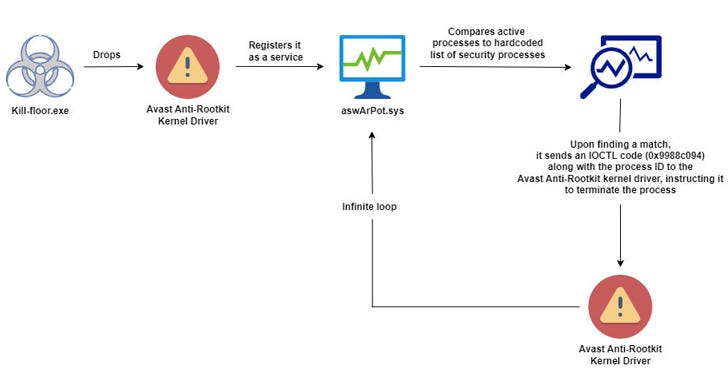
🦠 Researchers have discovered a new malware campaign that uses a method called Bring Your Own Vulnerable Driver (BYOVD) to bypass antivirus protections. The malware installs a modified Avast Anti-Rootkit driver, allowing it to disable security software and control the infected system. This tactic has become more common among cybercriminals to deploy ransomware by exploiting legitimate but vulnerable drivers.
AI, Crypto, Tech & Tools
🇺🇸 💰 Zoom has offered to pay an $18 million fine to settle an investigation into false claims about its video encryption — The company previously agreed to pay $85 million in 2021 after admitting it misled users about end-to-end encryption. The SEC is currently considering Zoom's offer to resolve the matter.
Vulnerabilities, Research, and Threat Intelligence
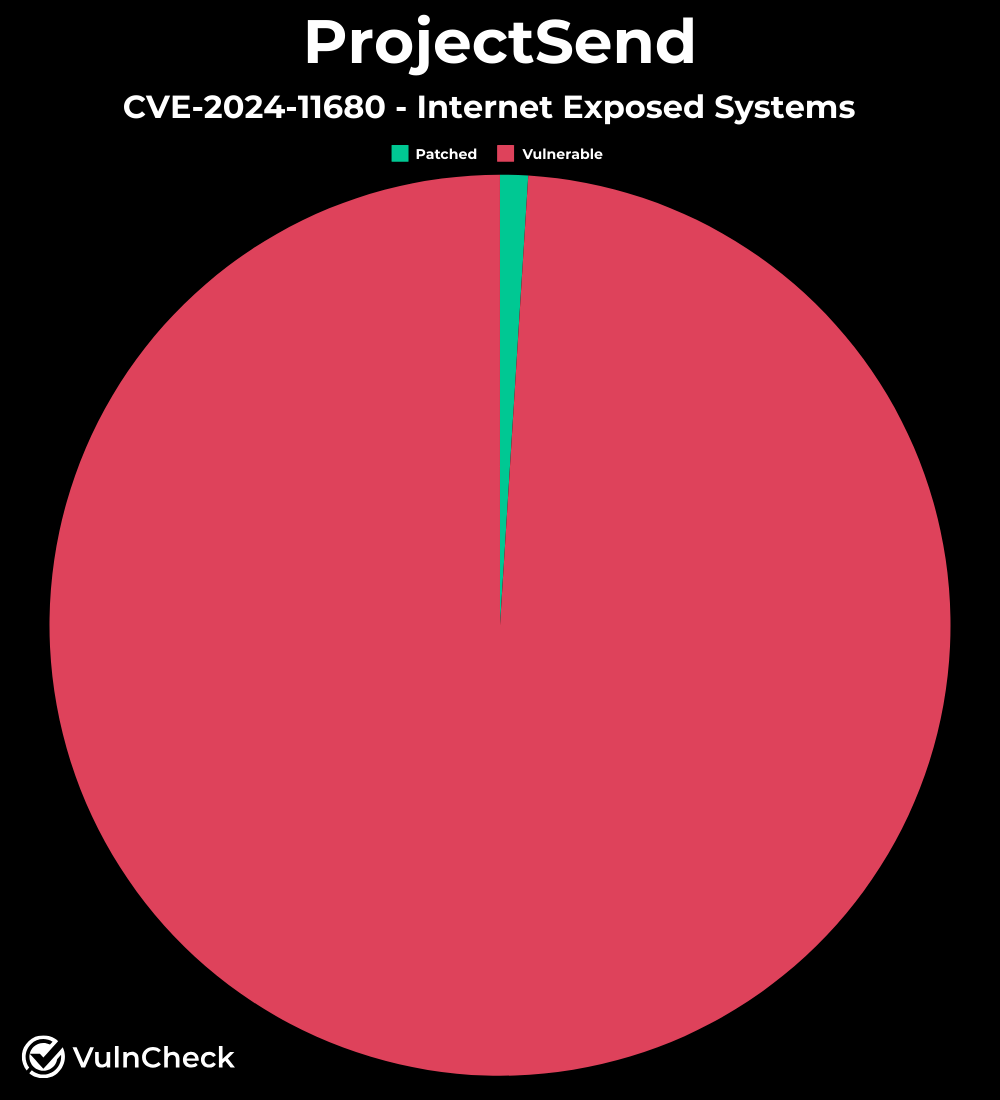
🪳 💥 A critical security flaw in the ProjectSend file-sharing application is actively being exploited, allowing attackers to execute malicious code. The vulnerability, affecting many servers that haven't been updated, was first reported in January 2023 but only patched in August 2024. Users are urged to update to the latest version to protect against these attacks.
🐧 Researchers have discovered "Bootkitty," the first UEFI bootkit targeting Linux systems, created by a group called BlackCat. This bootkit is a proof-of-concept and has not been used in real-world attacks yet. Its development highlights a new threat in cybersecurity, as UEFI bootkits are no longer limited to Windows.
🔓 Researchers discovered vulnerabilities in Palo Alto and SonicWall VPN clients, allowing attackers to use fake VPN servers to install harmful updates. These vulnerabilities can lead to stolen login credentials and the installation of malicious software. SonicWall and Palo Alto have released patches, and AmberWolf has created a tool to demonstrate how these attacks work.
🇷🇺 The Russia-aligned hacker group RomCom used two zero-day vulnerabilities in Firefox and Windows to launch attacks without user interaction. They created a fake website that led victims to a server where a backdoor was downloaded and executed. ESET discovered these vulnerabilities and reported them, prompting quick fixes from Mozilla and Microsoft.
ICS, OT & IoT
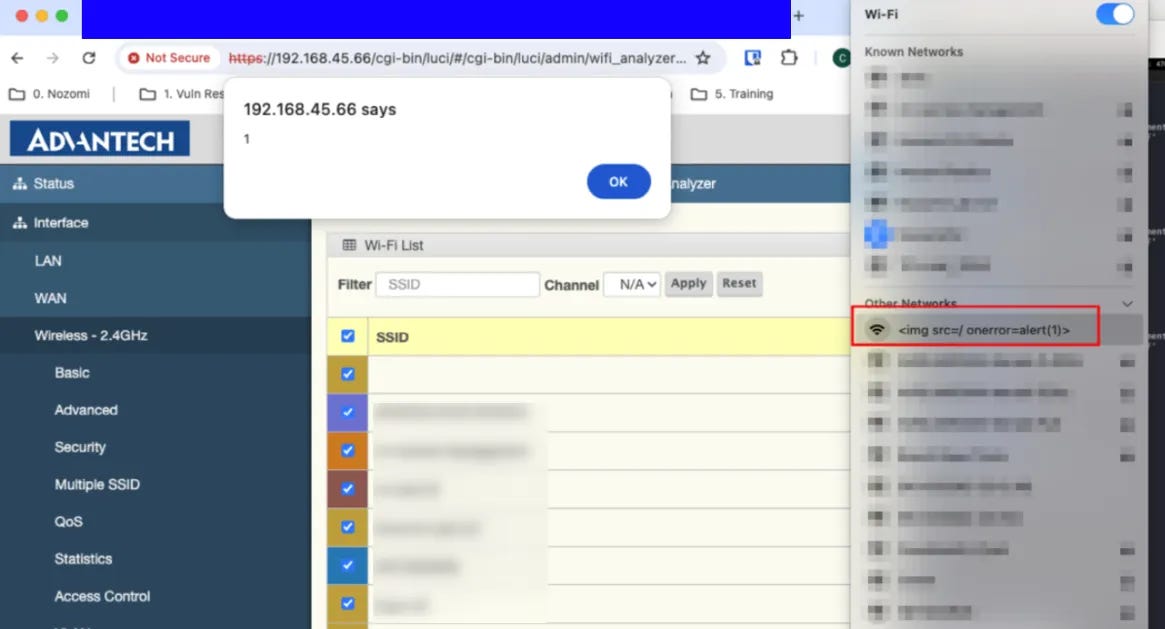
🛜 🔓 Advantech industrial Wi-Fi access points have over 20 security flaws, some critical enough to allow hackers to bypass authentication and execute code with high privileges. Six of these vulnerabilities could enable attackers to gain persistent access and control over the devices. Users are advised to update their firmware to the latest versions to protect against these risks.