[InfoSec MASHUP] 51/2024
McDonald's India Breached; More Cybercriminals Sentenced to Prison Time; Meta and Netflix Fined in Europe; Major Phishing Campaign in Europe; Israeli Spyware Company Bought by US Private Equity;
Welcome to the 4 new members from the last 30 days! This newsletter now has 1,607 subscribers.
Partners and Affiliates
🔐 NordVPN Christmas Campaign (Dec 10 - Jan 8) - Save up to 74% + 3 Extra Months!
Breaches & Security Incidents
46% of financial institutions had a data breach in the past 24 months
🇺🇸 BeyondTrust reported a cyberattack that compromised some of its Remote Support SaaS instances in early December 2024. Hackers gained access to an API key, allowing them to reset passwords for local application accounts. The company has since revoked the compromised key and applied security patches to protect their services.
🇮🇳 🍔 A major security flaw in McDonald's India delivery system exposed sensitive customer and driver data — The vulnerabilities allowed unauthorized access to personal information, including names, email addresses, and real-time location tracking. McDonald's India fixed these issues after being informed by a security researcher, but did not reveal how many customers were affected.
🔓 📊 A recent report shows that consumer trust in brands affected by data breaches has decreased slightly in 2024, but many still blame cybercriminals instead of recognizing their own role in security risks. While 66% of consumers would not trust a company after a breach, younger shoppers, like Generation Z, are more accepting of security incidents.
🇺🇸 Texas Tech University Health Sciences Center experienced a cyberattack that may have exposed the data of 1.4 million patients — The stolen information includes names, Social Security numbers, and medical details. A ransomware group called Interlock claimed responsibility for the breach and leaked a large amount of data online.
🇺🇸 Rhode Island's RIBridges system experienced a data breach due to a ransomware attack by the Brain Cipher group, exposing residents' personal information. Deloitte, which manages the system, confirmed that hackers likely stole sensitive data, including names and Social Security numbers. The system is currently offline, and affected residents will receive letters and guidance on protecting their information.
➝ More breaches:
ConnectOnCall breach exposes health data of over 910,000 patients
Ascension: Health data of 5.6 million stolen in ransomware attack
🔊 Interested in Reaching a Cybersecurity Audience?
Amplify your brand’s presence by sponsoring the InfoSec MASHUP newsletter!
Reach dedicated readers in the cybersecurity field with each issue! Contact us to explore sponsorship opportunities.
Cybercrime, Cyber Espionage, APT’s
North Korea-linked hackers accounted for 61% of all crypto stolen in 2024
🇺🇸 🇮🇱 ⚖️ An Israeli court will review a U.S. extradition request for Rostislav Panev, who is accused of being a developer for the LockBit ransomware gang. The U.S. claims that LockBit has caused over $500 million in losses and affected around 2,500 victims worldwide. Panev was arrested in August and allegedly earned $230,000 from his work with the group.
🇷🇴 ⚖️ Daniel Christian Hulea, a Romanian man involved in NetWalker ransomware attacks, was sentenced to 20 years in prison — He admitted to obtaining around 1,595 bitcoins from victims, totaling about $21.5 million. Hulea must also pay nearly $15 million in restitution and forfeit assets linked to his crimes.
🇺🇦 🇺🇸 ⚖️ Mark Sokolovsky, a Ukrainian national, was sentenced to five years in prison for running the Raccoon Stealer malware operation that stole sensitive data from millions of victims. He rented the malware to others for a fee, allowing them to commit cybercrimes more easily. After his arrest in 2022, Sokolovsky pleaded guilty and agreed to pay over $910,000 in restitution.
🇷🇺 APT29, a Russia-linked hacker group, is using a technique called "rogue RDP" to target high-profile victims like governments and researchers. They trick victims into opening malicious Remote Desktop Protocol (RDP) files, which give attackers control over their machines. This allows the hackers to steal sensitive data without deploying traditional malware, making their attacks harder to detect.
🇹🇷 A South Asian cyber espionage group called Bitter targeted a Turkish defense organization using two malware types, WmRAT and MiyaRAT, in November 2024. They delivered the malware through a RAR archive with hidden files that tricked victims into launching a malicious shortcut. This group has a history of attacks on various countries and aims to gather intelligence for government interests.
🎣 MUT-1244 is a threat actor targeting security researchers and academics to steal sensitive information using phishing emails and malicious GitHub repositories. Their attacks involve a payload called xmrdropper that updates a cryptocurrency miner and exfiltrates data from compromised systems. Researchers have warned that hundreds of victims have been affected by this ongoing campaign.
INTERPOL is urging a change in language from "pig butchering" to "romance baiting" to describe online scams that exploit victims through fake romantic relationships. They believe the new term is more respectful and focuses on the scammers rather than shaming the victims. This shift aims to encourage more victims to seek help and report these crimes.
Government, Politics, and Privacy
US considers banning TP-Link routers over cybersecurity risks
👀 🍏 Apple sends notifications to users who may be targeted by spyware, advising them to seek help from the nonprofit Access Now rather than conducting forensic investigations themselves. This approach has been praised by cybersecurity experts for improving accountability in spyware cases and helping at-risk individuals recognize threats. Apple also encourages users to activate Lockdown Mode for added security against potential spyware attacks.
🇨🇳 🇺🇸 China's cyber incident response center accused the U.S. of launching cyberattacks to steal trade secrets from Chinese tech companies. They reported two specific attacks, one targeting a materials research unit and another a high-tech energy enterprise, using vulnerabilities in their systems. This accusation comes amid ongoing tensions, with the U.S. also blaming China for cyber espionage.
🇪🇺 Apple and Meta are in conflict in Europe over the Digital Markets Act, which affects their access to each other's services. Apple claims that Meta's requests for interoperability could compromise user privacy and security. Meta argues that Apple's privacy concerns are unfounded and a tactic to limit access 🤷🏻♂️🤷🏻♂️
🇷🇺 Russia has banned the cybersecurity company Recorded Future, calling it an "undesirable" organization — The company is accused of working with the CIA and providing support to Ukraine against Russia. Recorded Future's CEO welcomed the designation, viewing it as a rare compliment.
🇳🇱 💰 Netflix has been fined €4.75 million by the Dutch data protection authority for not properly informing customers about their data usage. This penalty comes five years after a complaint was filed under the EU's General Data Protection Regulation (GDPR). Netflix plans to appeal the fine, and other complaints against streaming services like Amazon Prime and Apple Music are still pending.
🇮🇪 💰 Meta has been fined €251 million for a data breach in 2018 that affected 29 million Facebook accounts — The breach was caused by a bug that allowed unauthorized access to users' personal data. This is the second fine from the Irish Data Protection Commission, highlighting ongoing privacy violations by Meta.
🇺🇸 ☁️ CISA has ordered federal agencies to secure their Microsoft 365 cloud environments by following new security guidelines. Agencies must identify their cloud tenants, deploy assessment tools, and monitor their configurations to protect against cyber threats. While the current focus is on Microsoft 365, CISA plans to introduce similar guidelines for other platforms like Google Workspace in the future.
🇪🇺 🇷🇺 The European Union has imposed new sanctions on 16 individuals and three entities linked to Russia's destabilizing actions abroad — This marks a significant step in the EU's efforts to combat Russia's hybrid threats, including actions in Ukraine. The latest sanctions package also targets various organizations and individuals involved in spreading disinformation and supporting Russia's military operations.
🇮🇱 🇺🇸 Paragon, an Israeli spyware company, was bought by U.S. private equity firm AE Industrial Partners for $500 million, with potential earnings reaching $900 million. Founded by former Israeli intelligence officers, Paragon’s spyware is used to hack into phones and access apps like WhatsApp and Gmail. This acquisition follows a trend of Western investment in Israeli spyware firms, amid ongoing concerns about their impact on privacy and security.
👀 🇺🇸 The Department of Homeland Security (DHS) claims that China, Russia, Iran, and Israel are using security flaws in telecom networks to spy on people in the U.S. — These countries exploit a system called SS7 to track individuals and intercept their communications. The DHS has confirmed that all U.S. carriers are vulnerable to these types of surveillance attacks.
🕯️ 🇷🇸 Amnesty International's report reveals that Serbian police are using spyware called NoviSpy, along with phone-cracking technology, to surveil journalists and activists. One case highlighted is that of journalist Slaviša Milanov, who discovered his phone had been tampered with after police held him for questioning. The report raises concerns about digital surveillance and the potential misuse of technology against civil society in Serbia.
Partners and Affiliates
🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.
Malware & Threats
Attackers Exploit Microsoft Teams and AnyDesk to Deploy DarkGate Malware
🦠 🇰🇵 The Lazarus Group, linked to North Korea, has been targeting nuclear engineers with new malware called CookiePlus — This attack is part of a long-term cyber espionage campaign that uses fake job offers to deliver malware. The group has been improving its tactics to evade detection while increasing its cryptocurrency thefts significantly in 2024.
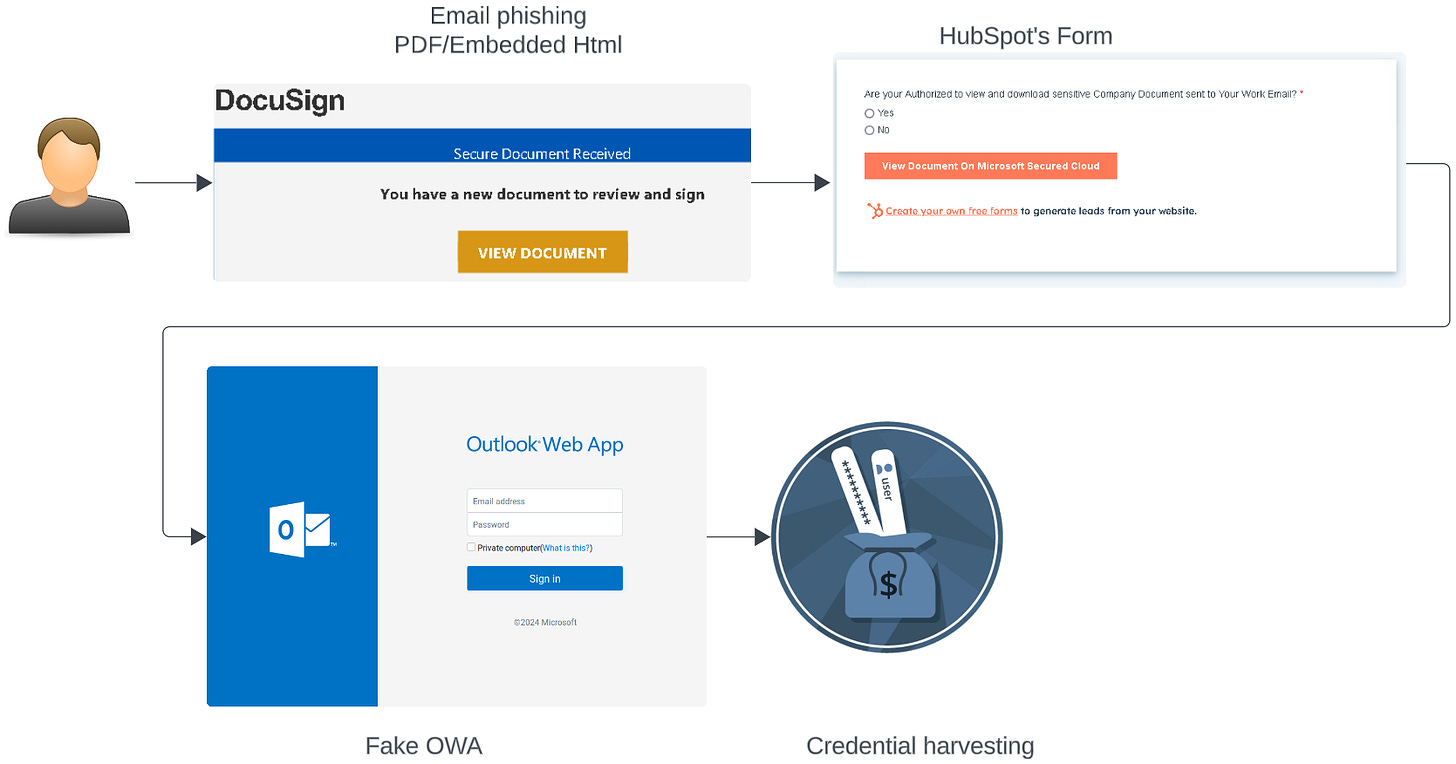
🎣 🇪🇺 A new phishing campaign named HubPhish is targeting over 20,000 European users to steal their Microsoft Azure credentials using HubSpot tools. Attackers send fake Docusign emails that redirect victims to malicious login pages to harvest their account information. Researchers warn that these types of phishing attacks are becoming more advanced by using legitimate services to bypass security measures.
🦠 📷 The FBI has warned about new HiatusRAT malware attacks targeting vulnerable web cameras and DVRs, especially those from Chinese brands. These attacks scan for security weaknesses and use tools to gain access to devices with weak passwords. The FBI advises protecting these devices and reporting any suspicious activity.
🦠 🇨🇳 Cybersecurity researchers discovered a new PHP backdoor named Glutton, linked to the Chinese APT group Winnti, which has been operating undetected for over a year. Glutton targets several countries and can exfiltrate data or inject malicious code into popular PHP frameworks. Despite some weaknesses, researchers believe Winnti is behind this malware, which aims to exploit the cybercrime market.
🦠 A large malvertising campaign called "DeceptionAds" spreads the Lumma Stealer malware through fake CAPTCHA pages, tricking users into running harmful PowerShell commands. This campaign uses the Monetag ad network to show deceptive ads on over 3,000 websites, targeting those who visit pirate streaming and software sites. To avoid infection, users should never execute commands from suspicious websites and be cautious of pirated software.
🦠 📺 Attackers are using a Node.js loader called NodeLoader to deliver malware disguised as game hacks through YouTube and Discord — When users download and run the malicious file, it can download additional malware that steals information and mines cryptocurrency. The use of Node.js makes detection by security software more difficult, as these files often have low antivirus detection rates.
AI, Crypto, Tech & Tools
Kali Linux 2024.4 released with 14 new tools, deprecates some features
🥷🏻 🤖 Researchers developed a machine learning algorithm that uses large language models (LLMs) to create new versions of malicious JavaScript, making them harder to detect. They improved their detection methods by retraining their model on these LLM-rewritten samples, which boosted detection rates by 10%. This approach highlights the challenge of preventing malicious actors from using LLMs to obfuscate existing malware.
Vulnerabilities, Research, and Threat Intelligence
BeyondTrust fixes critical vulnerability in remote access, support solutions (CVE-2024-12356)
Sophos Issues Hotfixes for Critical Firewall Flaws: Update to Prevent Exploitation
⚠️ Juniper Networks warns that Session Smart Router devices with default passwords are being attacked by the Mirai botnet — This malware can use infected devices to launch DDoS attacks on other systems. To protect against these threats, users should change their passwords, monitor for suspicious activity, and keep their software updated.
⚠️ Fortinet has warned about a critical security flaw in its Wireless LAN Manager (FortiWLM) that could allow attackers to access sensitive information. The vulnerability, known as CVE-2023-34990, has a high severity score and can enable unauthorized users to read log files and potentially gain administrative access. Users are urged to update their FortiWLM versions to protect against this and other related vulnerabilities.
🪳 🔓 A critical vulnerability in Apache Struts, known as CVE-2024-53677, allows attackers to upload malicious files and execute remote commands on vulnerable servers. Exploitation attempts are actively happening using public proof-of-concept code, prompting cybersecurity agencies to issue urgent alerts. Users are advised to upgrade to Struts 6.4.0 or later and change their file upload mechanisms to protect against this flaw.
🪳 🔓 Over 25,000 SonicWall VPN firewalls are exposed to serious security flaws, with many using outdated firmware no longer supported by the vendor. Cybersecurity firm Bishop Fox found that these vulnerabilities have been targeted by ransomware groups to access corporate networks. Despite improvements in patch adoption, a significant number of devices remain vulnerable to attacks.
🪳 🔓 Antonio Morales discovered 29 new vulnerabilities in the GStreamer library, mainly in the MKV and MP4 formats — He created a unique input corpus generator to effectively test these formats, as traditional methods were limited due to the large size of multimedia files. This approach allowed him to identify previously undetected vulnerabilities in the MP4 and MKV parsers.
🪳 🔓 Palo Alto Unit 42 researchers found serious security vulnerabilities in the Azure Data Factory's Apache Airflow integration, allowing attackers to gain shadow admin control. Exploiting these flaws could lead to data theft, malware deployment, and manipulation of Azure's internal services. The researchers reported these issues to Azure, highlighting misconfigured permissions and weak authentication as key problems.