We’ve Moved! 🚀
Exciting changes ahead! We’ve officially moved from Substack to beehiiv to bring you an even better reading experience. Expect the same great content—just with a sleeker design, faster delivery, and new features to enhance your experience. If you're receiving this, you're already on board! Thanks for sticking with us—big things ahead! 🎉
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
🇬🇧 🇺🇸 A cybersecurity journalist refused to remove articles about a ransomware attack on U.K. healthcare firm HCRG, despite a court order demanding it. The journalist argues that they are not subject to U.K. law and that their reporting is protected under U.S. free speech rights. HCRG confirmed the cyberattack and is investigating the incident, but has not provided full details to the public.
🇨🇦 🐒 The Toronto Zoo has updated information about a ransomware attack that occurred in January 2024, revealing that personal and financial data of employees, volunteers, and donors was stolen. The Akira ransomware group claimed responsibility for the breach and leaked over 35GB of data on the dark web, including names, addresses, and credit card details. The zoo has reported the incident and is advising affected individuals to monitor their financial accounts for suspicious activity.
🇮🇳 The Hunters International ransomware gang has claimed responsibility for a January cyberattack on Tata Technologies, stealing 1.4TB of data. Tata Technologies, which provides engineering solutions globally, reported minimal impact on its operations and is working to restore its IT systems. The gang threatens to release the stolen files unless a ransom is paid within a week.

Tata Technologies listed on Hunters International extortion page/BleepingComputer.com
🇵🇱 The Polish space agency (POLSA) disconnected its network from the internet after a cyberattack over the weekend. The agency is investigating the incident and has reported it to the authorities. There are concerns that the attack could be linked to ransomware or a nation-state threat due to Poland's support for Ukraine.
🇮🇳 Indian stock brokerage firm Angel One reported a data breach affecting client information stored in its Amazon Web Services account. The breach was discovered after a dark web alert, and the company has since changed passwords and hired experts to investigate. Angel One assured clients that their securities and funds are secure, but the incident caused the company's shares to drop over 11%.
➝ More:
🔗 Partners and Affiliates
🔐 NordVPN Birthday Campaign 🎉 (February 5 – March 19)
Special Birthday Offer: up to 73% off on 2-year plans + 6 months free purchasing Ultra, Ultimate, Complete, Plus, Standard plans.
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
🇺🇸 🇷🇺 The U.S. Secret Service has seized the website of Garantex, a Russian cryptocurrency exchange linked to illegal activities. This action is part of ongoing sanctions against the exchange, which was previously accused of handling over $100 million in transactions tied to criminal organizations. Following the seizure, Garantex announced it was suspending all services, including cryptocurrency withdrawals.
🎤 Two employees from a third-party contractor for StubHub stole $635,000 by intercepting concert ticket orders. Most of the stolen tickets were for Taylor Swift's Eras Tour, but they also targeted other major events. The defendants face serious charges and could get 3 to 15 years in prison if convicted.
🇺🇸 ⚖️ The U.S. Justice Department has indicted 12 Chinese nationals for their alleged role in extensive cyber espionage attacks on U.S. agencies, including the Treasury Department. These individuals, linked to China's Ministry of Public Security and a hacking group, are accused of stealing and selling data to the Chinese government. The U.S. is offering rewards for information about these suspects and has imposed sanctions on some of them.
🇺🇸 ⚖️ The U.S. Treasury Department has sanctioned an Iranian man named Behrouz Parsarad, who ran the Nemesis darknet marketplace used for drug trafficking and cybercrime. The marketplace was shut down in March 2024, with over 150,000 user accounts involved. Parsarad allegedly made millions from transaction fees and is reportedly planning to create a new darknet site.
🇻🇪 🇺🇸 Two Venezuelans were arrested in the US for hacking ATMs and stealing over $110,000. They used malware to control the machines and withdrew cash without needing bank account information. The suspects face serious charges and could spend up to 10 years in prison.
🇹🇭 A hacker known by several names, including ALTDOS and DESORDEN, has been arrested in Thailand. He is of hacking over 50 companies worldwide and extorting them for stolen data. Law enforcement in Thailand and Singapore worked together to capture him and seize valuable items during the raid.
🇨🇳 Microsoft Threat Intelligence identified a shift in tactics by the Silk Typhoon hacking group, linked to China, who is now targeting IT supply chains to gain access to corporate networks. They exploit security flaws in various software and use stolen credentials to infiltrate systems for espionage.
💰 BTC > ETH? The cybercriminals who stole $1.4 billion in cryptocurrency from Bybit have moved most of it into Bitcoin. Experts believe the North Korean government is behind the hack, which is the largest in history. The hackers are using mixers to obscure the funds' origins, making it harder for investigators to trace them.
📮 Ransomware extortionists are now sending physical letters to company executives, demanding ransoms without hacking their systems. These letters claim to be from the BinLian group, asking for payments in Bitcoin and including a QR code. So far, no recipients have fallen for these fake demands, and experts advise reporting them to the authorities instead of responding.
⚖️ Oleg Nefedov, the alleged leader of the Black Basta ransomware group, escaped from court while awaiting a detention decision. He had been arrested on June 21, 2024, but managed to flee during a walk outside the courthouse. Nefedov left in a vehicle despite the presence of police and court officials.
🇷🇺 Kaspersky, huh? Prospero OOO, a notorious provider of bulletproof web hosting for cybercriminals, has begun routing its operations through Kaspersky Lab's networks. Security experts warn that this connection could enable further malicious activities, as Prospero has a history of hosting malware and ransomware groups. Kaspersky's involvement raises concerns about the security implications of supporting such a service.
🇺🇸 💰 U.S. authorities recovered $31 million in cryptocurrency stolen from the Uranium Finance platform during two cyberattacks in April 2021. The attacks exploited vulnerabilities, resulting in over $53 million in losses for investors. Victims can email authorities to claim a portion of the recovered funds.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests. Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
🇬🇧 The U.K. government has removed encryption advice from its websites after asking Apple for backdoor access to encrypted iCloud data. The National Cyber Security Centre no longer recommends encryption for high-risk individuals and suggests using Apple's Lockdown Mode instead. This change follows Apple's decision to pull its Advanced Data Protection feature from the U.K. due to the government's demands.
🇪🇸 ⚖️ A Barcelona court has decided that NSO Group executives can be charged in a spyware investigation linked to the hacking of a lawyer. The ruling came after a human rights nonprofit, Iridia, appealed a previous decision to not charge the executives. This decision is seen as a significant step in holding individuals accountable for spyware activities in Europe.
🇺🇸 🇺🇦 The CIA director announced that the Trump administration has paused sharing intelligence with Ukraine after a disagreement between President Trump and Ukrainian President Zelenskyy. This pause raises concerns about Ukraine's ability to defend itself against Russian attacks. The CIA director believes this pause will eventually end.
🇺🇸 The House has passed a bill that requires federal contractors to implement vulnerability disclosure policies to improve cybersecurity. This legislation aims to protect sensitive information by ensuring contractors follow guidelines set by the National Institute of Standards and Technology. The bill has support from various tech companies and is seen as a crucial step in defending against cyber threats.
🇬🇧 The UK Information Commissioner's Office is investigating TikTok, Reddit, and Imgur regarding how they handle children's personal information. The focus is on protecting the privacy of users aged 13-17 and ensuring they are not exposed to harmful content. These investigations aim to enforce data protection laws and improve online safety for children.
🔗 Partners and Affiliates
🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.

🦠 MALWARE & THREATS
📮 Fake. Sort of — The FBI warns that scammers are pretending to be the BianLian ransomware gang by sending fake ransom notes to U.S. executives. These notes claim hackers have stolen sensitive data and demand ransoms between $250,000 and $500,000. The FBI has not linked the scammers to the actual BianLian group and reports that many letters have targeted healthcare executives.
🇦🇪 Are you Polyglot? Proofpoint discovered a targeted email campaign delivering advanced malware to a few aviation and transportation organizations in the UAE. The malware, called Sosano, utilized complex techniques to hide its presence and was delivered via compromised emails from a trusted source. This incident highlights the risks of supply chain compromises and the need for organizations to be cautious of unexpected emails, even from known contacts.
🕸️ A new DDoS botnet called Eleven11bot has been discovered, affecting around 86,400 hacked devices, including many in the U.S., U.K., Canada, and Australia. It has been launching intense attacks on gaming and communication services, sometimes sending hundreds of millions of packets per second. The botnet grows by exploiting weak passwords and targeting exposed network ports.
📨 Black Basta and Cactus ransomware groups are using a new malware called BackConnect to maintain control over compromised systems. They employ social engineering and legitimate tools like Microsoft Teams and OneDrive to trick victims into granting access. Since October 2024, most attacks have occurred in North America, particularly affecting manufacturing and financial sectors.
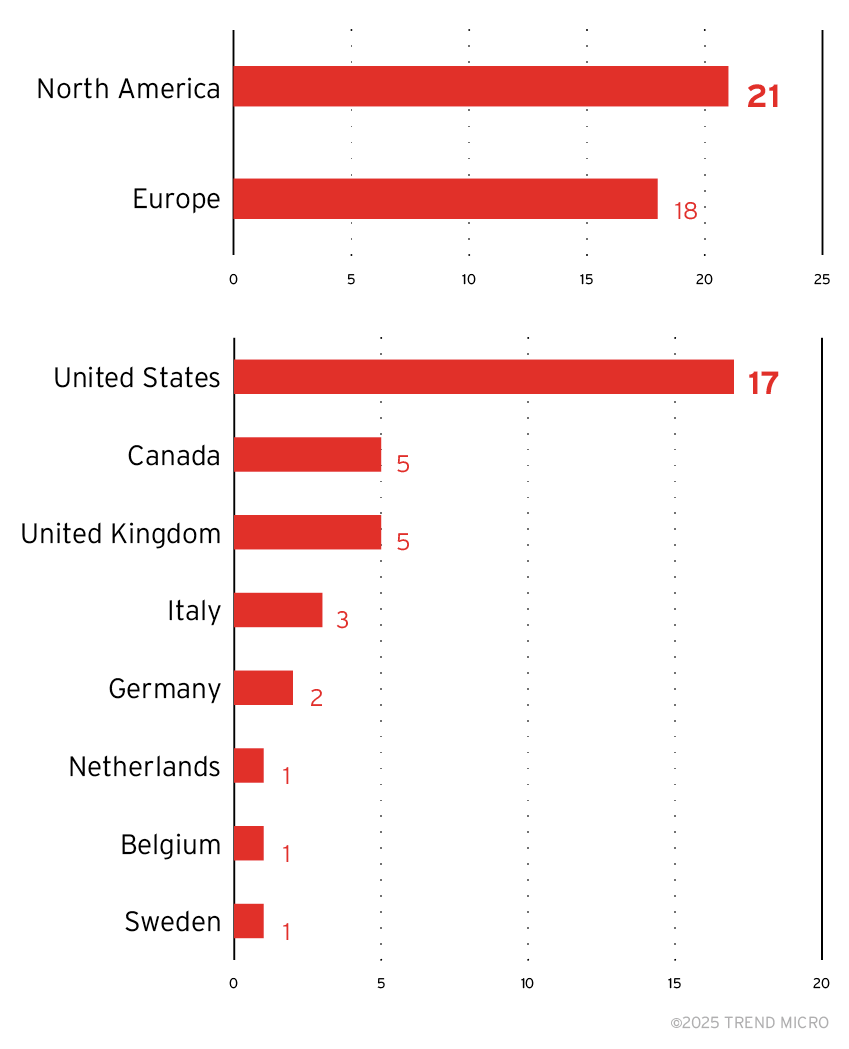
Black Basta’s targeted regions (top) and countries (bottom) since October 2024, based on Trend Micro Threat Intelligence
🐧 🍎 Researchers have found malicious Go packages that impersonate popular libraries and install malware on Linux and macOS systems. At least seven typosquatted packages have been identified, using similar obfuscation techniques to hide their harmful functions. Developers are advised to be vigilant and use real-time scanning tools to protect against these threats.
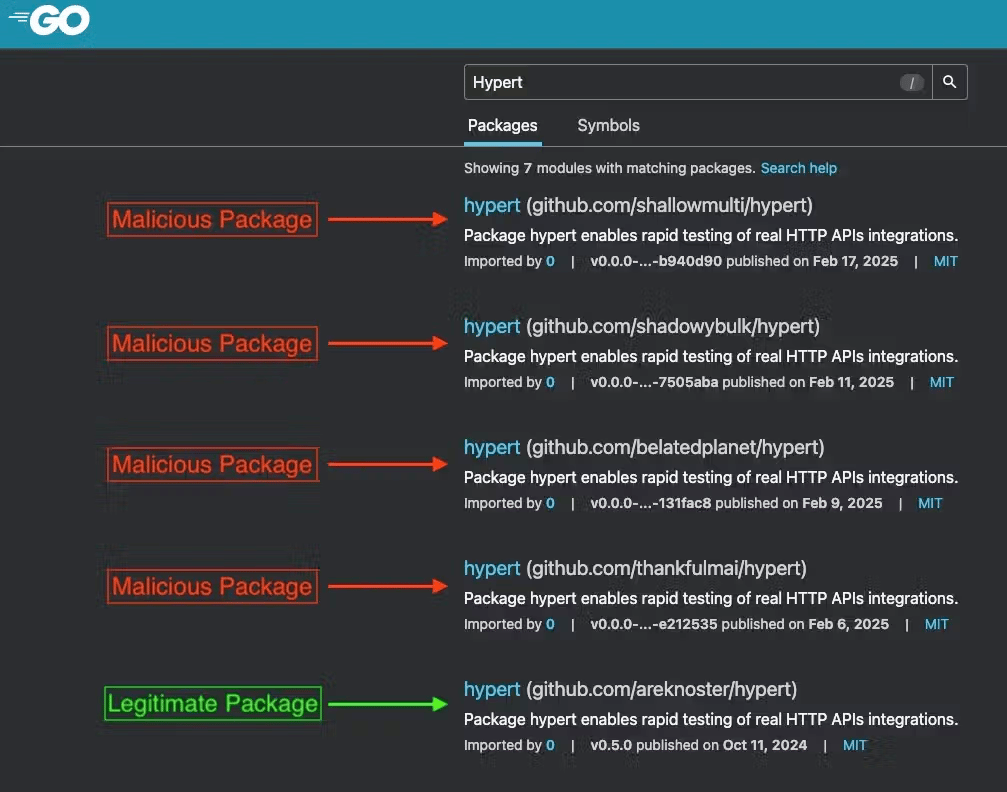
A search on the Go Module Mirror shows multiple malicious “hypert” packages (highlighted in red), all appearing above the legitimate “hypert” library (green) from github.com/areknoster/hypert
🇮🇷 Iranian hackers targeted a few organizations in the U.A.E. aviation sector using a compromised email from an Indian firm, INDIC Electronics. They sent phishing emails containing malicious files that installed a backdoor called Sosano, allowing further control over the victims' systems.
📝 Insightful article from Palo Alto Unit42 discussing how malware authors use advanced obfuscation techniques, like AES encryption and code virtualization, to hide their malicious code and evade detection. These techniques allow malware, such as Agent Tesla and XWorm, to be distributed more effectively while complicating analysis by security tools.
💰 Hackers are exploiting a vulnerability in the Paragon Partition Manager driver to carry out ransomware attacks. This security flaw allows attackers to gain higher privileges and run malicious code on affected systems. Paragon Software has released an updated driver to fix these issues, and Microsoft has added the vulnerable version to its blocklist.
🤖 🧰 AI, CRYPTO, TECH & TOOLS
📺 Deepfake — YouTube warning users about an AI-generated phishing video of their CEO announcing changes in monetization.
📱 Cellebrite has added AI features to its forensic tools, allowing law enforcement to summarize chat logs and audio from seized phones. This has raised concerns among civil liberties experts about the transparency and accuracy of AI-generated evidence. Critics worry that AI may lead to incomplete or misleading conclusions in criminal investigations.
🇮🇳 India's Enforcement Directorate has chosen CoinDCX to manage the custody of seized cryptocurrencies during investigations. CoinDCX has set up a specialized team with advanced security measures for this role. Despite regulatory challenges, India's crypto market is expected to grow significantly in the coming years.
☎️ Google new AI-powered features to detect scams on Android devices
🔗 Partners and Affiliates
⚡️ Unlock Your Peak Performance – First Month FREE!
Optimize your sleep, recovery, and performance with WHOOP. Perfect for cybersecurity pros who need to stay focused and ahead of the threat. Try it out, get a free WHOOP 4.0 and one month free.
🪳 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
🚨 Broadcom has alerted customers about three VMware zero-day vulnerabilities that are being actively exploited in attacks. These flaws allow attackers with admin access to escape the virtual machine's sandbox and compromise the hypervisor. VMware products, often targeted by hackers, include ESXi, vSphere, and Workstation, making these vulnerabilities a significant risk for enterprises.
🪳 Microcode — Google has released the full details of EntrySign, the AMD Zen microcode signature validation vulnerability which they initially disclosed last month.
🇨🇳 The Great Firewall of China is Bleeding — The paper titled "Wallbleed: A Memory Disclosure Vulnerability in the Great Firewall of China" uncovers a critical flaw in China's internet censorship infrastructure, specifically within its DNS injection subsystem.
🪳 📱 A new vulnerability called EvilLoader in Telegram for Android allows attackers to disguise harmful APKs as video files, leading to unauthorized installations. This exploit remains unpatched in the latest version of Telegram and has been sold on underground forums since January 2025. Users are advised to be cautious and avoid opening files from unknown sources until a fix is released.
🩹 Google's March security update for Android fixed 43 vulnerabilities, including two that are actively exploited. The most severe flaw, CVE-2024-43093, allows attackers to gain privileges with user interaction and has a high severity score. Pixel users will receive these updates soon, while other manufacturers may take longer to release their patches.
📝 2024 Malicious Infrastructure Report: In 2024, Insikt Group expanded its tracking of malicious infrastructure, identifying trends such as the rise of malware-as-a-service infostealers like LummaC2. The report highlights that the US and China remain top hosting locations for cybercrime, while AsyncRAT is the most prevalent malware affecting victims globally. Law enforcement actions are expected to improve in effectiveness, aided by better international cooperation and experience.
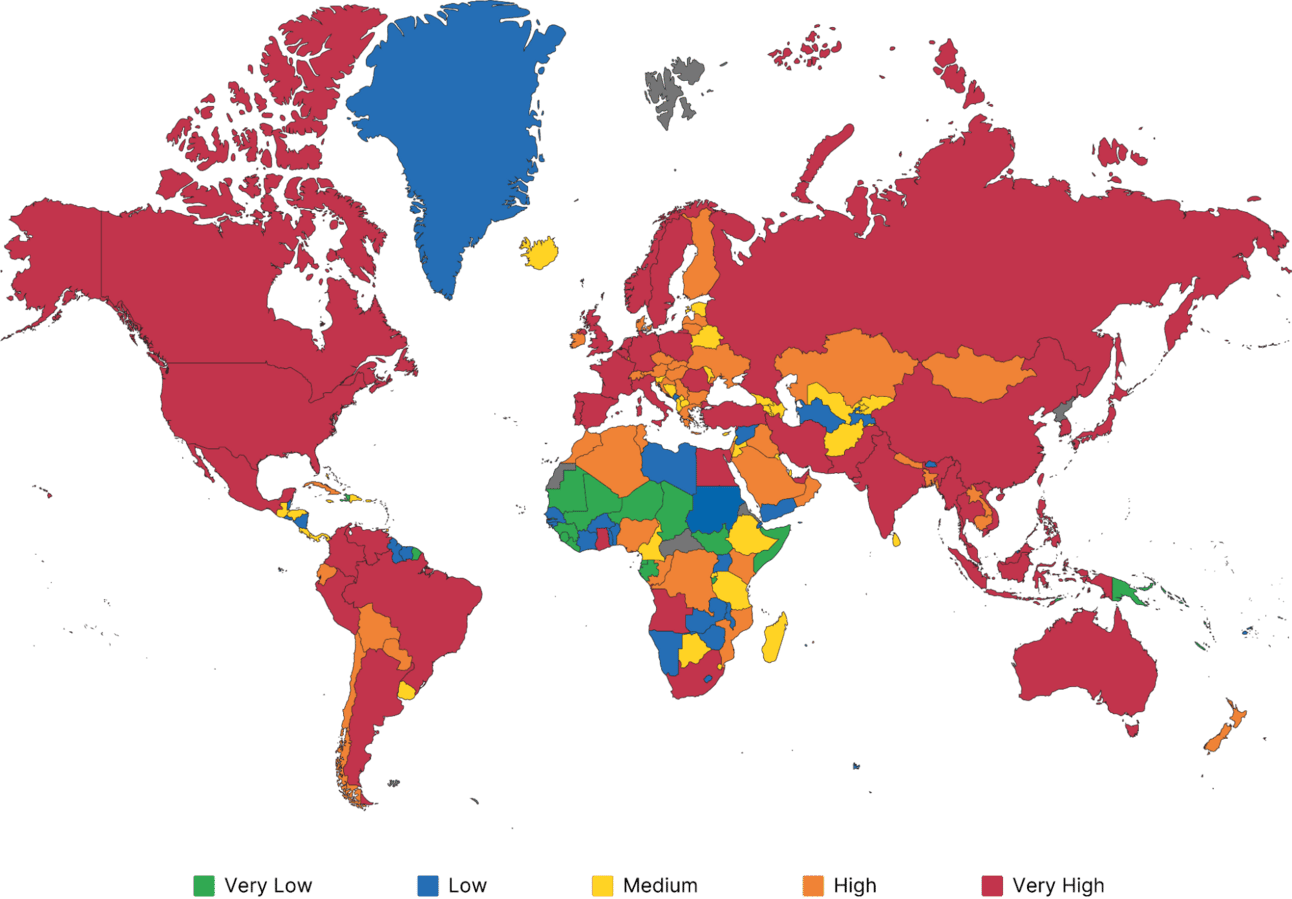
Malware impact by country based on Recorded Future Network Intelligence/RecordedFuture.com
🛰️ ICS, OT & IoT
🪳 A security assessment of the ICONICS Suite SCADA system revealed five high-risk vulnerabilities in versions 10.97.2 and earlier. These vulnerabilities could allow attackers to execute malicious code and gain elevated privileges, posing risks to critical infrastructure sectors. ICONICS has released security patches and advisories to address these issues.
📝 The 2025 ICS/OT Cybersecurity Budget Report — A new report shows that while many organizations are increasing their ICS/OT cybersecurity budgets, key areas like network visibility and secure remote access remain underfunded. Over a quarter of surveyed companies faced security incidents in the past year, often starting from compromised IT environments. Despite budget increases, only a small percentage of staff fully focus on ICS/OT security, highlighting ongoing challenges in protecting critical infrastructure.
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.