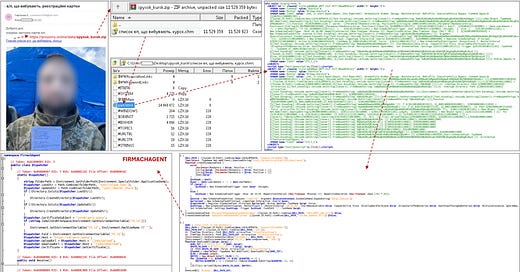
[InfoSec MASHUP] Week 34/2024
Meta has shut down CrowdTangle; National Public Data Published Its Own Passwords; QNAP adds NAS ransomware protection; Data Exfiltration from Slack AI; Azure Kubernetes Services Vuln. Exposed;
Welcome to the 27 new members from the last 30 days! This newsletter now has 1,503 subscribers.
Keep reading with a 7-day free trial
Subscribe to X’s InfoSec Newsletter to keep reading this post and get 7 days of free access to the full post archives.