[InfoSec MASHUP] 50/2024
27 DDoS-for-hire Platforms Shut Down; Security Flaw in Skoda Cars; European Union Implemented Cyber Resilience Act (CRA); A Spyware Tool Linked to Chinese Police; Voice Phishing Ring Busted;
Welcome to the 10 new members from the last 30 days! This newsletter now has 1,603 subscribers.
Partners and Affiliates
🔐 NordVPN - Save up to 75% + 3 Extra Months!
Breaches & Security Incidents
🇰🇵 💸 Radiant Capital has linked a $50 million cryptocurrency heist to North Korean hackers, specifically a group called Citrine Sleet. The cyberattack, which occurred on October 16, involved sophisticated malware that compromised developers' devices and bypassed security measures. Radiant is now working with U.S. law enforcement to recover the stolen funds.
🇺🇸 Krispy Kreme experienced a cyberattack on November 29, 2024, which disrupted its online ordering system in the U.S. While stores remain open for in-person orders, the company anticipates a financial impact due to lost digital sales and recovery costs. The investigation is ongoing, and it is still unclear if the attack involved ransomware.
🇷🇴 Romanian energy supplier Electrica is investigating an ongoing ransomware attack, but its critical systems remain unaffected. The company is working with cybersecurity authorities to ensure the safety of its operations and customer data. This incident follows a wave of cyberattacks linked to political events in Romania.
Lynx ransomware behind Electrica energy supplier cyberattack
🇺🇸 Artivion, a medical device company, reported a cybersecurity incident that disrupted its services. The company believes hackers stole and encrypted data, potentially indicating a ransomware attack. Despite the disruptions, Artivion does not expect the incident to significantly affect its finances.
🇭🇷 Luka Rijeka, a Croatian maritime company, was hacked by the 8Base ransomware group, which claims to have stolen sensitive documents. The company detected the attack on November 30 and quickly shut down its IT system, with no ransom demand received so far. Luka Rijeka has backups of its data and believes there has been no significant damage from the attack.
➝ More breaches:
Bitcoin ATM giant Byte Federal says 58,000 users’ personal data compromised in breach
390,000+ WordPress Credentials Stolen via Malicious GitHub Repository Hosting PoC Exploits
🔊 Interested in Reaching a Cybersecurity Audience?
Amplify your brand’s presence by sponsoring the InfoSec MASHUP newsletter!
Reach dedicated readers in the cybersecurity field with each issue! Contact us to explore sponsorship opportunities.
Cybercrime, Cyber Espionage, APT’s
US offers $5 million for info on North Korean IT worker farms
🇺🇸 🇰🇵 A federal court has indicted 14 North Korean IT workers accused of stealing at least $88 million from American companies over six years. These workers used fake identities to pose as employees and extorted sensitive business information. The U.S. government is actively working to disrupt North Korea's cyber operations and has offered rewards for information about these activities.
🇪🇸 🇵🇪 Spanish police, along with Peruvian authorities, arrested 83 people involved in a voice phishing scam that defrauded 10,000 bank customers out of €3 million. The scammers used fake calls to impersonate banks and trick victims into giving away sensitive information. Police advise people to verify they are speaking with real bank agents before sharing personal details.
🇷🇺 🇺🇦 A Russian hacker group called Turla (which Microsoft refers to as Secret Blizzard) is using tools from other cybercriminals to attack Ukraine, particularly targeting military networks. They have adapted malware to bypass security and gain long-term access to sensitive systems. This tactic reflects a shift in their strategy, making it harder for organizations to defend against their attacks.
🇪🇺 Law enforcement from 15 countries shut down 27 DDoS-for-hire platforms in a coordinated effort called 'Operation PowerOFF' — Three administrators were arrested, and around 300 customers were identified for using these services, which can disrupt online businesses. This crackdown aims to combat cybercrime, especially during the busy holiday shopping season.
🇺🇸 🇨🇳 The U.S. has charged a Chinese hacker, Guan Tianfeng, for exploiting a serious security flaw in Sophos firewalls, affecting around 81,000 devices globally. Guan allegedly created malware to access and steal data from these firewalls, with many targets being U.S. critical infrastructure companies. The U.S. government has also imposed sanctions on his company, Sichuan Silence, for its role in cyber attacks.
🇳🇱 🇧🇪 Eight members of a cybercrime gang were arrested in Belgium and the Netherlands for using Airbnb properties to run fraud operations — They targeted victims across Europe with phishing scams to steal money, often posing as bank employees. The police seized luxury items and cash believed to be bought with the stolen funds during the raids.
Government, Politics, and Privacy
🇷🇺 🤐 Russia has blocked the Viber messaging app for violating its laws on information dissemination — The country's internet regulator cited concerns about terrorism, illegal drugs, and extremist content. This ban follows previous actions against other messaging services and VPN apps in Russia.
🇪🇺 👀 BeReal is facing a privacy complaint in Europe for how it asks users to consent to ad tracking — The complaint claims that the app uses manipulative tactics, pressuring users who refuse tracking by repeatedly prompting them each time they try to post. A privacy rights group is asking regulators to ensure BeReal complies with GDPR rules and to impose penalties if necessary.
🇺🇸 📡 U.S. Senator Ron Wyden has proposed the "Secure American Communications Act" to strengthen cybersecurity for telecom companies after recent hacks by Chinese state hackers. The bill would require telecoms to test their networks annually and comply with new FCC rules to protect against breaches. Wyden criticized the FCC for allowing phone companies to set their own security rules, which led to vulnerabilities exploited by foreign hackers.
🇪🇺 The European Union has implemented new cybersecurity rules for connected devices called the Cyber Resilience Act (CRA) — These rules require manufacturers to ensure their products are secure and provide software updates to fix vulnerabilities. While companies have until December 11, 2027, to comply, devices can now display a CE mark to show they meet these security standards.
Partners and Affiliates
🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
Malware & Threats
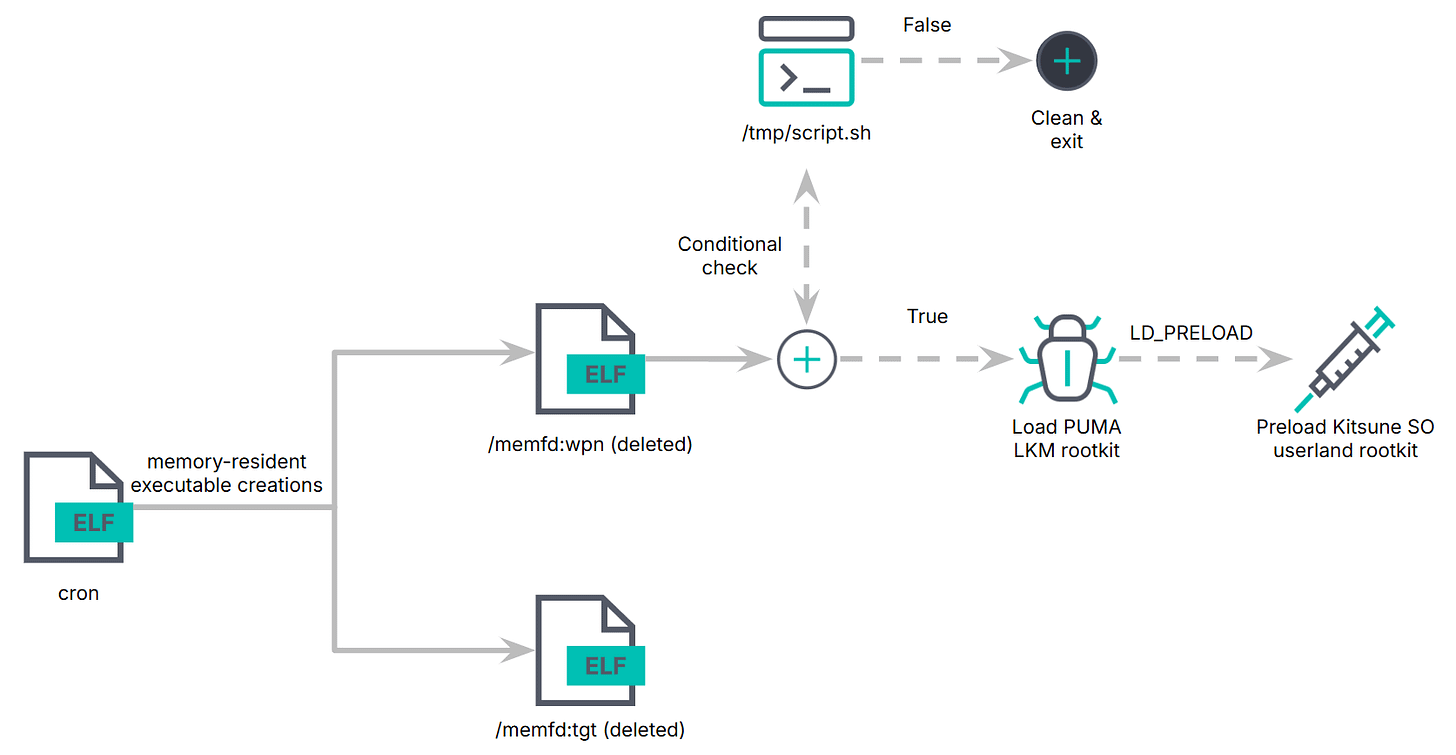
🦠 🐧 A new Linux rootkit malware called Pumakit has been found, which uses advanced techniques to remain hidden on infected systems. It consists of multiple components that allow it to escalate privileges and manipulate system behavior, targeting Linux kernels older than version 5.7. Pumakit can hide its presence and communicate with a command and control server, making it a significant threat to critical infrastructure and enterprise systems.
🦠 Researchers have found a new version of ZLoader malware that uses DNS tunneling to hide its communications. This updated version includes features that help it avoid detection and is linked to recent ransomware attacks. ZLoader's methods are becoming more sophisticated, allowing it to act as a gateway for other malware.
🦠 A new malware technique uses Windows' UI Automation framework to carry out harmful actions while avoiding detection by EDR tools. This method can allow attackers to steal sensitive data and manipulate messaging applications without being noticed. It highlights a security vulnerability in the way assistive technology applications interact with system UI elements.
🦠 🇨🇳 Researchers have discovered EagleMsgSpy, a spyware tool linked to Chinese police, that has been tracking mobile devices since 2017. It collects extensive data, including messages, screen recordings, and location information, without the user's knowledge. The spyware requires physical access to the device for installation and is believed to be used by law enforcement in China.
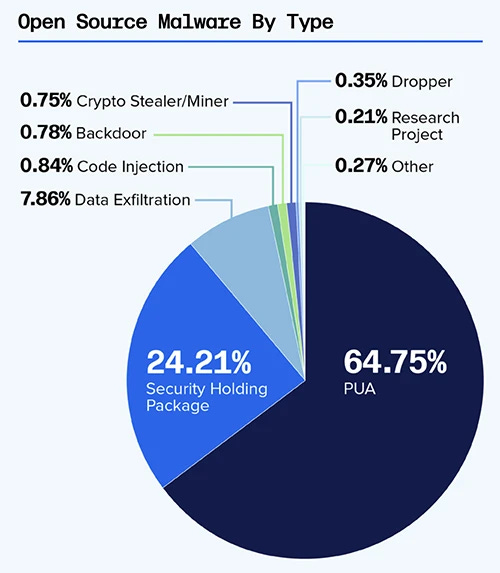
🦠 Open source malware has increased by 200% since 2023, with over 778,500 malicious packages detected — Developers are targeted through popular platforms like npm and PyPI, as attackers exploit low security measures to infiltrate software supply chains. Many of these malicious packages contain potentially unwanted applications that can compromise user privacy and security.
🦠 🕸️ A malicious botnet called Socks5Systemz is powering an illegal proxy service, PROXY.AM, which has over 85,000 hacked devices. This botnet allows cybercriminals to obscure their activities by using compromised systems as anonymous proxy servers. The service has been active since 2016 and is marketed as offering private proxy servers for a fee.
AI, Crypto, Tech & Tools
Back where it started: “Do Not Track” removed from Firefox after 13 years
🙈 MITRE Corporation released new findings evaluating 19 cybersecurity vendors' abilities to detect and protect against ransomware and North Korean malware. The results showed some vendors had more false positives than actual detections, indicating a need for improvement. The evaluation also included macOS threats for the first time, highlighting the growing importance of security for Apple devices.
Vulnerabilities, Research, and Threat Intelligence
🪳 🔓 A critical security flaw in Microsoft's multi-factor authentication (MFA) allowed attackers to bypass protections and gain unauthorized access without alerting victims. Researchers discovered that the lack of rate limits enabled unlimited brute-force attempts on six-digit codes. Microsoft has since fixed the issue by enforcing stricter rate limits to enhance security.
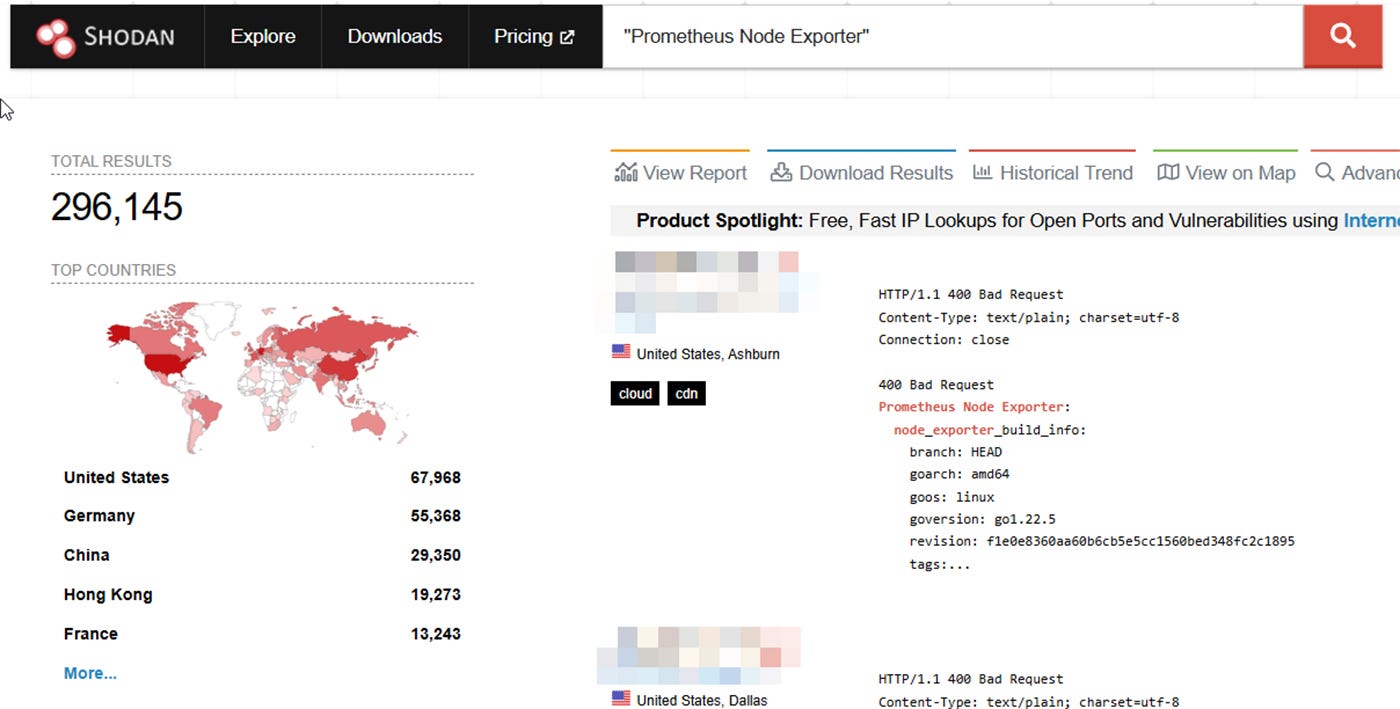
🔓 Cybersecurity researchers warn that over 300,000 Prometheus servers are exposed online, risking sensitive information leaks and potential attacks. Many of these servers lack proper authentication, allowing attackers to access credentials and cause denial-of-service issues. Organizations are advised to secure their Prometheus servers and monitor for unusual activity to prevent exploitation.
🪳 🚗 Researchers found security flaws in Skoda cars that could let hackers track vehicles and control some features remotely — The vulnerabilities affect the infotainment system in the Skoda Superb III and could expose personal data like phone contacts. Skoda is addressing these issues through updates, ensuring customer safety is a priority.
🪳 💥 Improperly patched Cleo bug exploited in the wild — Cleo file transfer software is facing a serious vulnerability that allows hackers to execute code remotely, even on updated systems. Cybersecurity experts warn users to protect their software and ensure it is not exposed to the internet, as multiple businesses have already been compromised. A patch for the issue is expected to be released soon, but users should remain vigilant against ongoing attacks.
🤖 Microsoft has launched the LLMail-Inject Challenge to improve defenses against prompt injection attacks on an LLM-powered email client. Participants will act as attackers, trying to bypass security measures through crafted emails, with a total prize pool of $10,000. The competition runs from December 9, 2024, to January 20, 2025, and winners will present their findings at a conference.
🪳 🤖 Researchers have discovered security flaws in the DeepSeek AI chatbot that allow attackers to take control of user accounts through prompt injection attacks. These vulnerabilities could enable unauthorized code execution and session hijacking, leading to account takeovers. Similar issues have also been found in other AI tools, highlighting the need for developers to consider the risks of untrusted outputs.
ICS, OT & IoT
🇩🇪 🦠 Germany's cybersecurity agency has disrupted the BadBox malware found in over 30,000 Android IoT devices, which can steal data and install more malware. They have blocked the malware's communication with attackers by redirecting it to police-controlled servers. Device owners will be notified and should disconnect affected devices, as many are running outdated software and may remain vulnerable.
🇮🇷 A new malware named IOCONTROL, linked to Iranian threat actors, targets IoT and SCADA devices in the U.S. and Israel. It can control various devices, potentially shutting down services and stealing information. IOCONTROL represents a significant threat to critical infrastructure, using advanced techniques to evade detection.