We’ve Moved! 🚀
Exciting changes ahead! We’ve officially moved from Substack to Beehiiv to bring you an even better reading experience. Expect the same great content—just with a sleeker design, faster delivery, and new features to enhance your experience. If you're receiving this, you're already on board! Thanks for sticking with us—big things ahead! 🎉
Table of Contents
🔓 BREACHES & SECURITY INCIDENTS
📝 In-Depth Technical Analysis of the Bybit Hack: Attackers exploited vulnerabilities in the Safe{Wallet} web interface to trick Bybit's signers into approving a fraudulent transaction, leading to significant fund loss. By modifying the transaction details they saw, the attackers managed to gain control of the cold wallet without directly breaching the multi-signature security. This incident highlights the need for better security controls and practices to verify transaction data before approval.

Off-Chain Attack Diagram/nccgroup.com
🇮🇳 A ransomware group called Hunters International has leaked data from Tata Technologies, following a ransomware attack on the company. The leaked information includes personal details of employees and confidential company documents, totaling over 730,000 files. Tata Technologies has not confirmed if this data is related to the attack they disclosed earlier this year.
🇺🇸 ⚖️ New York is suing Allstate and its subsidiaries for two data breaches that exposed sensitive information of nearly 200,000 people. The lawsuit claims that National General, which Allstate acquired, failed to notify customers about compromised driver’s license numbers. The state is holding insurance companies accountable for poor data security practices following similar cases with other insurers.
🇺🇸 What PowerSchool Won’t Say: A hacker gained access to PowerSchool's network months before a major data breach in December, according to a report by CrowdStrike. The compromised credentials allowed unauthorized activity from August to September 2024, raising concerns about the security of customer information. The breach, which was disclosed in December 2024, has left many questions unanswered about the scale of the incident and the types of data stolen. Despite confirming the breach, PowerSchool has not disclosed how many individuals are impacted or whether they paid a ransom to the hackers.
🇺🇸 Over 560,000 people were affected by four recent healthcare data breaches involving organizations like Sunflower Medical Group and Hillcrest Convalescent Center. The breaches exposed sensitive information such as Social Security numbers and medical data, with the Rhysida and BianLian ransomware groups claiming responsibility. In total, 720 healthcare data breaches were reported in 2024, impacting 186 million user records.
😳 🇷🇺 Face-to-face: Russian crypto exchange Garantex is facing trouble after Tether blocked access to its wallets and U.S. law enforcement seized its websites. The U.S. Justice Department charged two Garantex administrators with money laundering. In response, Garantex is inviting customers with positive account balances to face-to-face meetings in Moscow to discuss their blocked assets.
🔗 Partners and Affiliates
🔐 NordVPN Birthday Campaign 🎉 (February 5 – March 19)
Special Birthday Offer: up to 73% off on 2-year plans + 6 months free purchasing Ultra, Ultimate, Complete, Plus, Standard plans.
🥷🏻 CYBERCRIME, CYBER ESPIONAGE, APT’s
A new ransomware called SuperBlack is being used by a group named Mora_001, exploiting two Fortinet vulnerabilities to gain access to firewalls. They first gain admin privileges, steal data, and then encrypt files for ransom while trying to erase evidence of their attack. There are strong links between SuperBlack and the LockBit ransomware group, suggesting a connection between the two.

Key characteristics of the newly identified Mora_001 threat actor exploiting CVE-2024-55591 and CVE-2025-24472/Forescout.com
🇮🇱 🇺🇸 A LockBit ransomware developer named Rostislav Panev has been extradited to the US from Israel. He is accused of helping to create malware that has targeted over 2,500 organizations worldwide. The US Justice Department charges that he earned over $230,000 for his work in cybercrime.
🚢 The SideWinder APT group is targeting maritime, nuclear, and IT sectors across Asia, the Middle East, and Africa. They use advanced techniques, including spear-phishing emails and malware, to infiltrate organizations and steal sensitive information. The group's activities have expanded to include diplomatic entities in several countries, showing their growing threat.
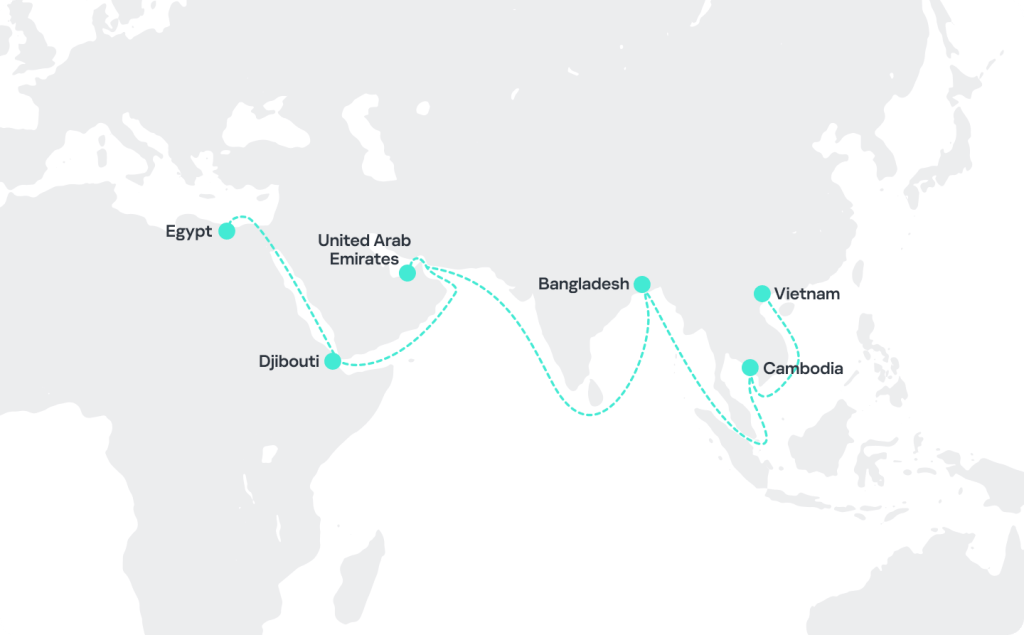
Countries and territories targeted by SideWinder in the maritime and logistics sectors in 2024/securelist.com
🇺🇸 The FTC will distribute $25.5 million in refunds to over 736,000 people misled by tech support scams from Restoro and Reimage. These companies used fake pop-ups and ads to trick consumers into paying for unnecessary computer repairs. Eligible recipients will receive an email and must claim their PayPal payment within 30 days starting March 13.
❌ No, it’s not (necessarily) Ukraine: The hacktivist group Dark Storm claims responsibility for DDoS attacks causing outages on X.
🗓️ {Cyber,Info}Sec Events: My list of past and future {cyber,info}sec related events — Feel free to contribute by submitting issues or pull requests. Thanks! 😉
👨🏻⚖️ 👀 GOVERNMENT, POLITICS, AND PRIVACY
👀 Amazon is still hosting private data from three stalkerware apps, Cocospy, Spyic, and Spyzie, despite being notified about the breach weeks ago. TechCrunch found that these apps are storing stolen phone data on Amazon's cloud servers, affecting around 3.1 million victims. Amazon has not confirmed if it will take action against these apps, citing procedural issues instead.
🇺🇸 Spying Government: A contractor for Immigration and Customs Enforcement (ICE) and many other U.S. government agencies has developed a tool, called ShadowDragon, used to gather publicly available data from over 200 websites, including social media and payment platforms. This tool allows government agencies to track individuals' activities and connections online. More at 404media.
🇺🇸 Elon Musk's Department of Government Efficiency (DOGE) has laid off over 100 employees from the U.S. cybersecurity agency CISA, including members of its "red team." The cuts, which occurred without warning, are part of ongoing reductions in federal cybersecurity staff since the Trump administration began. Affected employees are now seeking new jobs, expressing concern about the future of government cybersecurity efforts.
🇺🇸 President Trump nominated Sean Plankey to lead the Cybersecurity and Infrastructure Security Agency (CISA). Plankey has extensive experience in cybersecurity, including roles in the Energy Department and the National Security Council. His nomination will be reviewed by the Senate Homeland Security Committee.
🇨🇭 Switzerland's National Cybersecurity Centre has introduced a new rule requiring critical infrastructure organizations to report cyberattacks within 24 hours. This rule, effective from April 1, 2025, aims to address the rising number of cybersecurity incidents. Organizations that fail to comply after a leniency period may face fines of up to CHF 100,000.
🔗 Partners and Affiliates
🌐 Stay connected and secure on the go with Airalo's global eSIMs — Use the code NEWTOAIRALO15 if you’re new to Airalo to get an additional 15% discount.

🦠 MALWARE & THREATS
👻 Ghost in the Router: Mandiant discovered that a Chinese espionage group, UNC3886, targeted Juniper routers by deploying custom malware known as TINYSHELL. This malware includes backdoors that can disable logging and communicate with command and control servers, allowing the attackers to control the devices. UNC3886's tactics show a sophisticated understanding of network device vulnerabilities, enabling them to bypass security protections.
🇰🇵 Six malicious npm packages linked to the North Korean Lazarus hacking group have been found, designed to steal sensitive information and deploy malware. These packages trick developers through typosquatting, mimicking popular libraries to gain access to credentials and cryptocurrency wallets. Developers are urged to carefully check the packages they use to avoid compromising their systems.
💸 A new malware called MassJacker has been found stealing cryptocurrency by hijacking clipboard data from infected computers. It uses over 778,000 wallet addresses and has already amassed significant funds, including a single wallet with over $300,000. This malware operates by replacing legitimate wallet addresses with those controlled by attackers, tricking victims into sending money to them.
🇮🇹 🕸️ A new IoT botnet called Ballista targets TP-Link Archer routers by exploiting a known vulnerability. It is linked to an Italian threat actor and has attacked organizations in multiple countries. The botnet downloads malware to compromised devices, allowing attackers to control them and launch various attacks. A Censys search shows more than 6,000 internet-exposed devices that could be vulnerable to attacks.
🇨🇴 A South American cyberespionage group called Blind Eagle has infected over 1,600 victims in Colombia with malware. They primarily use phishing emails to deliver remote access trojans and have recently targeted a Microsoft vulnerability. Their attacks have affected many public and private organizations, showing their persistent threat in the region.
🎣 A phishing email campaign is tricking people into downloading malware by offering free TRUMP Coins, using a fake Binance logo to appear legitimate. Victims who download the software unknowingly install ConnectWise RAT, allowing attackers to take control of their computers. The campaign exploits the popularity of meme coins and aims to deceive users into completing “trading tasks” for fake rewards.
🤖 🧰 AI, CRYPTO, TECH & TOOLS
🔓 Microsoft researchers have created a new jailbreak method called Context Compliance Attack (CCA) that can bypass safety measures in most AI systems. This method tricks AI models into following manipulated conversation histories, allowing them to produce restricted outputs. The researchers suggest that improving server-side history maintenance and using digital signatures can help defend against such attacks.
🇨🇳 🇺🇸 OpenAI has labeled the Chinese AI lab DeepSeek as "state-controlled" and suggests banning its models due to security risks. They argue that DeepSeek must comply with Chinese laws that could compromise user data privacy. The relationship between DeepSeek and the Chinese government is unclear, but interest in the lab has grown in recent months.
🦠 Researchers at Tenable tested the Chinese AI DeepSeek's ability to generate malware like keyloggers and ransomware. Although DeepSeek has built-in protections against creating harmful code, these can be bypassed using jailbreak methods. The AI can create basic malware structures, but it requires manual edits and additional prompts to function effectively.
💬 A new paper discusses the relationship between AI and end-to-end encryption, raising important privacy questions. As AI technology advances, it may require access to users' private data, potentially compromising the security of encrypted messaging. While some companies are working to improve privacy protections, there are ongoing debates about laws that could mandate scanning of encrypted messages.
🇸🇬 A Singapore judge has granted bail to three men accused of smuggling Nvidia chips worth $390 million, allegedly defrauding suppliers by misrepresenting the servers' locations. The bail amounts are set at $600,000 to $1 million, with conditions that include electronic monitoring for one suspect. The case highlights concerns over the export of technology to China amid ongoing restrictions.
➝ Useful Links:
🔗 Partners and Affiliates
⚡️ Unlock Your Peak Performance – First Month FREE!
Optimize your sleep, recovery, and performance with WHOOP. Perfect for cybersecurity pros who need to stay focused and ahead of the threat. Try it out, get a free WHOOP 4.0 and one month free.
🪳 🧠 VULNERABILITIES, RESEARCH, AND THREAT INTELLIGENCE
➝ From the Patching Department:
🪳 Back to 2017: GitHub has found two serious vulnerabilities (CVE-2025-25291 + CVE-2025-25292) in the ruby-saml library that could let attackers bypass authentication and take over accounts. These flaws allow an attacker to create fake login credentials if they have a valid signature. Users are urged to update to the latest versions to protect against these security risks.
🩹 CVE-2025-21590: Juniper Networks has released emergency updates to fix a security flaw in their routers that was exploited by Chinese hackers to gain unauthorized access. The vulnerability affects multiple Juniper device series and allows attackers to execute arbitrary code. The U.S. cybersecurity agency has ordered agencies to secure affected devices by April 3rd due to the risk posed by this flaw.
🇬🇧 The Princess Alexandra Hospital NHS Trust discovered 5,000 to 10,000 unknown devices connected to its network, increasing its cybersecurity risks. Deputy director Jeffery Wood emphasized the need for better visibility and faster response to cyber threats, as the hospital relies on technology while managing security challenges. Among the many unexpected items discovered to be connecting to The Princess Alexandra Hospital NHS Trust’s (PAHT) networks were PlayStations, coffee machines and passing electric vehicles.
🪳 Meta has warned of a serious vulnerability in the FreeType font library, identified as CVE-2025-27363, which may be actively exploited. This flaw could allow remote code execution when processing certain font files, affecting FreeType versions 2.13.0 and below. Users are advised to update to version 2.13.3 to protect against potential attacks.
🪳 💥 A critical vulnerability in PHP, tracked as CVE-2024-4577, is being widely exploited, allowing attackers to execute code on vulnerable servers. This flaw affects Windows servers running Apache and PHP-CGI, and has led to malicious campaigns targeting various sectors, especially in Japan. Users are urged to update their PHP installations to the latest versions to protect against these attacks.

Daily observed exploitation attempts for CVE-2024-4577/GreyNoise Global Observation Grid
🪳 A new vulnerability, CVE-2024-9956, allows attackers within Bluetooth range to take over PassKeys accounts on mobile browsers by tricking users into authenticating through a malicious page. This exploit undermines the assumption that PassKeys are secure against phishing attacks, as attackers can initiate legitimate authentication requests. The issue affects major browsers like Safari, Chrome, and Firefox, making it a significant security concern.

Diagram of how those steps would look like/mastersplinter.work
🛰️ ICS, OT & IoT
Investigating Industrial Control Systems - Antti Rössi (from the Finnish National Cyber Security Center), a deep dive into what is wrong with ICS today, what attackers need to do to succeed.
🇨🇳 🇺🇸 Chinese hackers known as Volt Typhoon infiltrated a Massachusetts power utility for over 300 days, gathering sensitive operational data. The breach was discovered in November 2023, while the utility was enhancing its cybersecurity measures. Experts warn that the stolen information could be used for future attacks on critical infrastructure.
🩹 ICS Patch Tuesday: Siemens and Schneider Electric released security updates for their products, addressing critical vulnerabilities that could allow attackers to execute commands or take control of systems. CISA also published advisories on vulnerabilities in Optigo Networks tools and a Schneider Electric driver. These updates are part of the March 2025 Patch Tuesday.
🛜 Researchers found an undocumented backdoor in the widely used ESP32 Bluetooth chip, which could allow attackers to take control of devices and access sensitive data. This backdoor includes 29 hidden commands that can manipulate memory and spoof device identities. The discovery raises significant security concerns, especially since the ESP32 is used in over a billion IoT devices.
💬 CONNECT
Follow me on Mastodon for quick daily updates and bite-sized content.
Prefer using an RSS feed? Add Infosec MASHUP to your feed here.
Thanks for reading today’s newsletter, and if you're enjoying it and want to support my work, you can buy me a coffee ☕ over at https://www.buymeacoffee.com/0x58
See you next time!
-X.






